Scans for RDP Gateways
RDP is one of the most prominent entry points into networks. Ransomware actors have taken down many large networks after initially entering via RDP. Credentials for RDP access are often traded by “initial access brokers".
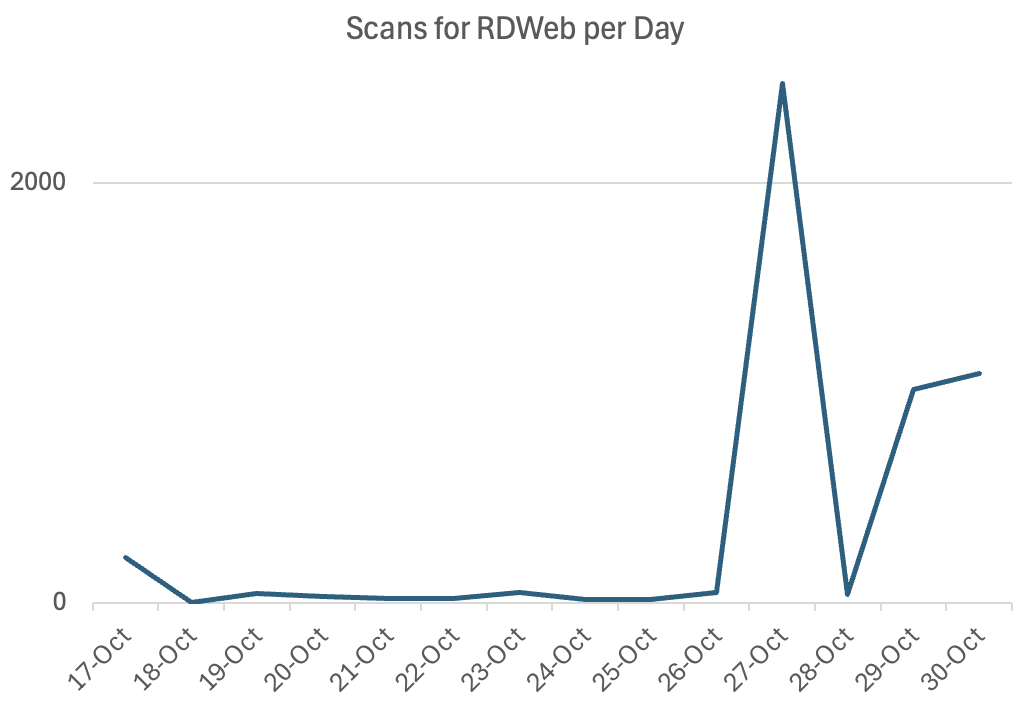
I noticed today an uptick in scans for "/RDWeb/Pages/en-US/login.aspx" . This is often used to expose RDP gateways, and there are even well-known Google dorks that assist in finding these endpoints. The scans I observed today are spread between several hundred IP addresses, none of which "sticks out" as more frequent than others. This could indicate a large botnet being used to scan for this endpoint.
There are three variations of this URL being used, all with the same effect of detecting the presence of an RDP gateway:
/RDWeb
/RDWeb/Pages/en-US/login.aspx
/RDWeb/Pages/
The first two are used the most, and the third (/RDWeb/Pages/) is used very little.
This data is from a subset of our honeypots that appears particularly attractive to these scans. The idea isn't new, but it appears that some group has "rediscovered" it.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments