Sandfly Security
Agentless Linux security with unmatched speed and reliability
Sandfly Security, headquartered in New Zealand (where they know sandflies all to well), refers to itself as such because they’re like sandflies: they relentlessly bug and discourage intruders, deploying like a swarm onto endpoints, then disappear only to return again and again. Theses swarms of checks make life miserable for hackers on Linux hosts while minimizing system impact. I’ve been following Sandfly’s Craig Rowland on Twitter for awhile with the intent of giving Sandlfy a look for toolsmith, and in the time I’ve kept watch, the offering has grown into a comprehensive and robust platform for Linux security.
Please note that Sandfly Security is a commercial platform that includes a free offering. My coverage of Sandfly is unsolicitated, and not compensated in anyway, but Craig did provide me with a professional license for a more comprehensive testing opportunity. The free license enables you to protect up to 50 hosts with 5 user accounts. The team created Sandfly with understanding of the limitations of conventional endpoint products. “A novel agentless method ensures security while monitoring and responding to threats across Linux systems without the risks associated with endpoint agents.” (Sandfly, 2023) The time was right for a Sandfly review in keeping with the v4.5.0 release. Sandfly 4.5.0 includes a massive capability upgrade with a new expression language syntax. This upgrade greatly expands how agentless threat hunting and incident response modules can be used to protect Linux, and includes:
- New expression language syntax allows rapid and wider creation of custom threat hunting sandflies for customers
- All built-in modules have been reviewed and depth of coverage for Linux threats broadened
- Expanded CPU support to cover IBM POWER8, 9 and 10 processors (Sandfly, 2023)
Please note that Sandfly Security is ridiculously well documented, every step I describe here is already provided in great detail via Documentation. As always, my goal is to pique your interest: protect your Linux hosts, people!
I took the easiest path for my Sandfly Server deployments and made use of the Digital Ocean preconfigured droplet image sandflysecurity450onubuntu2204. Instructions to do so are simple and straightforward, I was up and running quite quickly. While a production instance would likely include Dockerized servers and nodes, this setup includes server and node in one installation. The Sandfly UI has a common and comfortable feel to it and is intuitive and simple.
Figure 1: Sandfly UI
Craig provided me with a target range for testing, to connect to it I was required to go through a jump host so my order of configuration was Add Credentials, Add Jump Host, then Add Host. Once complete, all hosts were added to the queue, complete with authentication, and ready for a new manual scan.
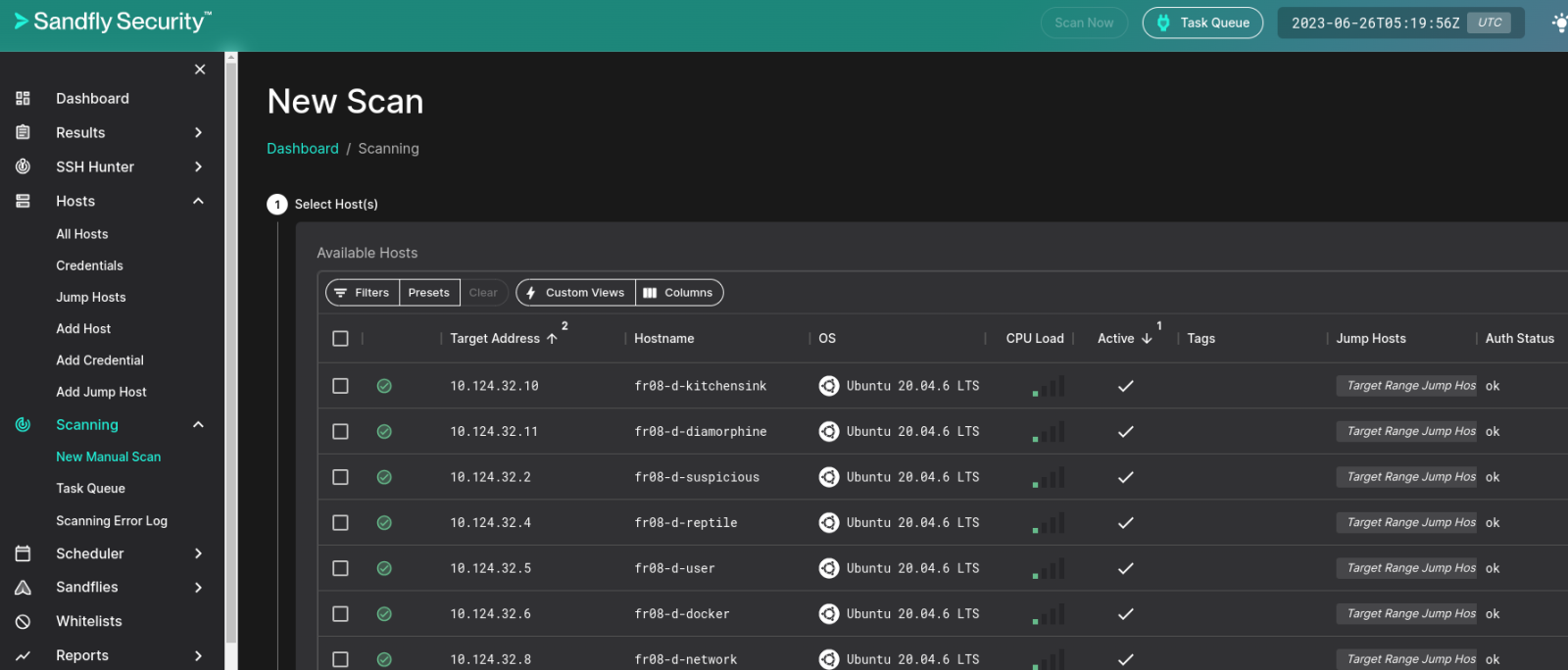
Figure 2: Sandfly Manual Scan
After you select target hosts, you have many choices for available Sandflies. These include Sandflies that are templated, or specific to incidents, directories, files, processes, logs, policy, and recon: 1168 Sandflies in total per the CSV I exported from the UI to assess my options. For this set of targets 587 Sandflies were made ready for me, I selected them all, and let fly. ;-) This sent my scan to the Task Queue and quickly produced findings in the Results menu inclusive of Results by Host, Results by Sandfly, or an all encompassing Results view.
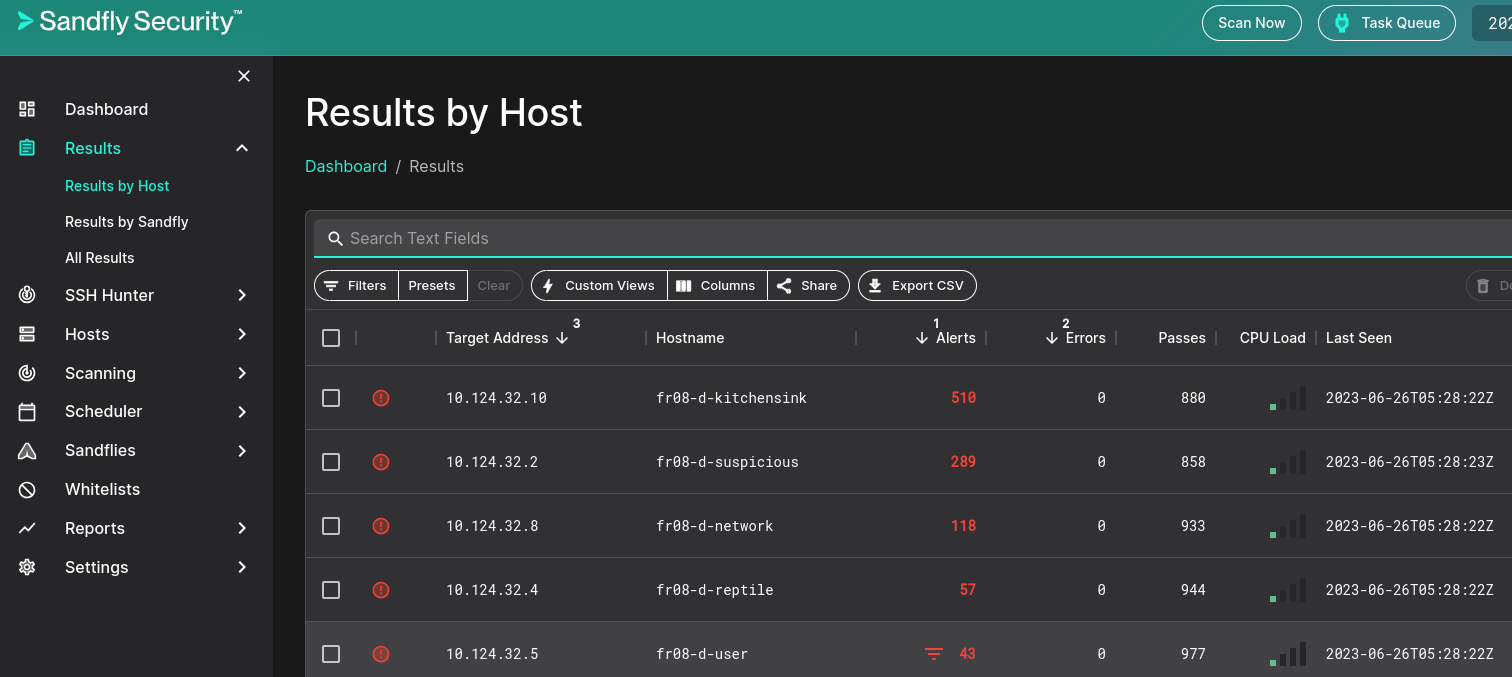
Figure 3: Sandfly Results by Host
Of immediate interest to me was zero errors and minimal CPU load. The agentless approach really does offer significant advantage. Recognizing that we threw all available Sandflies at these hosts, the result was as many as 510 alerts for a single host. Given, these hosts are the Sandfly equivalent of Metasploitable for testing purposes, but I chose to spend time with a host with fewer alerts to zoom in with effect: fr08-d-user (10.124.32.5). I was intrigued with the SSH Hunter feature and immediately ran down that rabbit hole with this host. Using Host Investigation under the SSH Hunter menu, I found fr08-d-user immediately and noted that it was red flagged for duplicate key entries.
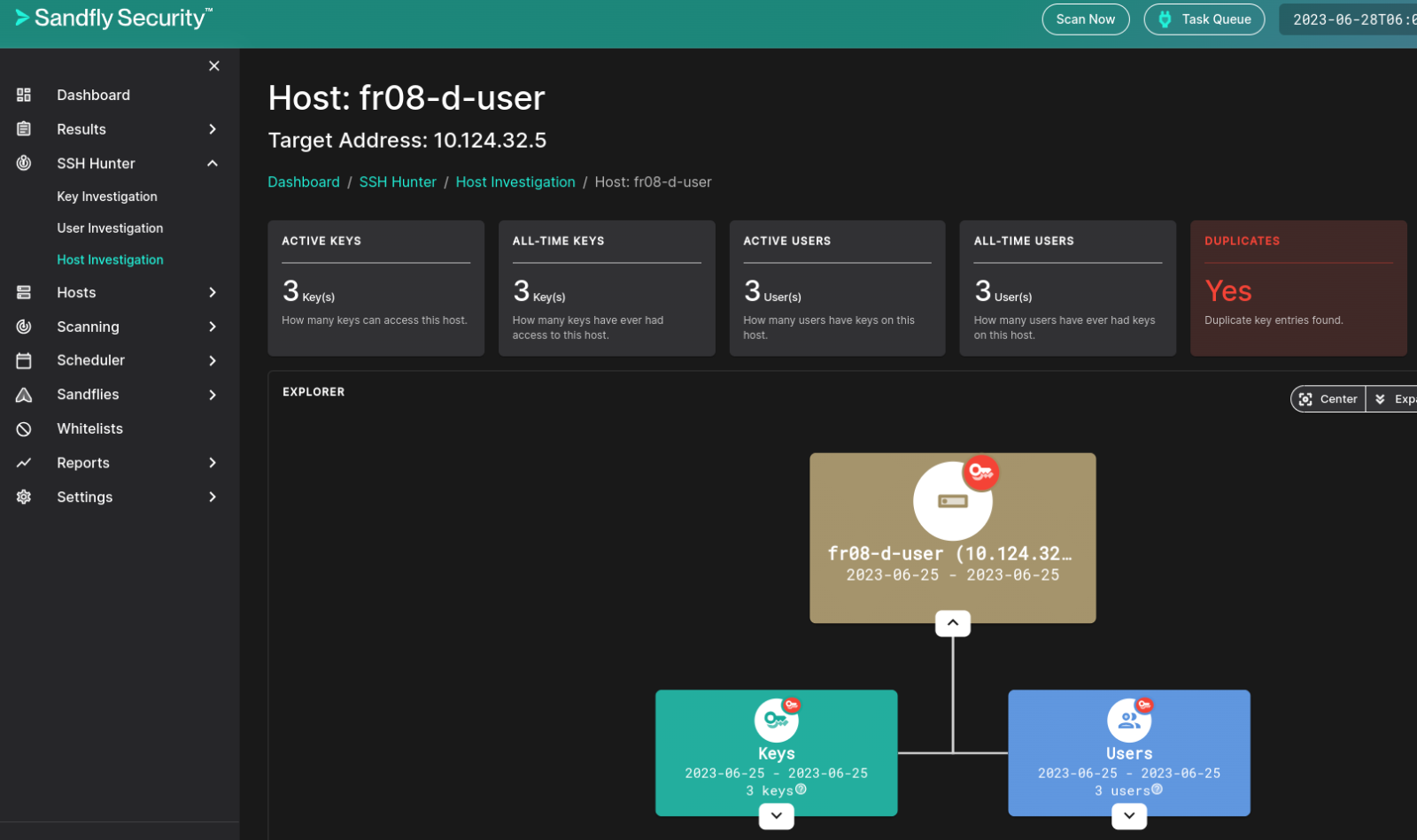
Figure 4: Sandfly Host Investigation
With the duplicate key entries finding I jumped back to Result by Host for fr08-d-user and zoomed in on the policy_user_ssh_authorized_keys_duplicates_found Sandfly. The Results Detail view for this alert (Result 2992) was one of the more rich, hunter-centric results and made my inner security analyst extremely happy. Please note that, via Raw Data, JSON data for each alert can be accessed. Automation, message topics, correlation, oh my!
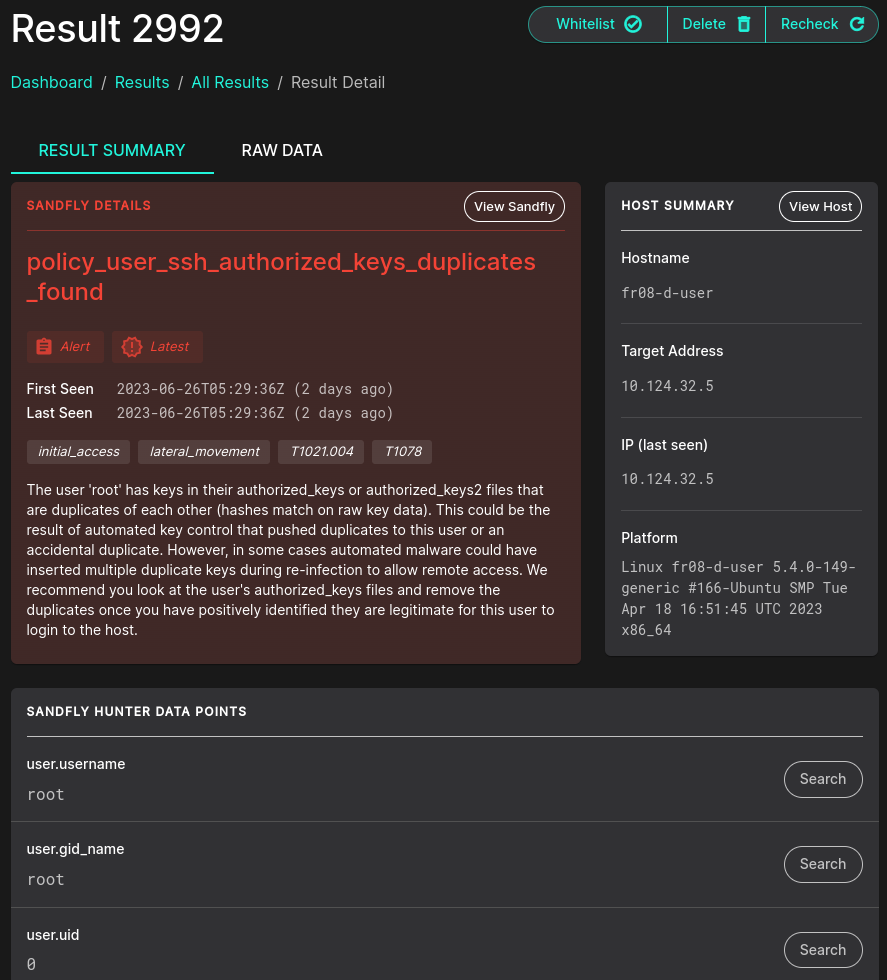
Figure 5: Sandfly Result Detail
I love the Sandfly Hunter Data Points as well. This is easily another rabbit hole to run down, which I did so exploring a different alert, specifically process_deleted. Result 3085 stated that “the process name ‘killdemoprocess’ with PID ‘13311’ binary has been deleted from the disk but it is still running at ‘/tmp/killdemoprocess’. This could be a malicious program still resident in memory and trying to hide from the file system.” Note also the T1070.004 tag, aka the MITRE ATT&CK technique reference for Indicator Removal: File Deletion. You’ll find such tagging and labeling throughout the platform, enabling additional immediate insights and a direct connection to well defined industry standards. Scrolling through the related Sandfly Hunter Data Points, I settled on process.hash.sha1 and hit Search.
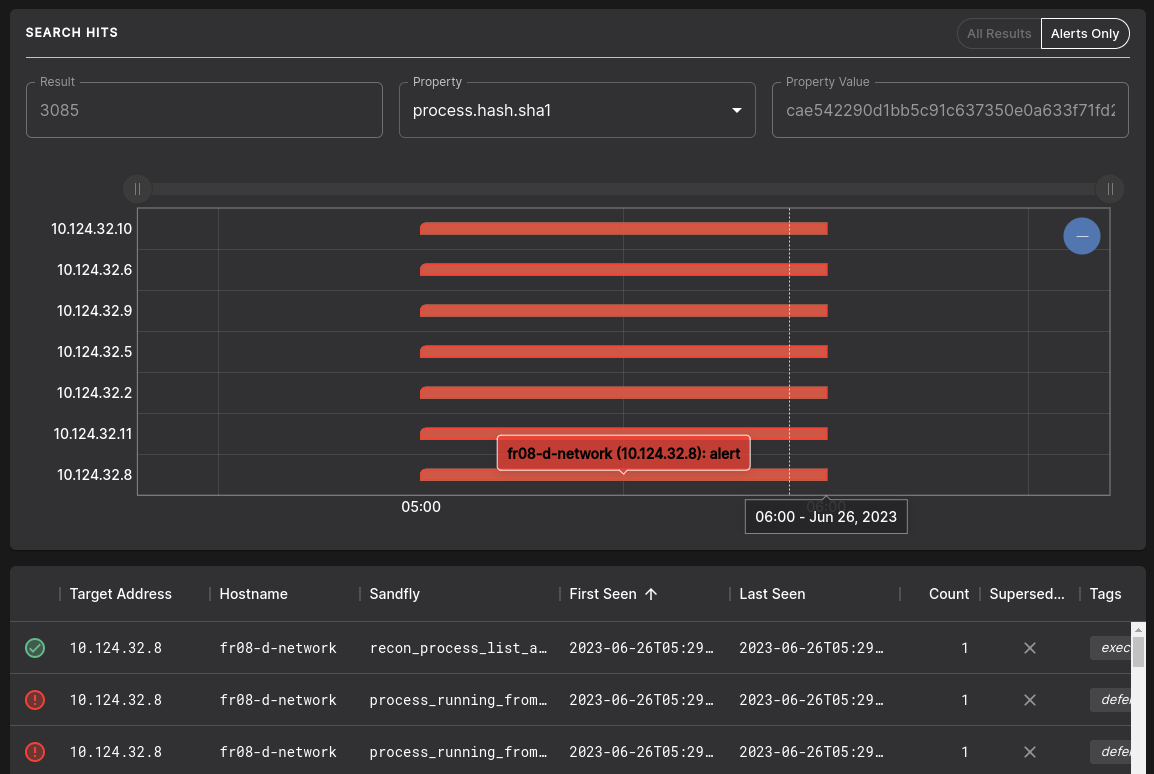
Figure 6: Sandfly Hunder Data Points
What!? This same process is running on other victim systems? Whodda thunk. ;-) This is a pivoting hunter’s paradise.
If I were still in the business of security operations and caring for Linux systems, Sandfly Security would absolutely be front and center in my defender’s arsenal. This offering, quite candidly, exceeded my expectations. I expected great, it’s even better. Well done to Craig and team! Grab yourself a free license, put it to use for a small deployment, and spend way more time testing the boundaries of this platform than I did. And seriously, read the documentation; to call this a “tip of the iceberg” review is an understatement. There’s profound capability awaiting you with this platform.
Cheers…until next time.
Russ McRee | @holisticinfosec | infosec.exchange/@holisticinfosec | LinkedIn.com/in/russmcree
References
Sandfly Security. (2023, March 17). Our Story. Sandfly Security - Agentless Linux Security and EDR. https://sandflysecurity.com/about-us/our-story/
Sandfly Security (2023, June 12). Sandfly 4.5.0 - powerful new expression syntax. Sandfly Security - Agentless Linux Security and EDR. https://sandflysecurity.com/blog/sandfly-4-5-0-powerful-new-expression-syntax/


Comments