Offensive Tools Are For Blue Teams Too
Many offensive tools can be very useful for defenders too. Indeed, if they can help to gather more visibility about the environment that must be protected, why not use them? More information you get, more you can be proactive and visibility is key. A good example is the combination of a certificate transparency list[1] with a domain monitoring tool like Dnstwist[2], you could spot domains that have been registered and associated with a SSL certificate: It's a good indicator that an attack is being prepared (like a phishing campaign).
A tool got more attention recently event if now brand new: "Amass" from the OWASP project[3]. This tool is easy to install, easy to be “Dockerised” and there is also a package available on Kali. Amass is a reconnaissance tool that helps to gather information about your “target” if you’re on the Red side or, if you're on the Blue side, to have an overview of your Internet exposure.
The tool is easy to setup via a single configuration file. The key point is to configure your API keys and credentials for the available services that will be queried. Some of them (the list of not complete):
- Spyse
- Sublist3rAPI
- ThreatCrowd
- URLScan
- ViewDNS
- VirusTotal
- Pastebin
- DNSDB
- Netcraft
- AlienVault
- Censys
- CertSpotter
You use the tool with submodules:
- iIntel’ to collect OSINT
- ‘enum’ to perform DNS network mapping
- ‘viz’ to vizualize gathered data
- ‘track’ to compare results between executions (this one is key for Blueteamers!)
Many command line arguments are available, please check the documentation for a complete overview[4].
Let’s start with the enumeration of a well-known domain: sans.edu.
root@kali:/tmp# amass enum -ip -src -brute -min-for-recursive 2 -d sans.edu Querying Spyse for sans.edu subdomains Querying Sublist3rAPI for sans.edu subdomains ... Querying ThreatCrowd for sans.edu subdomains Querying URLScan for sans.edu subdomains Querying ViewDNS for sans.edu subdomains Querying VirusTotal for sans.edu subdomains [Crtsh] isc.sans.edu 45.60.103.34,45.60.31.34 [Crtsh] sans.edu 45.60.31.34,45.60.103.34 [Censys] www.sans.edu 45.60.33.34 [Crtsh] apply.sans.edu 72.55.140.155 [Google] isctv.sans.edu 45.60.103.34,45.60.31.34 Starting DNS queries for brute forcing [Crtsh] handlers.sans.edu 74.208.193.6 [ThreatCrowd] www3.sans.edu 204.51.94.213 [Riddler] pre-www.sans.edu 204.51.94.213 [Riddler] search.sans.edu 204.51.94.41 [BufferOver] s120-www.sans.edu 204.51.94.126 [ThreatCrowd] pre-isc31.sans.edu 204.51.94.153 [ThreatCrowd] isc31.sans.edu 204.51.94.153 [IPv4Info] isc32.sans.edu 204.51.94.154 [ThreatCrowd] www2.sans.edu 66.35.59.213 Starting DNS queries for altered names [Alterations] s123-www.sans.edu 204.51.94.126 [Alterations] pre-isc3.sans.edu 204.51.94.233 ... [Alterations] s82-www.sans.edu 204.51.94.126 [Alterations] s55-www.sans.edu 204.51.94.225 [Riddler] lyncdiscover.sans.edu 52.112.192.14,2603:1027:0:2::e [Brute Forcing] autodiscover.sans.edu 52.97.186.152,52.97.232.216,52.97.186.120,2603:1026:200:3d::8,2603:1026:206:4::8,2603:1026:206:7::8 [Alterations] s86-www.sans.edu 204.51.94.126 ... [Alterations] s128-www.sans.edu 204.51.94.126 [Alterations] s12-www.sans.edu 204.51.94.246 Average DNS queries performed: 1695/sec, DNS names queued: 0 Average DNS queries performed: 1068/sec, DNS names queued: 0 Average DNS queries performed: 4/sec, DNS names queued: 0 OWASP Amass v3.3.1 https://github.com/OWASP/Amass -------------------------------------------------------------------------------- 71 names discovered - cert: 5, scrape: 5, api: 5, alt: 55, brute: 1 -------------------------------------------------------------------------------- ASN: 19551 - INCAPSULA, US 45.60.103.0/24 3 Subdomain Name(s) 45.60.31.0/24 3 Subdomain Name(s) 45.60.33.0/24 1 Subdomain Name(s) ASN: 32613 - IWEB-AS, CA 72.55.128.0/18 1 Subdomain Name(s) ASN: 8560 - ONEANDONE-AS Brauerstrasse 48, DE 74.208.0.0/16 1 Subdomain Name(s) ASN: 62669 - SANS INSTITUTE (SANSI-1) 66.35.59.0/24 2 Subdomain Name(s) 204.51.94.0/24 61 Subdomain Name(s) ASN: 8075 - MICROSOFT-CORP-MSN-AS-BLOCK, US 52.112.0.0/14 1 Subdomain Name(s) 2603:1000::/25 4 Subdomain Name(s) 52.96.0.0/12 3 Subdomain Name(s)
You can see that many interesting information are returned. I like the overview of the Autonomous Systems detected. Sometimes, it’s a good indicator to discover that some services are hosted in cloud services!
The next step is to generate some visual representation of data we collected:
root@kali:/tmp# amass viz -d sans.edu -d3
There are other export formats like a Maltego one. The result is a file called ‘amass_d3.html’ that can be viewed in any browser:
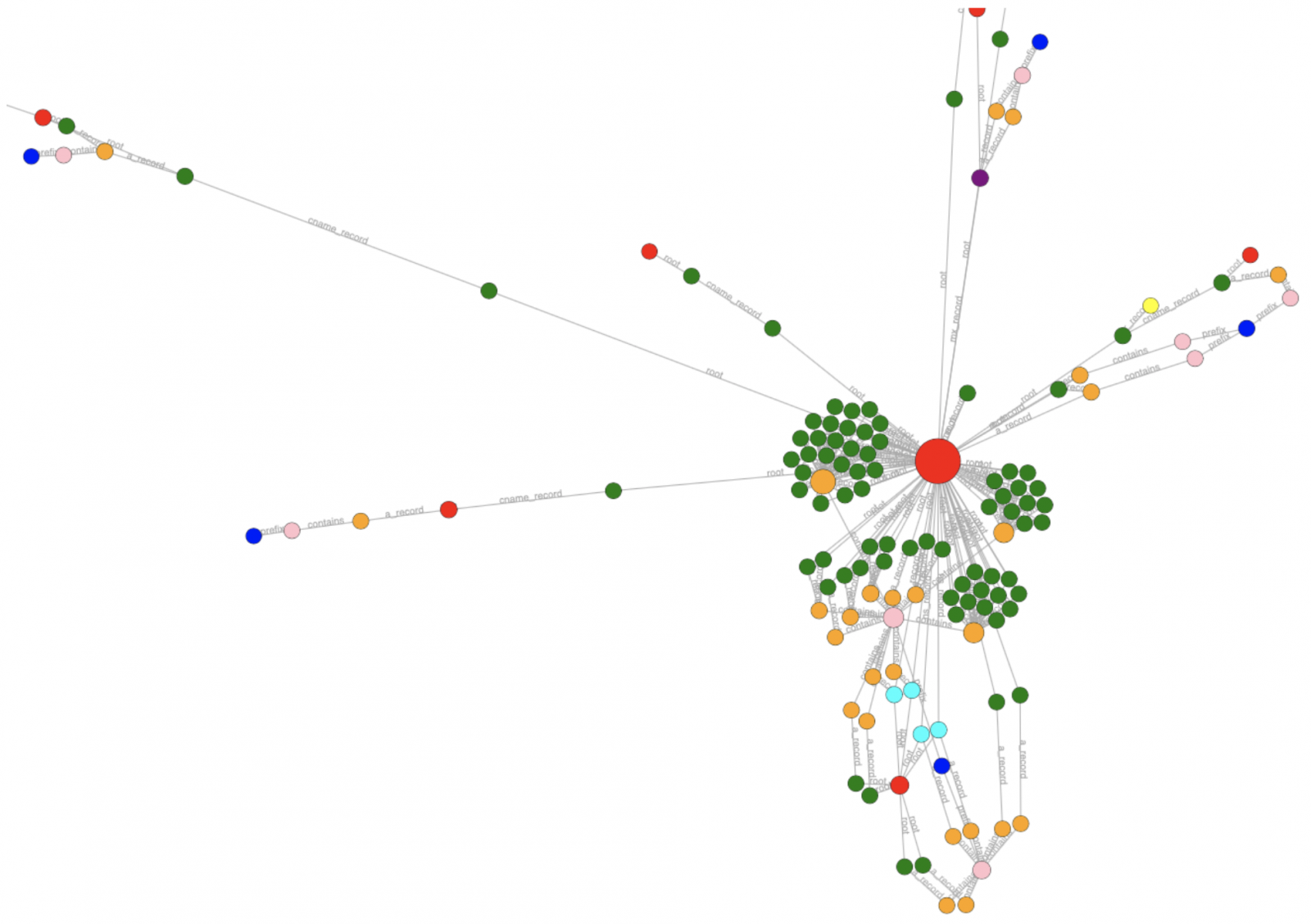
From a Blue team point of view, the ’track’ sub-module is the most interesting because it helps to find changes that occurred between different enumerations:
root@kali:/tmp# amass track -d sans.edu -------------------------------------------------------------------------------- Between 02/26 18:33:09 2020 CET -> 02/26 18:36:19 2020 CET and 02/26 18:14:47 2020 CET -> 02/26 18:33:09 2020 CET -------------------------------------------------------------------------------- Moved: lyncdiscover.sans.edu from 52.112.192.14,2603:1027:0:2::e to 52.112.193.16,2603:1027:0:2::e Moved: autodiscover.sans.edu from 40.101.82.72,2603:1026:c0d:20::8,40.101.80.200,2603:1026:c0d:2a::8,2603:1026:c0b:16::8,52.97.176.40 to 2603:1026:207:14f::8,40.101.80.24,40.101.12.24,2603:1026:207:a7::8,2603:1026:206:8::8,40.101.12.136 Found: s13-www.sans.edu 204.51.94.225 Found: s6-www.sans.edu 204.51.94.246 Found: mp3.sans.edu 204.16.246.222 Found: s23-www.sans.edu 204.51.94.225 Found: s8-www.sans.edu 204.51.94.246 Found: s7-www.sans.edu 204.51.94.225 Found: s127-www.sans.edu 204.51.94.126 Found: s25-www.sans.edu 204.51.94.225 Found: s84-www.sans.edu 204.51.94.126 Found: pre-www31.sans.edu 204.51.94.125 Found: s89-www.sans.edu 204.51.94.126 Found: s83-www.sans.edu 204.51.94.126 Found: pre-www2.sans.edu 66.35.59.213 Found: s17-www.sans.edu 204.51.94.225 Found: s78-www.sans.edu 204.51.94.126 Found: s126-www.sans.edu 204.51.94.126 Removed: s90-www.sans.edu 204.51.94.126
Based on this, you can perform a quick scan of all discovered devices:
root@kali:/tmp# amass db -show -d sans.edu 2>/dev/null | grep sans.edu | while read HOST; do nmap -sC -v -Pn $HOST; done
About the integration with other tools, Amass (in enum mode) can dump results to a JSON file that can be easily re-used (ex: indexed in a Splunk) to maintain a list of assets.
Conclusion, there are many tools around that could have a real value for Blue teams!
Tip: Amass makes an intensive use of DNS! I recommend you to use one of the public DNS servers (1.1.1.1, 8.8.8.8, 9.9.9.9, etc) to not abuse your local resolvers.
[1] https://isc.sans.edu/forums/diary/Using+Certificate+Transparency+as+an+Attack+Defense+Tool/24114
[2] https://dnstwister.report/
[3] https://github.com/OWASP/Amass
[4] https://github.com/OWASP/Amass/blob/master/doc/user_guide.md
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments