Tool updates: le-hex-to-ip.py and sigs.py
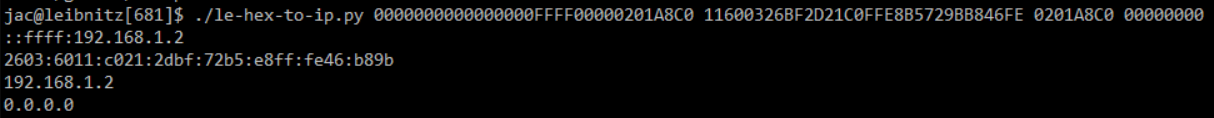
I am TA-ing for Taz for the new SANS FOR577 class again and I figured it was time to release some fixes to my le-hex-to-ip.py script that I wrote up last fall while doing the same. I still plan to make some additional updates to the script to be able to take the hex strings from stdin, but in the meantime, figured I should release this fix. I was already using Python3's inet_ntoa() function to convert the IPv4 address, so I simplified the script by using the inet_ntop() function since it can handle both the IPv4 and IPv6 addresses instead of my kludgy handling of the IPv6. As a side-effect it also quite nicely handles the IPv4-mapped IPv6 addresses (of the form ::ffff:192.168.1.75).
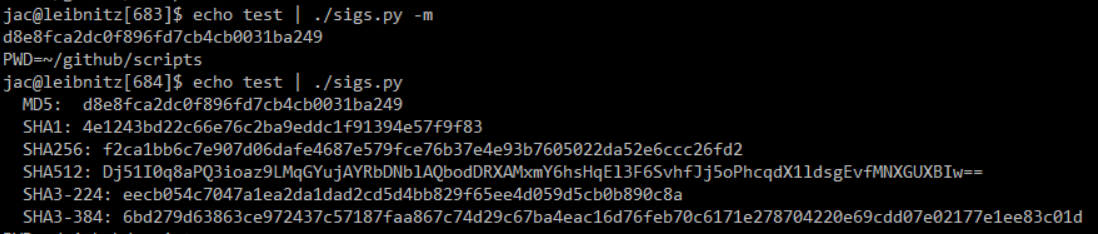
And, during class today, I noticed that somewhere along the line, I broke my sigs.py script when taking input from stdin. That has now been fixed, too.
 Both scripts can be found in my scripts repo on github.
Both scripts can be found in my scripts repo on github.
References:
[1] https://github.com/clausing/scripts
[2] https://github.com/clausing/scripts/blob/master/le-hex-to-ip.py
[3] https://github.com/clausing/scripts/blob/master/sigs.py
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| LINUX Incident Response and Threat Hunting | San Diego | May 11th - May 16th 2026 |


Comments