Summary of DNS over HTTPS requests against our honeypots.
Our honeypots see a lot of DNS over HTTP(s) requests against the "/dns-query" endpoint. This endpoint is used by DNS over HTTPs requests to receive queries. Queries can use different encodings. You may either see the more readable URL encoding, like "?name=google.com&type=A" or the raw DNS data encoding, like "?dns=mNwBAAABAAAAAAAABmdvb2dsZQNjb20AAAEAAQ".
Decoding the raw queries isn't hard, but note that the padding "=" characters are cut off at the end. Some base64 implementations will refuse to decode data with missing padding.
Our database lists a total of 5,727 different URLs starting with "dns-query". Only 12 of them use the "URL encoded" format, with by far the most common one being
/dns-query?name=baidu.com&type=A
and
/dns-query?name=dnsscan.shadowserver.org&type=A
A few used queries to echodns.xyz to find open resolvers. For DNS over HTTP(s), an attacker would not use an open resolver for denial of service attacks (at least there is no amplification). But they may use it to obtain an anonymous DNS relay. Shadowserver uses these queries to populate their open resolver feed.
The remaining 5,714 queries use DNS encoding. DNS encoding does include a random query ID (not required for DNS over HTTP(s), but still often set). We need to decode the names to find out which unique names are being resolved.
Query IDs appear somewhat random, with no query ID appearing more than twice, and all queries were for exactly one record, making decoding easier. So I had to channel my inner Didier and wrote a quick Python script to decode. For the most part, I had Google's copilot write it for me. It did a good job, I believe.
The results:
| # of Requests | Hostname |
|---|---|
| 5335 | baidu.com |
| 39 | www.google.com |
| 8 | openresolver.dnslab.cn |
| 2 | www.example.com |
| 1 | example.com |
| 1 | download.windowsupdate.com |
| 1 | amazon.com |
Many of the requests originate from Alibaba's cloud. Interestingly, the user-agent used is just the word "Chrome" for many of these queries, indicating that a specific tool is likely used for these scans.
In summary, aside from some researchers, scans for open DNS over HTTP(s) resolvers are likely used to anonymize browsing traffic. We do not have sufficient data to see what they are looking for. Even configuring one of our honeypots as an open resolver has not yielded more exciting results.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|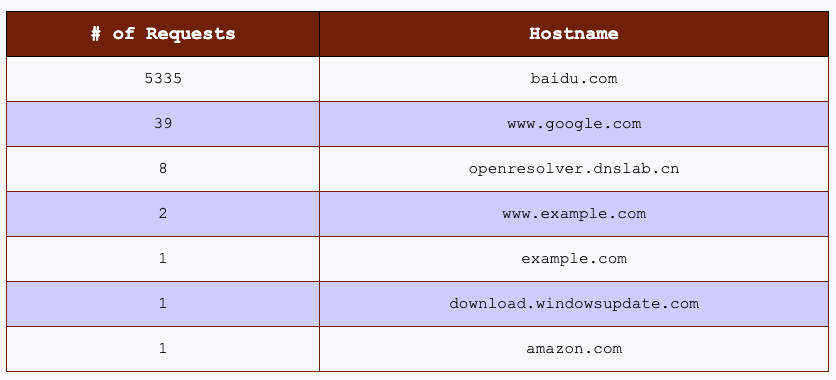
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments