Quick look at a couple of current online scam campaigns
Since I was exposed to three different online scam campaigns in the last three weeks, without having to go out and search for them, I thought that today might be a good time to take a look at how some of the current online scams work.
All of the campaigns we’ll mention seemed to target people in the Czech Republic, although not exclusively, as one of the landing pages I found had at least 20 different regional variants set up for countries from all over the world. In cases where I was unable to find an English version of a page, I had Chrome translate it – the results are not always pretty, but should be sufficient for our purposes.
Everything started a couple of weeks ago, when I was searching for a website of a certain small town theater on my phone. Having found it on Google, I tapped the relevant link and was surprised when, my browser didn’t stop at the intended destination, but rather was redirected to a site proclaiming me a "lucky visitor" of the day with a "chance to win Apple iPhone 11 Pro".
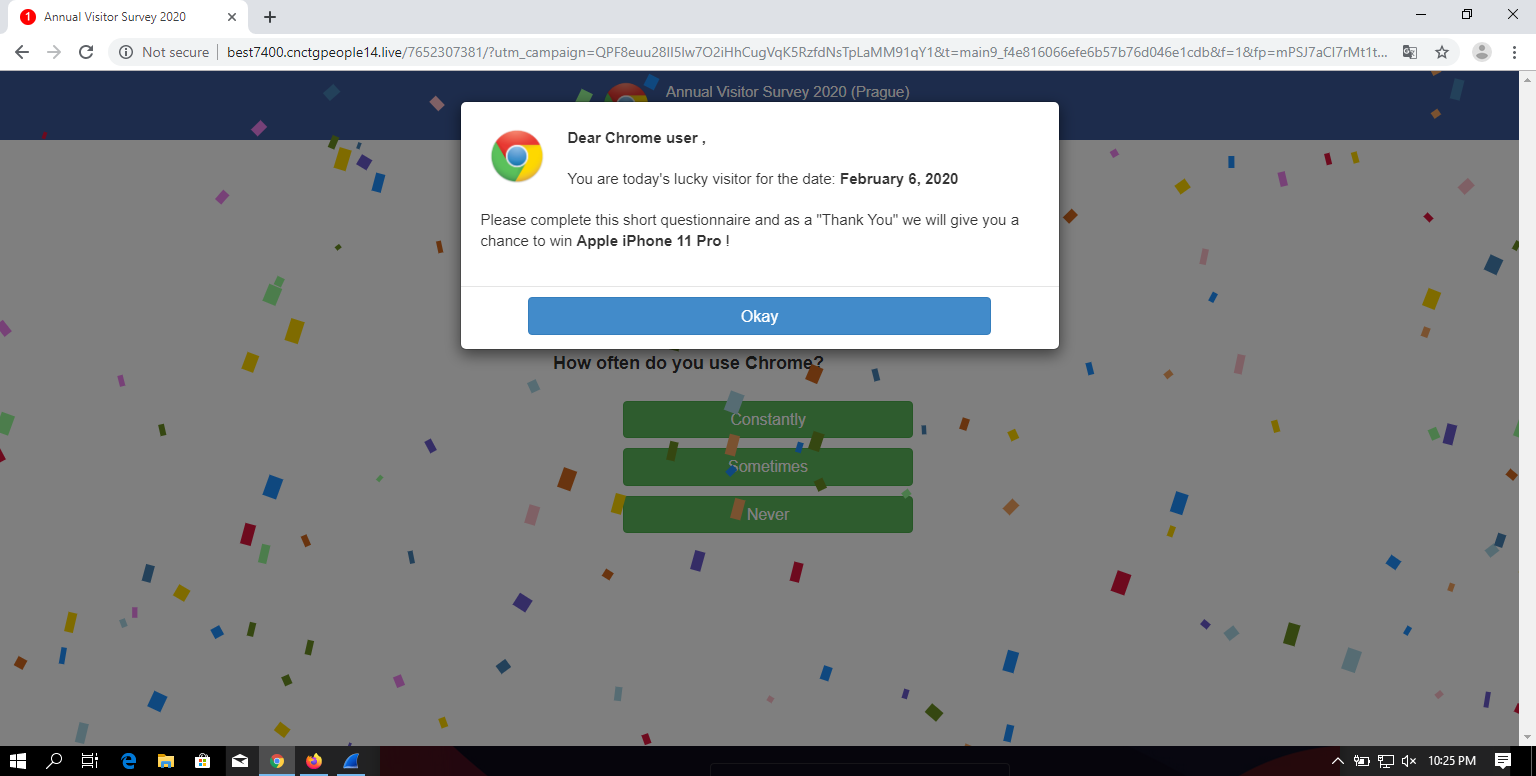
Given all the ad blockers and script filters I usually use, I didn’t see any similar pages or pop-ups similar to this one (not counting phishing pages, of course) for a long time, so I decided to take a closer look at it. After clicking through four questions related to my preference in browsers, I was informed that I had a chance to win a brand new iPhone (although it wasn’t quite obvious that the offer was to enter a contest and not to buy the phone at an incredibly low price, as you may see for yourself).
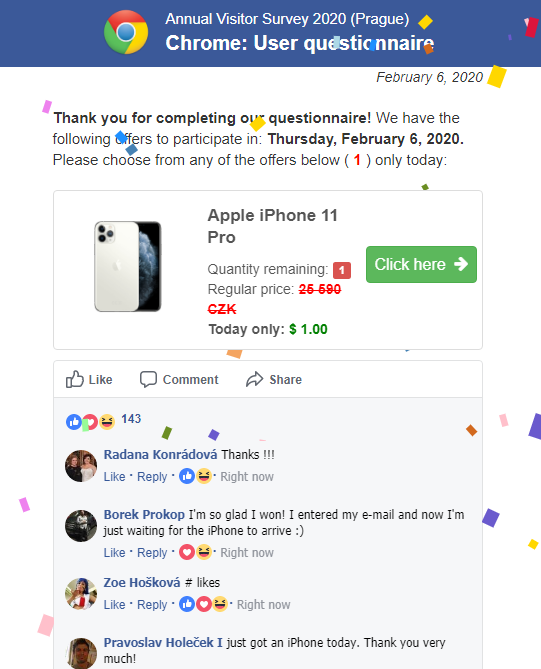
One interesting part of this page, which deservers a special mention, was the comments section at the end, as it was seemingly populated in real time through JavaScript embedded in the HTML code. That is, all the comments were loaded as part of the original page at the same time, but displayed one at a time. I imagine that having them appear one after another with "like counts" rising while the user watches might look quite convincing to potential victims.
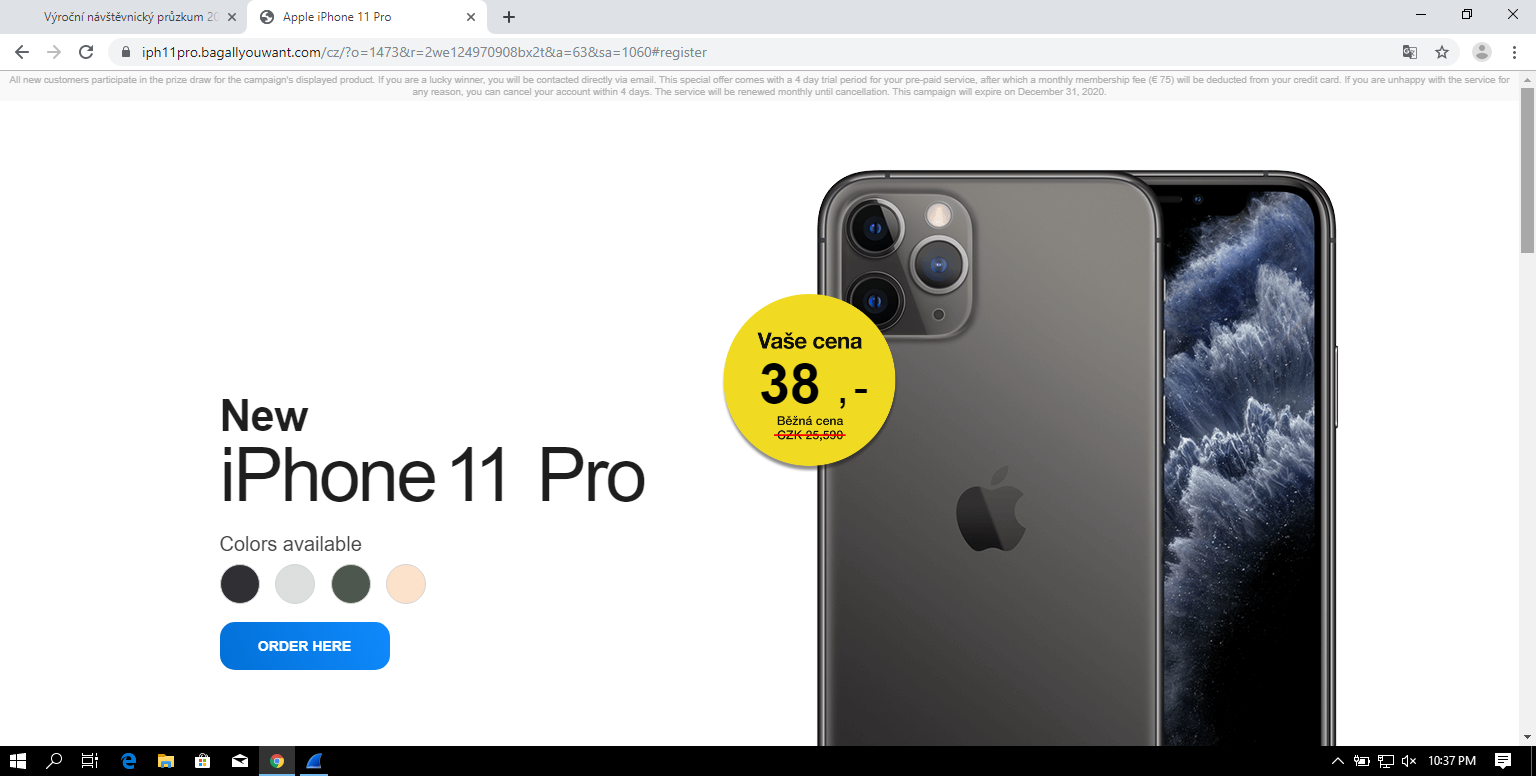
After clicking the button, browser was redirected to another domain where it seemed, once again, as if a user had the option to buy an iPhone for a small fraction of its usual price.
Next, the site asked for some personal information – a full name and an address along with an e-mail and a phone number.
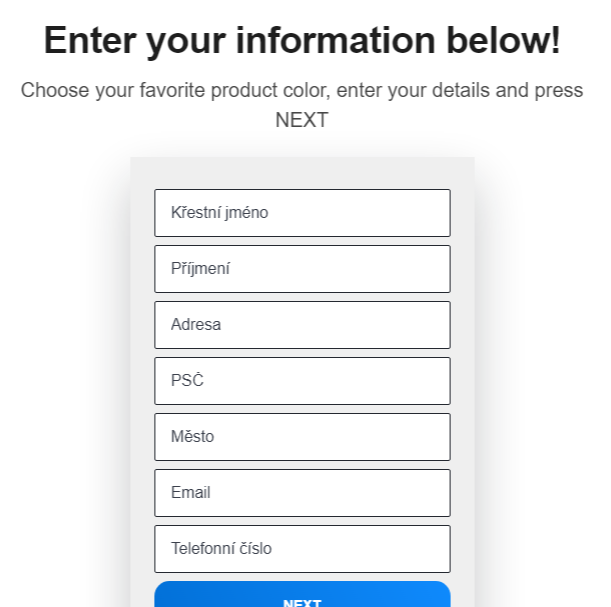
What wasn’t obvious at first glance, but would be really important to anyone actually trying to order the phone, was a small paragraph hidden at the end of the page, explaining that the customer wasn’t actually buying an iPhone, but was merely entering a prize draw for it. By itself, that wouldn’t be so bad, but the rest of the text mentioned that, besides confirming his participation in the contest, the user would be subscribing to an unnamed pre-paid service with a €75 monthly fee.
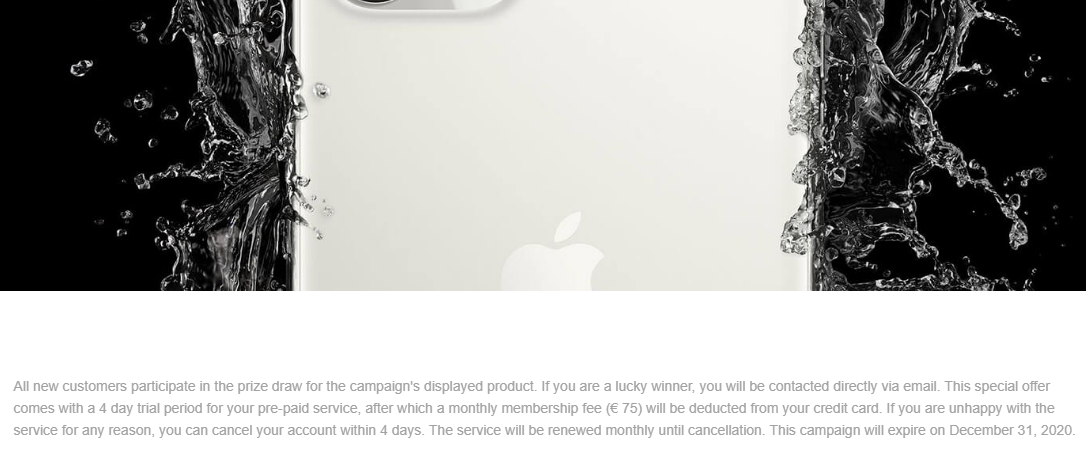
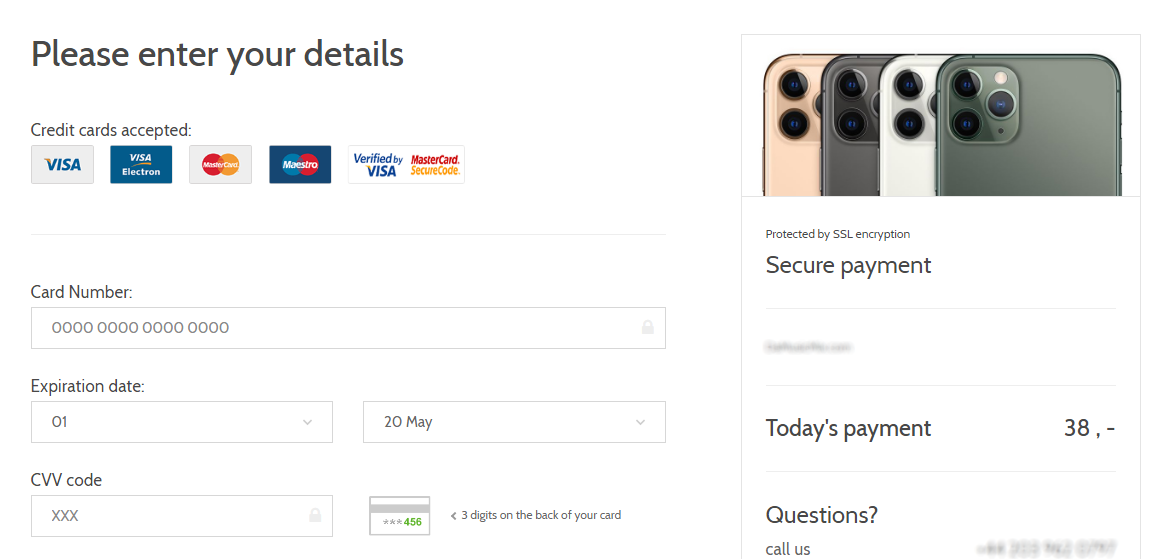
The last thing required of a user at that point, would be to fill in his credit card details in order to confirm the payment. Not the €75 subscription, which would later be charged against users account, but the "price" for the iPhone (or rather for a participation in the iPhone lottery) of approximately €1.5.
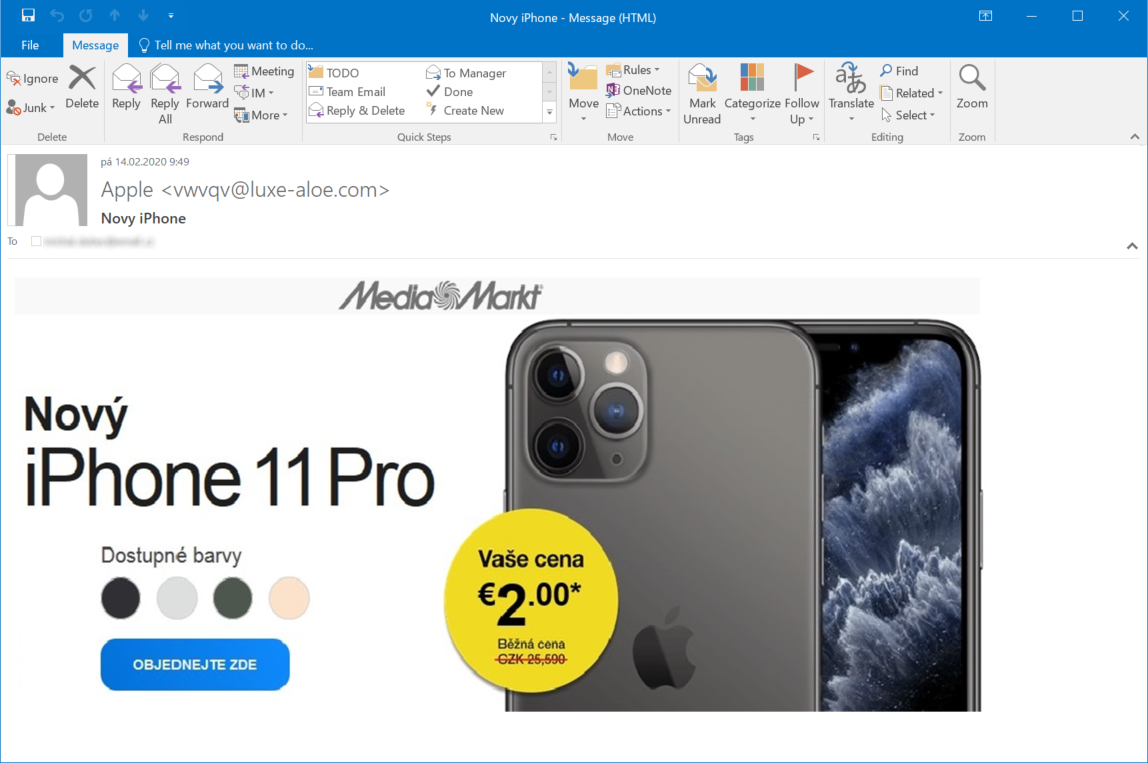
About a week after I found the previously mentioned website, a colleague of mine asked me, laughing, whether I wanted to buy a new iPhone for €2. My first guess was that he managed to end up on the same site I did. This, however, didn’t turn out to be the case as the second campaign was a straightforward phishing. Nevertheless, what caught my attention was the use of the same graphical style I saw in the previous campaign.
Apart from the stripe at the top, the landing page (and other pages, all the way to the payment form) was nearly identical to those used in the first campaign as well.
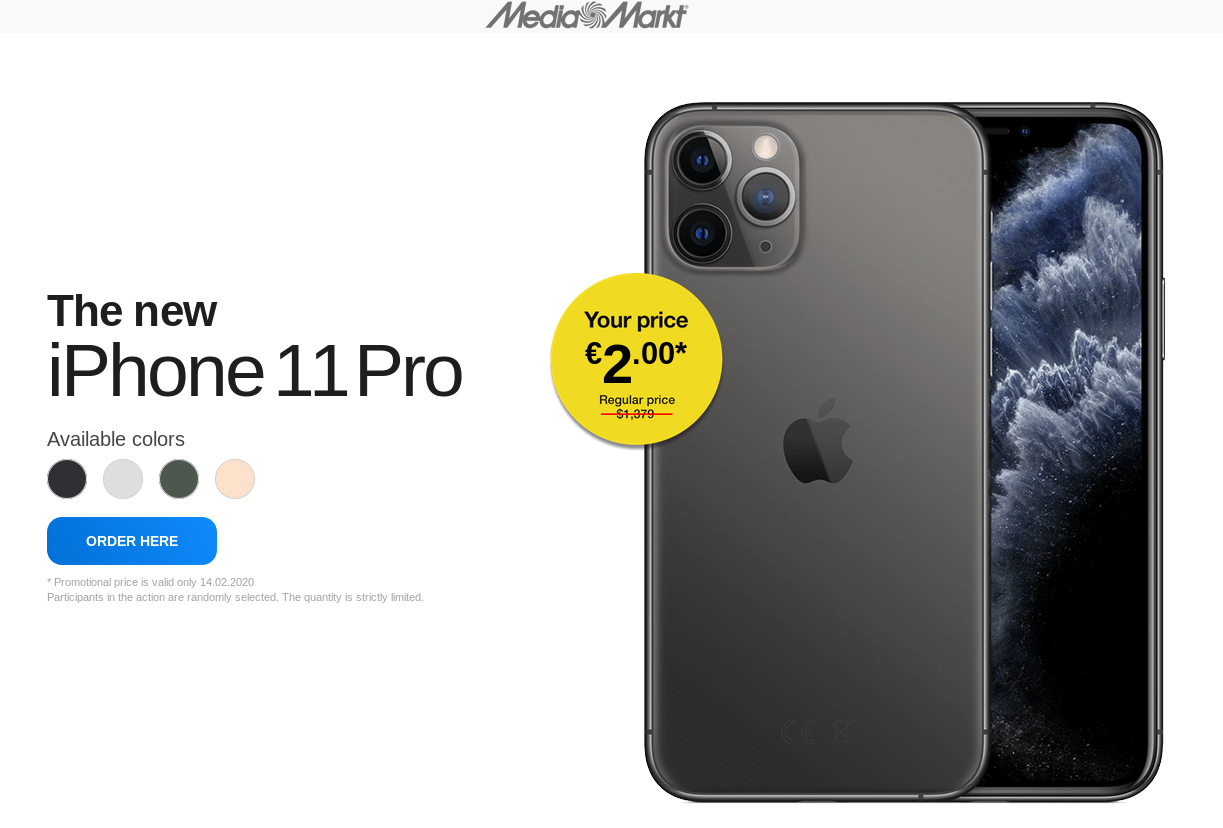
Unlike in the first campaign, however, there was no paragraph on any of the pages explaining whether the user was actually subscribing to any service, so it is hard to say what unexpected things one might be charged for if one actually tried to buy an iPhone in this way.
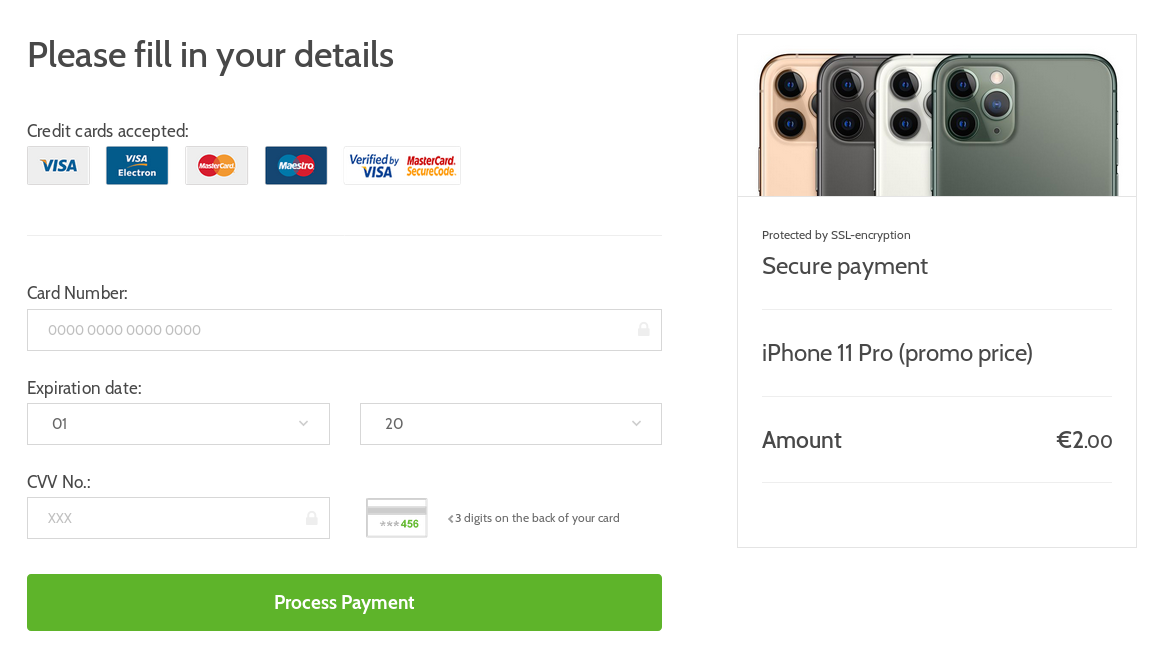
Although the second campaign comes much closer to a phishing style of operation than to a classic scam, re-use of the same assets in both campaigns is interesting. Use of the same phishing kits (or "scamas" as they are sometimes called) on multiple sites is not too unusual – many such kits are actually open-sourced and some may even be found on GitHub. Nevertheless, one usually doesn’t expect to see the same kit used twice within a couple of weeks for two different campaigns with different modes of operation…much less three.
On Saturday, I was looking for information about a vulnerability in a certain software product and one of the results, which Google returned, ended up pointing my browser to another site with the same landing page offering iPhones for €2. At first glance, it looked like another campaign simply re-using the same kit, however, after a bit of digging around, I discovered that this campaign was actually much more complex than the previous ones.
The first and second campaigns used couple of forced redirects each to get a user to the landing page.
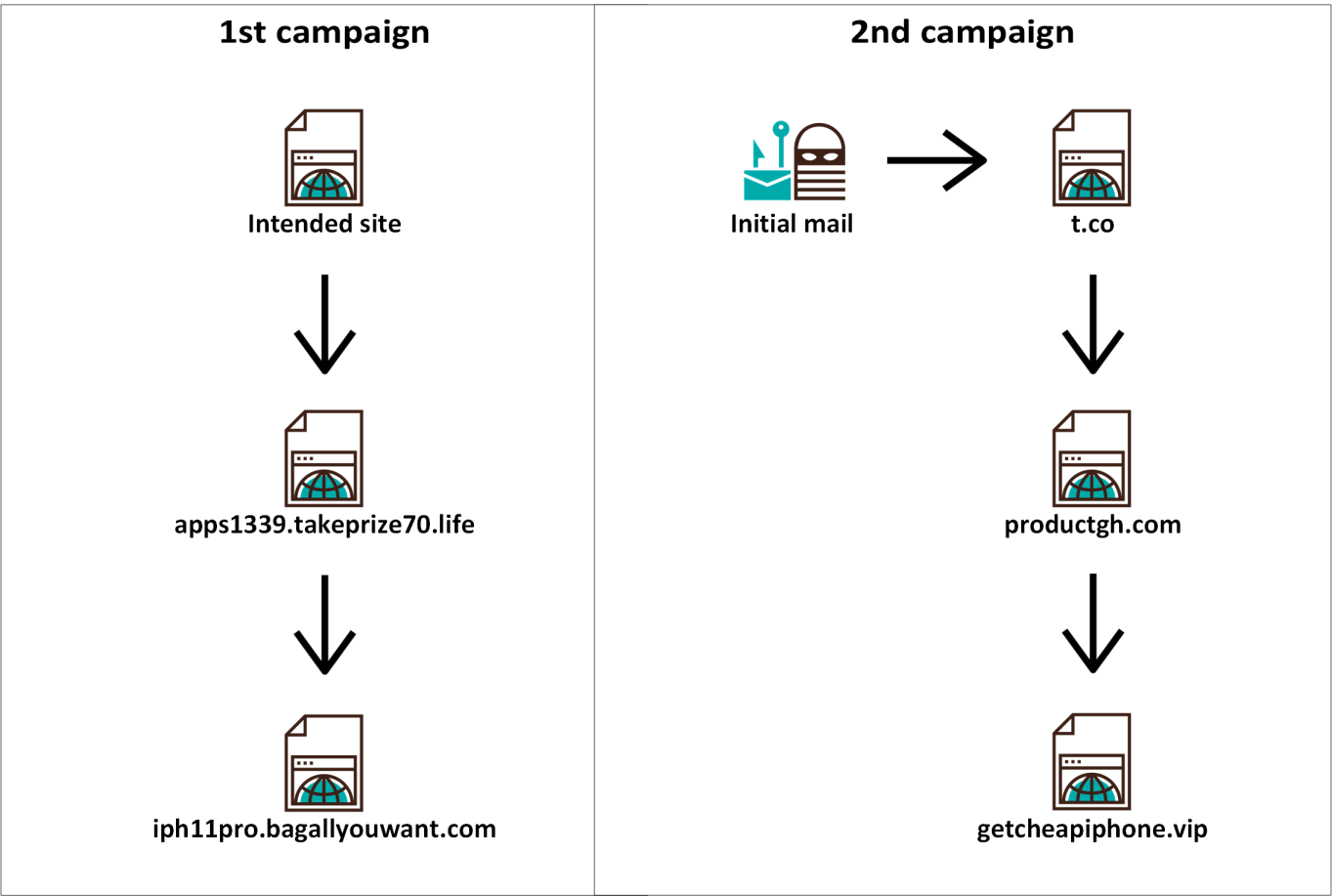
The third campaign had multiple starting pages on multiple domains redirecting to a couple of domains/IP addresses, which finally redirected to multiple landing pages (or, under some conditions, to Google). I only mapped out a small part of the starting and landing pages, but the following diagram should give you an idea of the inner workings of this campaign.
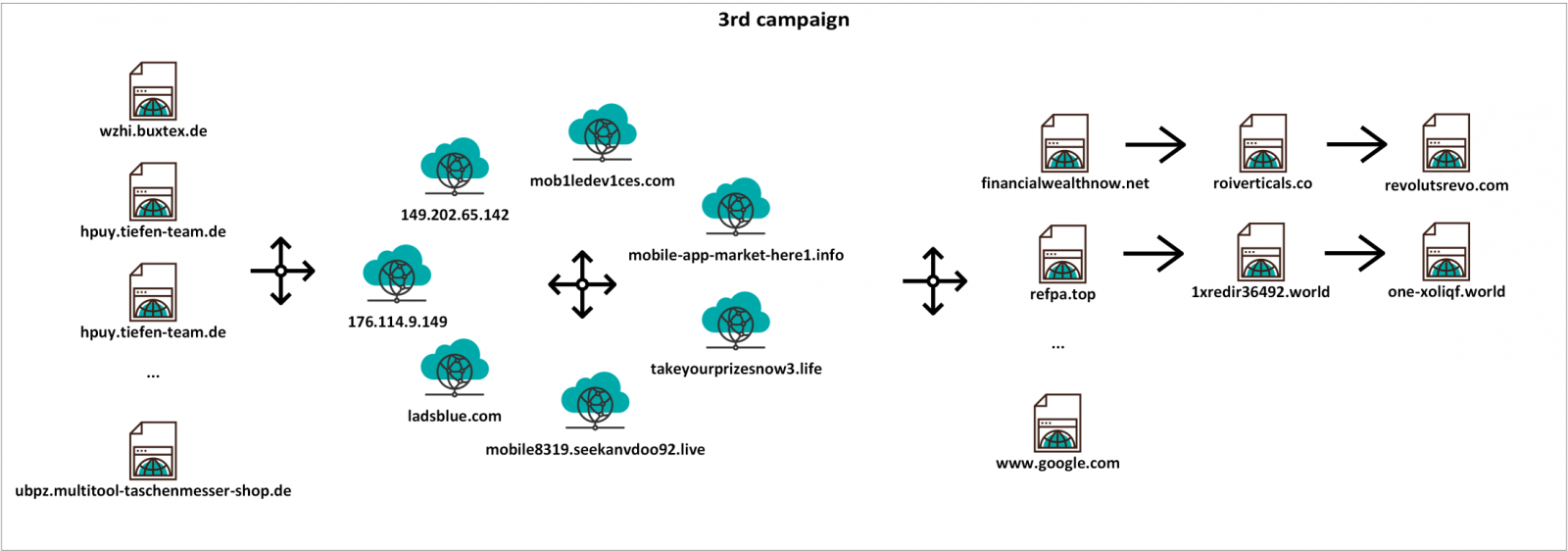
Since all three parts of the redirection chain were interesting, let’s take a look at each one in turn.
The initial/starting pages used cloaking (i.e. serving different content to search engine spiders than to regular users[1]), which was the reason I landed on one of these pages in the first place – Google had it indexed as containing information which wasn’t actually there. In addition to the cloak, a referrer check was implemented on the servers serving the initial pages to make things a little more complicated. The behavior and responses of the servers did therefore differ quite significantly based on a couple of factors.
- If a user should manually enter the address of one of the initial pages (for example hxxp://wzhi.buxtex.de/web-shell.html), the server would return a HTTP 404 response.
- If the same user were to navigate to the same page through a link from a search engine, the server would return a HTTP 302 response and would redirect the browser in the way shown in the diagram above. The server would only provide the 302 response if an address of a well-known search engine (e.g. Google or Bing) was present in the Referer header of the HTTP request. With the Referer header set to any other value, the server would – once again – return a 404 response.
- Finally, if a search engine spider such as Googlebot were to visit the page, it (or anyone using a User-Agent header set to "Googlebot") would be served with a clickbait content cobbled together from different sites. In case of web-shell.html for example, one part of the content was taken from an article published on rapid7.com.
Given the behavior of the servers described above, it is almost certain that any real user would be redirected to another URL after visiting one of the initial pages. That would start a chain of multiple forced redirections between the domains and IP addresses mentioned in the diagram above (and potentially others as well).
Although many of these appear to be suspicious at first glance, not all of them are necessarily malicious – one of the domains, ladsblue.com, actually belongs to a commercial advertising network named Adsterra. A quick Google search for Adsterra led to a number of claims that this network doesn’t always operate ethically[2], however, hoping that these claims are not correct, I did let the company know about the misuse of their ad network with the hope that they will block it.
The redirection chain would end on one of a number of different landing pages, chosen based on geolocation of the IP address from which the user was connected (and potentially other factors). It is possible that not all of the pages one might land on after the redirects end are related to scams. One of the redirection chains, for example, led to a page for a certain betting site, and even though Google results seem to indicate that it might not be a completely legitimate service, I can’t be sure of that without further research I wasn’t willing to put in.
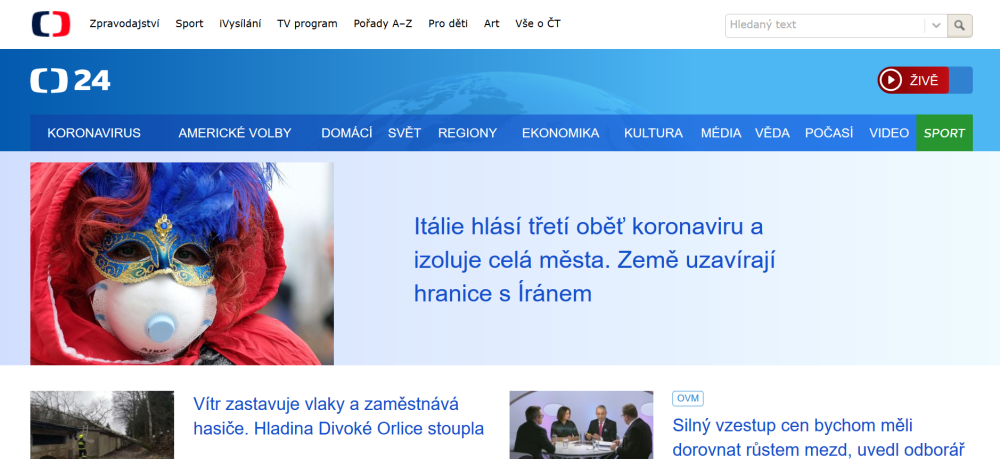
The one site we can be quite sure was a scam, however (apart from the site using the "iPhone for €2" kit we saw in the first two campaigns), was hosted at the domain hxxps://financialwealthnow.net. The reason we may be certain of the fraudulent nature of the site is that this site was a copy of the official website of a Czech 24 hour news TV station[3].
This is the real site...
...and this is the fake one.
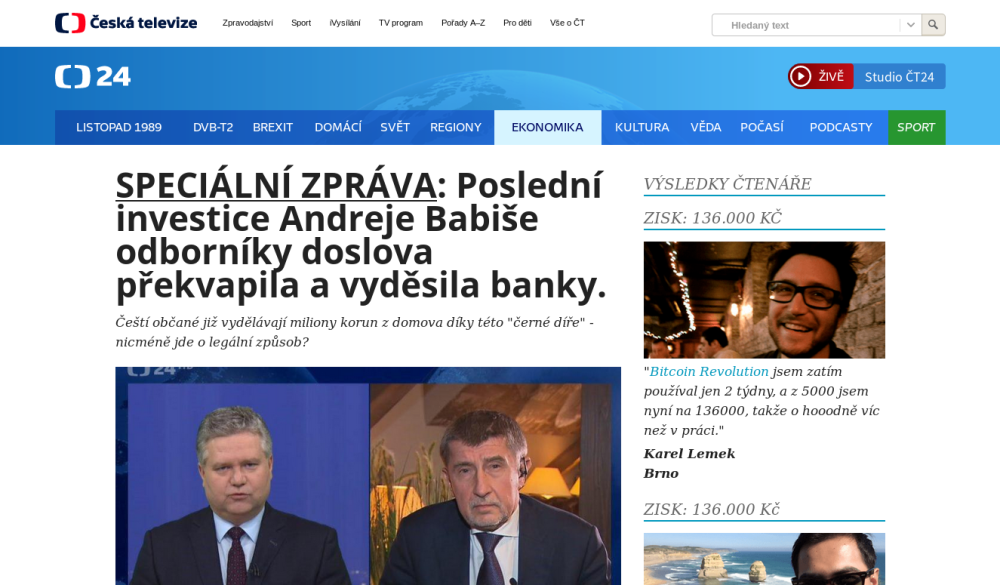
The text on the site tries to get visitors to register with a cryptocurrency trading platform with promises of instant wealth and with the help of a fake interview with a well-known Czech politician and entrepreneur praising the platform. If you’d like to take a closer look at the contents of the fake page, I wrote a short post about it (in Czech) at untrustednetwork.net[4].
What appears to be even more interesting than the contents of the page themselves is that the site seems to be part of a much larger operation using fake celebrity interviews and deceptive ads, which is run by a group called FizzCore (thanks to @vavkamil for pointing this out to me). The description of (for lack of a better term) TTPs of this actor provided in the analysis published by Confiant[5] fits the fake news page exactly.
Although the last campaign is quite interesting, neither it, nor either one of the previous ones, were unique. Similarly, forced multiple redirects to less than reputable sites are nothing new. Even though both of these statements are true, I found the brief look I was given into the world of current internet scams fairly informative… And I hope that you did as well.
[1] https://en.wikipedia.org/wiki/Spamdexing#Cloaking
[2] https://www.google.com/search?q=adsterra+scam
[3] https://ct24.ceskatelevize.cz/
[4] https://www.untrustednetwork.net/cs/2020/02/22/ct24_podvodna_stranka/
[5] https://blog.confiant.com/fake-celebrity-endorsed-scam-abuses-ad-tech-to-net-1m-in-one-day-ffe330258e3c


Comments
Anonymous
Feb 27th 2020
5 years ago
Anonymous
Mar 2nd 2020
5 years ago
trackers
landing, click
landing2 click several answers (useless no matter what you click)
landing3 rewards
coordinates, pay and get scammed 70$/month
MX = *.domain
SPAM FROM DOMAIN's IP - DOMAIN ISP
https://newtrackers.page.link/68kT
https://newtrackers.page.link/ngC1
https://trackmyclicks.page.link/EoMc
http://rammolemia.com/login/link.php?M=11973138&N=856&L=23&F=H
http://rammolemia.com/login/link.php?M=11973138&N=325&L=6&F=H
http://yoreirold.com/login/link.php?M=11973138&N=2&L=1&F=T
http://ractentmal.com/login/link.php?M=11973138&N=383&L=27&F=H
http://jocenfean.com/login/link.php?M=11973138&N=1900&L=25&F=H
http://jocenfean.com/login/link.php?M=11973138&N=2001&L=15&F=H
http://jocenfean.com/login/link.php?M=11973138&N=1900&L=25&F=H
PH https://www.virustotal.com/gui/url/e073fdc379318db90bd1e7715dc2a8d905710993f0e8ccb4867c34c0ccc836b7/detection
http://gieverrerl.com/login/link.php?M=11973138&N=653&L=6&F=H
http://gieverrerl.com/login/link.php?M=11973138&N=17&L=16&F=H
http://donfamasse.com/login/link.php?M=11973138&N=596&L=23&F=H
http://donfamasse.com/login/link.php?M=11973138&N=393&L=16&F=H
http://nortsesire.com/login/link.php?M=11973138&N=144&L=8&F=H
http://ginsailtry.com/login/link.php?M=11973138&N=539&L=16&F=H
http://beliciph.com/login/link.php?M=11973138&N=225&L=18&F=H
http://judarisour.com/login/link.php?M=11973138&N=358&L=1&F=H
http://judarisour.com/login/link.php?M=11973138&N=82&L=23&F=H
http://seditimsts.com/login/link.php?M=11973138&N=204&L=1&F=H
http://hananinons.com/login/link.php?M=11973138&N=76&L=9&F=H
http://uninaisotl.com/login/link.php?M=11973138&N=142&L=46&F=H
http://wesadan.com/login/link.php?M=11973138&N=209&L=23&F=H
http://esmorisans.com/login/link.php?M=11973138&N=14&L=13&F=H
http://guppena.com/login/link.php?M=11973138&N=618&L=6&F=H
http://elloneelo.com/login/link.php?M=11973138&N=1963&L=15&F=H
PH https://www.virustotal.com/gui/url/cd7cea7813880c3b26bbae222c84c8f66fa257b00a2cd8b7269e4435acc0b0f9/detection
http://welindyl.com/login/link.php?M=11973138&N=335&L=1&F=H
http://erileera.com/login/link.php?M=11973138&N=872&L=58&F=H
http://erileera.com/login/link.php?M=11973138&N=1178&L=66&F=H
PH M3 https://www.virustotal.com/gui/url/79dd94287f1b3d2a1bb7fd07fff2cd6b68b4231dbee93e20d05791edc9e5a4d1/detection
http://guidicelah.com/login/link.php?M=11973138&N=11&L=10&F=H
http://aoriton.com/login/link.php?M=11973138&N=142&L=1&F=H
PHISHING https://www.virustotal.com/gui/url/a155a427ca6edf2f8404b7468e77b8147a8d2112b098cb0f42a6b10da60aa978/detection
http://overthinkco.com/login/link.php?M=11973138&N=591&L=56&F=H
PH https://www.virustotal.com/gui/url/cbe169fc012ad27768252972ac32bf887377adb82f9a46d61e02314398962e48/detection
http://vascoak.com/login/link.php?M=11973138&N=2&L=1&F=H
http://kandrebe.com/login/link.php?M=11973138&N=142&L=1&F=H
http://snesarot.com/login/link.php?M=11973138&N=18&L=17&F=H
http://katienety.com/login/link.php?M=11973138&N=1618&L=5&F=H
http://rainchak.com/login/link.php?M=11973138&N=117&L=8&F=H
PH https://www.virustotal.com/gui/url/c441312b7ca812ef574d0aade3b7de2df77b3834ff1065a7c1b8865cdbca3eb3/detection
http://cenictarp.com/login/link.php?M=11973138&N=1424&L=5&F=H
http://averringstreet.com/login/link.php?M=11973138&N=45&L=12&F=H
http://omediaro.com/login/link.php?M=11973138&N=36&L=8&F=H
http://hasetaru.com/login/link.php?M=11973138&N=435&L=22&F=H
http://chacruater.com/login/link.php?M=11973138&N=14&L=12&F=H
PH https://www.virustotal.com/gui/url/557aec3b6dde11b368a5df0973a3e601bd968d7b3bcb6b31baff2eaa2b983953/detection
http://amporinya.com/login/link.php?M=11973138&N=1283&L=15&F=H
http://getfunsolutions.com/login/link.php?M=11973138&N=1023&L=77&F=H
PH https://www.virustotal.com/gui/url/1e0008fc456c4e66a26b13f9ffc84a2685b356dd59a38871ac942978069dc0f9/detection
http://hombealii.com/login/link.php?M=11973138&N=522&L=28&F=H
PH2 M2 https://www.virustotal.com/gui/url/ddf31a4e40eea00759ff82d8a5e2834e55293a1507f139e0fd57162405097752/detection
http://cenictarp.com/login/link.php?M=11973138&N=1030&L=15&F=H
http://detalapth.com/login/link.php?M=11973138&N=911&L=15&F=H
http://mewichort.com/login/link.php?M=11973138&N=837&L=1&F=H
http://dyaciaten.com/login/link.php?M=11973138&N=342&L=5&F=H
PH https://www.virustotal.com/gui/url/408e4227fedc4e0141c167f9f2c39f48ca20a1a3a98c3ca133c8c268936bd0c2/detection
http://cryptoonlineblog.com/login/link.php?M=11973138&N=649&L=47&F=H
http://cryptoonlineblog.com/login/link.php?M=11973138&N=649&L=47&F=H
http://manhasmadeof.com/login/link.php?M=11973138&N=558&L=44&F=H
http://manhasmadeof.com/login/link.php?M=11973138&N=558&L=44&F=H
PH https://www.virustotal.com/gui/url/68efd8a59cfdd61c9151ca2cf782feff87a100560d476a622ee72d3475e1dd72/detection
http://boyenoths.com/login/link.php?M=11973138&N=141&L=8&F=H
http://boyenoths.com/login/link.php?M=11973138&N=790&L=1&F=H
http://boyenoths.com/login/link.php?M=11973138&N=777&L=16&F=H
PH2 M3 https://www.virustotal.com/gui/url/8817225d67543d3ed7e652b823f7799d360a7ad1c266c36f1921607ffef5bb41/detection
PH2 M3 https://www.virustotal.com/gui/url/e10315c658d0961f52584990975fff82f43a688712afc828bb688d134be764d9/detection
http://icecoleek.com/login/link.php?M=11973138&N=291&L=28&F=H
PH2 M3 https://www.virustotal.com/gui/url/96202b4c25e80027fe166c3cf94ff88b100d1fc67326cf3fb2b81e691cb76929/detection
http://flowneduc.com/login/link.php?M=11973138&N=769&L=25&F=H
http://kamullaid.com/login/link.php?M=11973138&N=730&L=16&F=H
http://tographygraphy.com/login/link.php?M=11973138&N=686&L=45&F=H
DO = DIGITALOCEAN
HZ = Hetzner Online GmbH
ALL: PREFERRED REGISTRAR BY CROOKS... NameCheap!!!!!!!!!!!
CREATED: 2020 January OR February
IP Domain Country ISP
204.48.28.88 amporinya.com USA DO
167.71.159.65 aoriton.com USA DO
178.62.222.250 averringstreet.com Netherlands DO
142.93.252.137 beliciph.com USA DO
178.62.33.164 boyenoths.com UK DO
157.245.37.14 cenictarp.com UK DO
165.227.188.87 chacruater.com USA DO
64.227.90.207 cryptoonlineblog.com USA DO
134.209.200.61 detalapth.com Netherlands DO
159.203.30.6 donfamasse.com Canada DO
188.166.72.139 dyaciaten.com Netherlands DO
128.199.146.216 elloneelo.com Singapore DO
159.203.27.71 erileera.com Canada DO
178.62.35.135 esmorisans.com UK DO
157.245.34.234 flowneduc.com UK DO
88.198.228.21 getfunsolutions.com Germany HZ
142.93.152.22 gieverrerl.com Canada DO
68.183.202.1 ginsailtry.com Canada DO
64.227.38.229 guidicelah.com UK DO
64.225.60.62 guppena.com USA DO
64.225.13.137 hananinons.com USA DO
157.230.254.113 hasetaru.com Singapore DO
167.71.197.163 hombealii.com Singapore DO
142.93.9.172 icecoleek.com USA DO
159.203.173.60 jocenfean.com USA DO
67.205.155.93 judarisour.com USA DO
64.225.122.225 kamullaid.com USA DO
128.199.200.170 kandrebe.com Singapore DO
64.227.56.255 katienety.com USA DO
88.198.213.165 manhasmadeof.com Germany HZ
178.128.147.112 mewichort.com USA DO
64.227.12.1 nortsesire.com USA DO
159.203.11.240 omediaro.com Canada DO
206.189.220.46 overthinkco.com USA DO
64.225.69.174 ractentmal.com Netherlands DO
157.245.44.2 rainchak.com UK DO
138.68.76.90 rammolemia.com Germany DO
167.172.52.205 seditimsts.com UK DO
128.199.211.62 snesarot.com Singapore DO
78.47.207.236 tographygraphy.com Germany HZ
167.172.218.52 uninaisotl.com USA DO
165.227.91.127 vascoak.com USA DO
188.166.91.185 welindyl.com Netherlands DO
157.245.66.121 wesadan.com Netherlands DO
159.203.26.43 yoreirold.com Canada DO
amporinya.com
aoriton.com
averringstreet.com
beliciph.com
boyenoths.com
cenictarp.com
chacruater.com
cryptoonlineblog.com
detalapth.com
donfamasse.com
dyaciaten.com
elloneelo.com
erileera.com
esmorisans.com
flowneduc.com
getfunsolutions.com
gieverrerl.com
ginsailtry.com
guidicelah.com
guppena.com
hananinons.com
hasetaru.com
hombealii.com
icecoleek.com
jocenfean.com
judarisour.com
kamullaid.com
kandrebe.com
katienety.com
manhasmadeof.com
mewichort.com
nortsesire.com
omediaro.com
overthinkco.com
ractentmal.com
rainchak.com
rammolemia.com
seditimsts.com
snesarot.com
tographygraphy.com
uninaisotl.com
vascoak.com
welindyl.com
wesadan.com
yoreirold.com
Anonymous
Mar 10th 2020
5 years ago