Threatglass has pcap files with exploit kit activity
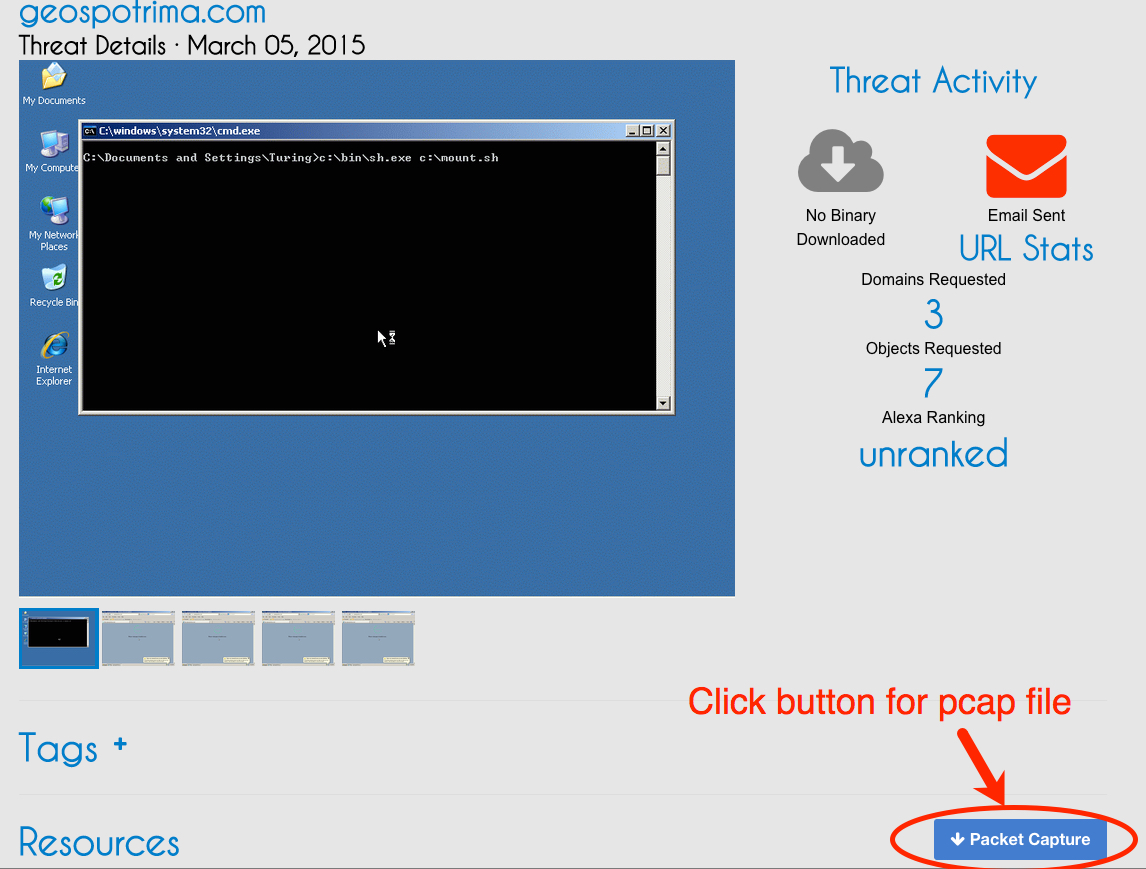
Threatglass is a one way to find up-to-date examples of exploit kit traffic. Not all of it is exploit kit traffic, but all of it represents some sort of malicious activity. Threatglass doesn't explain what type of traffic you're looking at from the pcaps the site provides. Let's look at a page from last week on Thursday, March 5th 2015 [1]. This one is exploit kit activity. In the image below, you'll find a link to the packet capture in the lower right-hand corner of the window:
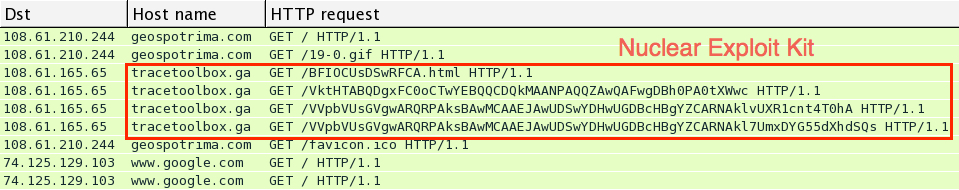
Download the pcap and open it in Wireshark. User http.request as the filter, and make sure you're showing the host name in the column display. We quickly find some unusual traffic, which I know from personal experience is the Nuclear Exploit Kit.
For most exploit kits, the pattern of traffic is: Landing page --> Exploit (Java, Flash, Silverlight, IE, etc) --> Malware payload if the exploit is successful
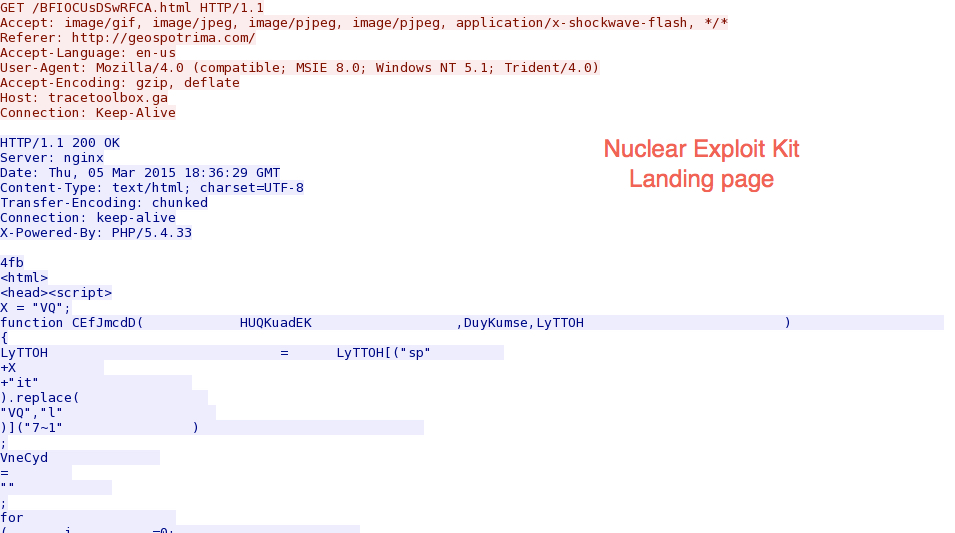
Let's look at this example by following a few TCP streams in the pcap. First, we have the landing page:
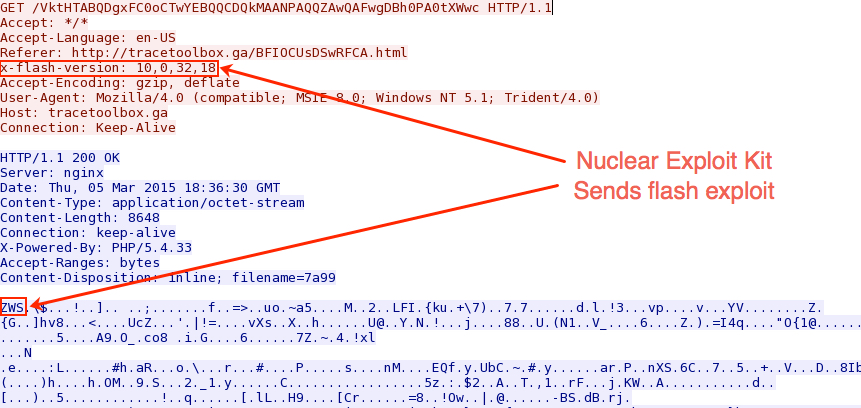
Next, the exploit kit sends a Flash exploit to the victim host:
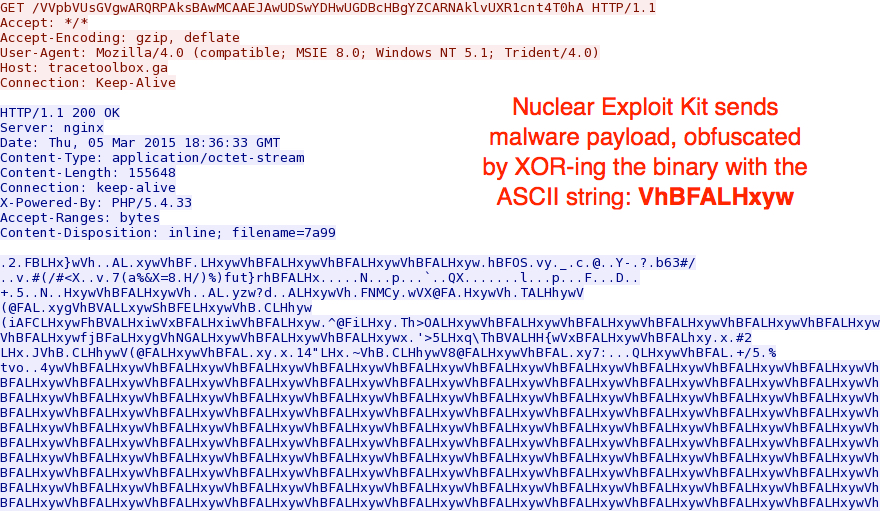
When the Flash exploit works, a malware payload is sent. Currently, Nuclear Exploit Kit obfuscates the malware payload with an ASCII string. In this case, the binary was XOR-ed with the ASCII string: VhBFALHxyw
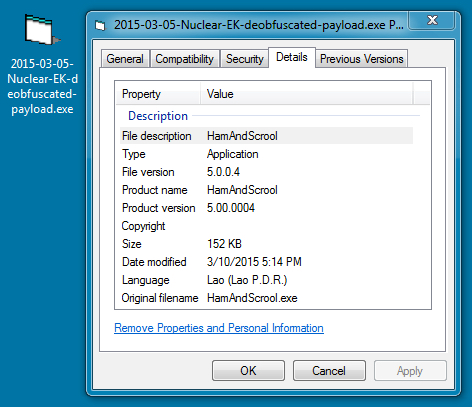
Using a Python script, I was able to XOR the payload with that ASCII string again, and I got the original malicious executable:
The Virus Total results indicate the malware is a Tofsee variant - https://www.virustotal.com/en/file/7659b2be203a34b7491c7101c0275b9e20e8d801d236817a5285c2e63e0ad0e5/analysis/
If you want a sample of the deobfuscated payload, you can get it from malwr.com at: https://malwr.com/analysis/N2U3NDUwMjQ5MWViNGZkNWFlMTBkMjkxMzExZGQxNTM/
If you have the time, review some of the other entries on Threatglass to figure out which ones are exploit kit activity, and which ones are other activity, like fake flash installer pop-up windows. This is one of many resources on line that aspiring analysts can use to build their skills.
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:


Comments
"Using a Python script, I was able to XOR the payload with that ASCII string again, and I got the original malicious executable:"
Is there any way you can elaborate more on how exactly you were able to accomplish this? I'm still very new in the security research area...Thanks
Anonymous
Mar 14th 2015
1 decade ago
Here's the python script:
#!/usr/bin/env python
b = bytearray(open('extracted-file.bin','rb').read())
k = bytearray('VhBFALHxyw')
for i in range(len(b)):
b[i] ^= k[i%len(k)]
open('decoded-binary.exe','wb').write(b)
In order to find the ASCII string, look for the 4th character in. which is normally x00. That will be the 4th character of the ASCII string. Then go to a later place in the file where there are normally a bunch of x00 in a row, which should have the string. Go back 4 from the 4th character, and you have the first character. From the first character, go until the pattern repeats itself. That's the ASCII string you need to use to de-obfuscate the file using the above script.
That's about as clear as I can explain it.
Anonymous
Mar 16th 2015
1 decade ago
This script is tight.
I am new to Python...can you help me understand exactly how this script XORs the binary, or confirm my correctness or incorrectness?
It's super interesting to me and I think I am almost there...but not quite.
It looks like you open the file "extracted-file.bin" as the variable "b"...reading it in as an array of ASCII bytes with the bytearray() builtin.
You then hold the resultant string of bytes open again with that last open().
Next, K is defined as its OWN single-element array of the byte sequence resulting from the ASCII string 'VhBFALHxyw', which you found referenced both in the known malware research as well as the payload reference itself in the PCAP.
You then define b[i] as each byte sequence along the length of the now-ASCII-arrayed binary, and k[i] as each ^= (XOR) against each byte in b[i].
You open the file "decoded-binary.exe" in memory and write each (b) byte to that output exe file.
:D
The XOR works because of the modulus.
Each element of b...b[i]...is added to each k[i] by ^=....and then XOR'd via the remainder that is found when diving each b[i] against each k[i] across the length of k.
For all b.
Am I right?
I feel like I am off somewhere...
...you wrote this five months ago, but you would be a super kind soul to help me pick this apart better.
Thanks :)
Anonymous
Sep 2nd 2015
1 decade ago
Anonymous
Sep 2nd 2015
1 decade ago