The Importance of Malware Triage
When dealing with malware analysis, you like to get "fresh meat". Just for hunting purposes or when investigating incidents in your organization, it’s essential to have a triage process to reduce the noise and focus on really interesting files. For example, if you detect a new sample of Agent Tesla, you don’t need to take time to investigate it deeply. Just extract IOCs to share with your colleagues. From a business point of view, you don’t have time to analyze all samples!
How to perform your malware triage? It will help if you have tools for this (executed from a sandbox). There are a lot of tools to achieve this. Still, another critical element is "automation": Your collected samples must feed a pipe of tools that will try to guess the malware family, extract config, … and why not archive and index everything? For this purpose, I'm using a local instance of mwdb[1] (MalwareDB). Coupled with karton [2]. For example, I'm extracting samples from catch-all mailboxes and sending them to the triage process via the REST API's:
Mail > MIME-Extract > mwdb > karton > Analysis modules (sandbox, YARA, ...)
But sometimes, you need to perform a quick analysis of a suspicious file manually, and you need "manual" tools. Recently, Jim (also FOR610 Instructor) found an interesting tool to achieve this task: Qu1ckSc0pe[3]. Why is this tool interesting? It can analyze multiple types of files: Windows, Linux, OSX binaries, Document files, APK files, and Archive files.
Written in Python, such tools usually require a lot of third-party modules and, therefore, are good candidates to be executed from a Docker container (to avoid pollution of your core OS with a lot of files and libraries). A simple Docker file is provided with the tool, but it was impossible to have a stable installation. So, I create my Dockerfile:
FROM ubuntu:22.04 MAINTAINER Xavier Mertens <xmertens@isc.sans.edu> # Update & install required packages RUN DEBIAN_FRONTEND=noninteractive apt update && apt -y upgrade && apt -y install sudo git python3-pip wget unzip # Install main app WORKDIR /app COPY . . # Stupid fix to allow non-interactive install RUN sed -i "s/apt install/DEBIAN_FRONTEND=noninteractive apt -y install/g" setup.sh RUN chmod a+x qu1cksc0pe.py setup.sh # Another simple fix to avoid breaking the setup script RUN ln -s /root /home/root RUN ./setup.sh # Missing dependencies RUN pip3 install pycryptodome # Install Radare2 WORKDIR /opt RUN git clone https://github.com/radareorg/radare2 RUN radare2/sys/install.sh WORKDIR /app ENTRYPOINT ["/app/qu1cksc0pe.py"]
How to build the tool?
remnux@remnux:/opt$ git clone https://github.com/CYB3RMX/Qu1cksc0pe.git
Replace the existing Dockerfile with mine and build the image:
remnux@remnux:/opt/Qu1ckSc0pe$ docker build -t xme/quickscope .
Now, to use the tool, map a volume containing your samples:
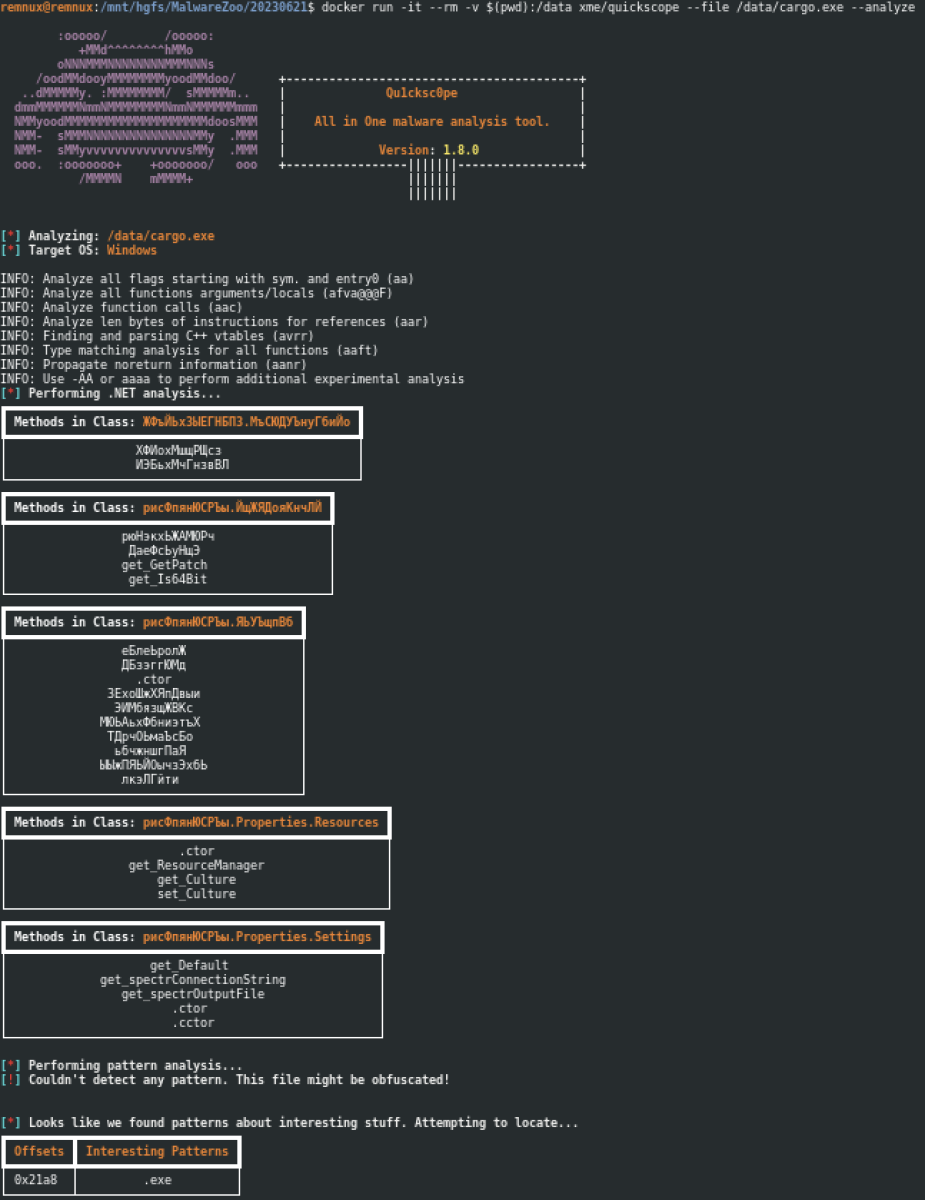
Here is an example against a Word document with a VBA macro:
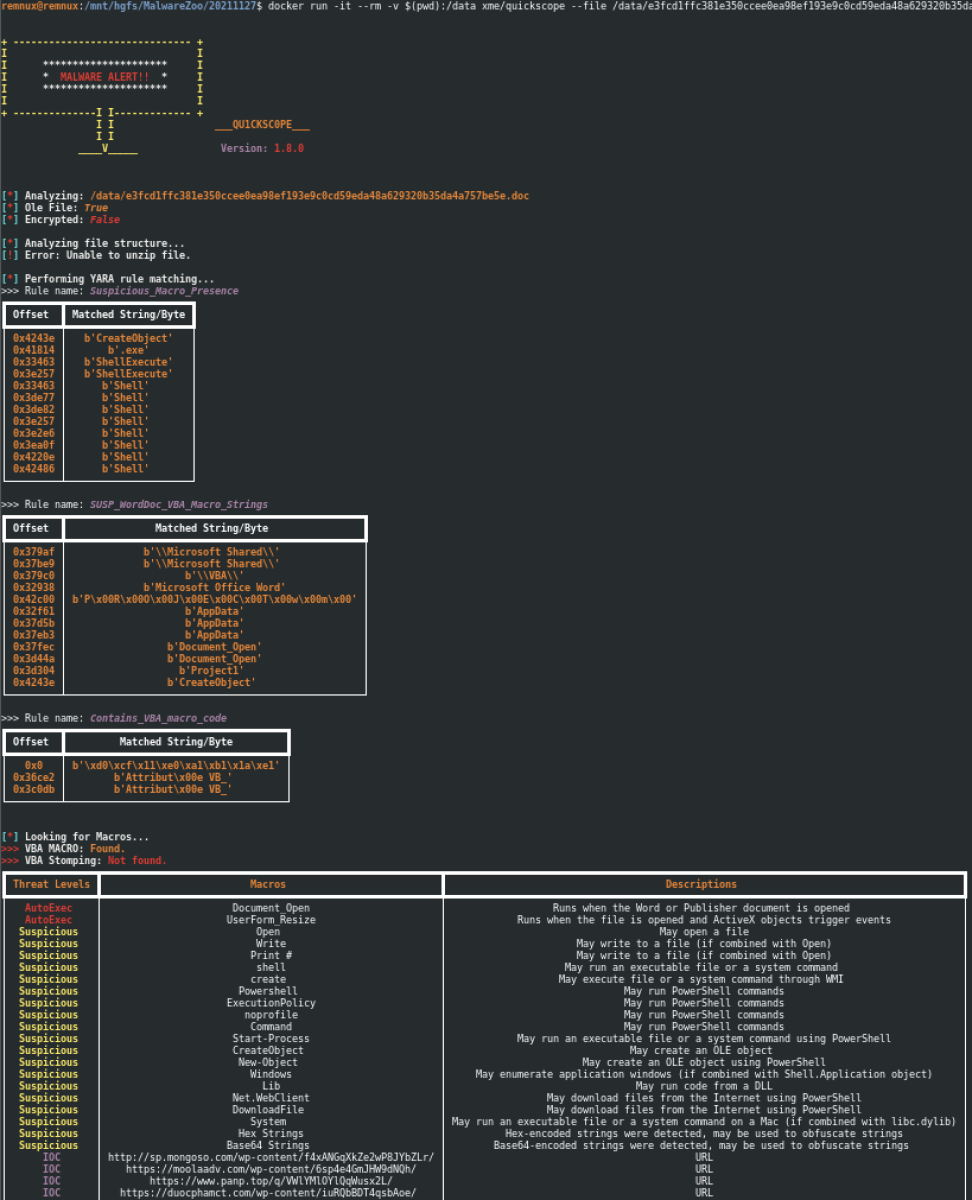
The Dockerfile must still be fine-tuned (for example, to create a volume to keep the YARA rules updated), but it already does the job.
Qu1ckScope has many features that I did not cover here. If interested, look at the repository that provides multiple examples of usage.
[1] https://github.com/CERT-Polska/mwdb-core
[2] https://github.com/CERT-Polska/mwdb-core
[3] https://github.com/CYB3RMX/Qu1cksc0pe
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
syevale111
Jun 29th 2023
2 years ago
syevale111
Jun 29th 2023
2 years ago