Malspam pushing coin miner and other malware
Introduction
Earlier today, @killamjr informed about a file with this SHA256 hash:
It's a JavaScript downloader, and it originated from a wave of malspam with zip attachments. Upon further investigation, the malspam had an error in the final boundary marker, so the attachment would not properly display in an email client until I fixed it.
Today's diary looks at the malspam and associated infection traffic.
The malspam and attachments
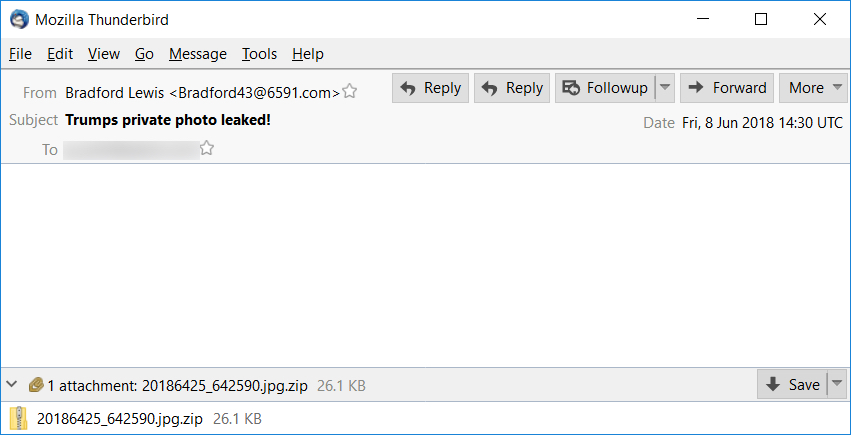
Shown above: Example of an email from this wave of malspam.
These emails had no message text, and they only contained an attached zip archive. The zip archive contained a JavaScript (.js) file. When extracted and double-clicked on a vulnerable Windows host, the .js file caused Windows Script Host to download and install malware.
My infected lab host also turned into a malspambot, and it sent similar messages out. Below are 20 examples of the senders and subject lines I saw from my infected lab host:
- From: Aida Davis <Aida33@2447.com> - Subject: Is she hot? Take a look at her
- From: Aida Perez <Aida78@5781.com> - Subject: Keep this photo private please
- From: Beulah Johnson <Beulah41@3710.com> - Subject: Rate my new photo please
- From: Billie Roberts <Billie37@6139.com> - Subject: Someone told me it's you???
- From: Blaine Howard <Blaine47@6150.com> - Subject: Someone takes photos from you
- From: Blair Nelson <Blair23@6150.com> - Subject: Your best photo
- From: Bob Brooks <Bob99@5457.com> - Subject: Please rate my picture
- From: Bobbi Bailey <Bobbi03@6591.com> - Subject: Damn I can't get her out my head
- From: Bradford Lewis <Bradford43@6591.com> - Subject: Trumps private photo leaked!
- From: Deanne Thomas <Deanne27@5457.com> - Subject: Is this you?
- From: Debbie Mitchell <Debbie54@8298.com> - Subject: Time for a change
- From: Debora Peterson <Debora09@6591.com> - Subject: Why you took that picture?!
- From: Deena Cook <Deena39@5356.com> - Subject: Unbelivable photo
- From: Delia Wright <Delia16@8298.com> - Subject: Your opinion needed
- From: Goldie Gray <Goldie39@2664.com> - Subject: Photo of my new girlfriend
- From: Gordon Rogers <Gordon67@6943.com> - Subject: Took photo of you
- From: Tania Roberts <Tania15@4347.com> - Subject: I simply love this photo of you!
- From: Tanner Thomas <Tanner95@3432.com> - Subject: LOL seen this photo?
- From: Tara Wood <Tara09@9774.com> - Subject: My love for you
- From: Teresa Cook <Teresa57@5781.com> - Subject: My picture
Each message from my malspambot had the same zip attachment that contained the same .js file. It had a different file hash than the one I originally infected my lab host with, but it was basically the same file.
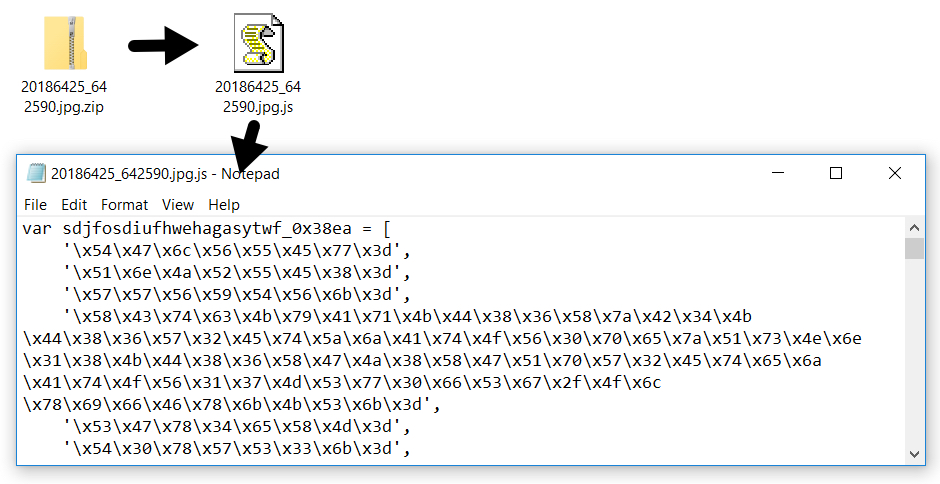
Shown above: Attachment from the malspam.
Traffic from my infected lab host
After double-clicking the .js file, I saw several HTTP requests for malware. One of the HTTP requests returned a .js file used in attachments from malspam sent by my newly-infected Windows host. Another HTTP request returned a mailing list of recipients to send the malspam.
In addition to SMTP traffic on TCP port 25, I also saw post-infection traffic for a Monero coin miner (XMRig).
I found an error in the final boundary line at the end of all emails sent by my infected lab host. That line had an extra dash (3 instead of 2 dashes) to close out the message. This made the attachment unreadable to any normal email client. If the message made it to its intended recipient, the recipient would probably see a blank message.

Shown above: HTTP requests from the infection traffic as seen in Wireshark.

Shown above: Post-infection traffic for a Monero coin miner.
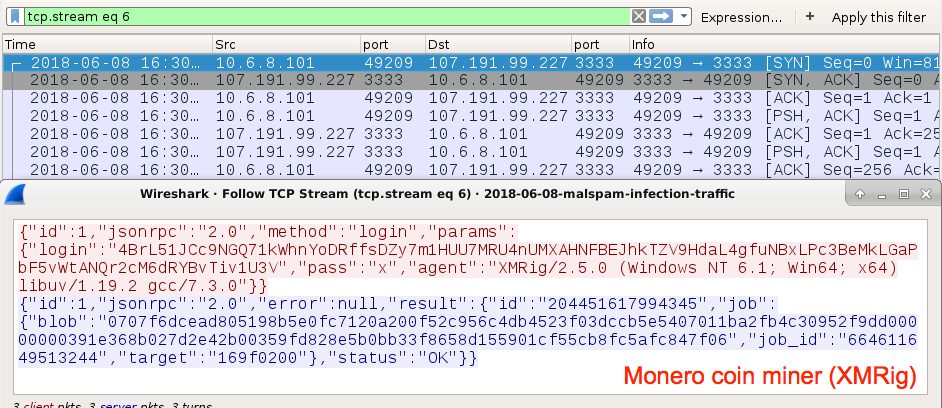
Shown above: Following one of the TCP streams for the coin miner traffic.
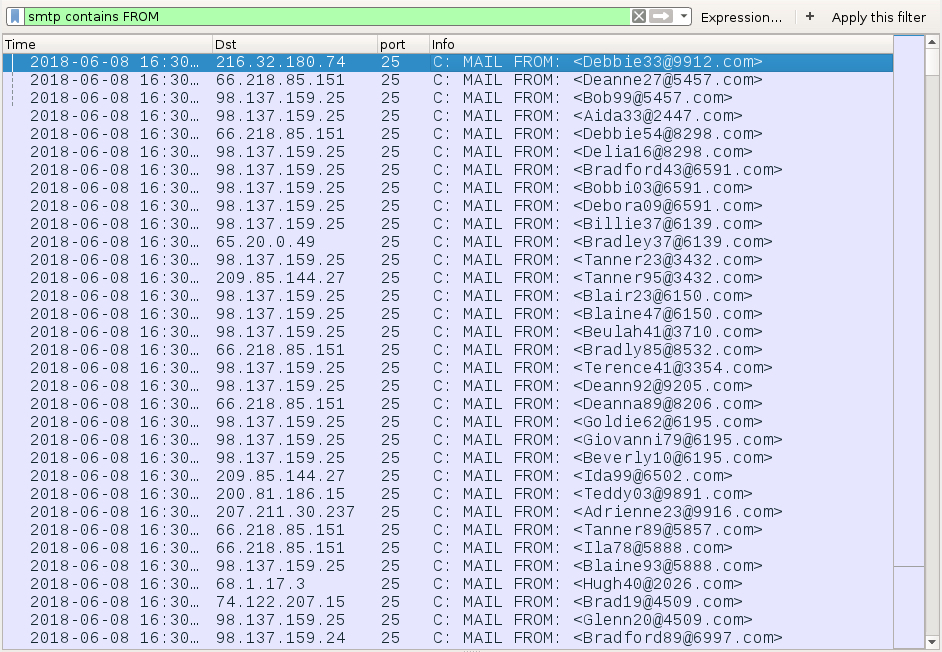
Shown above: Filtering on SMTP traffic to find the spoofed sending addresses.
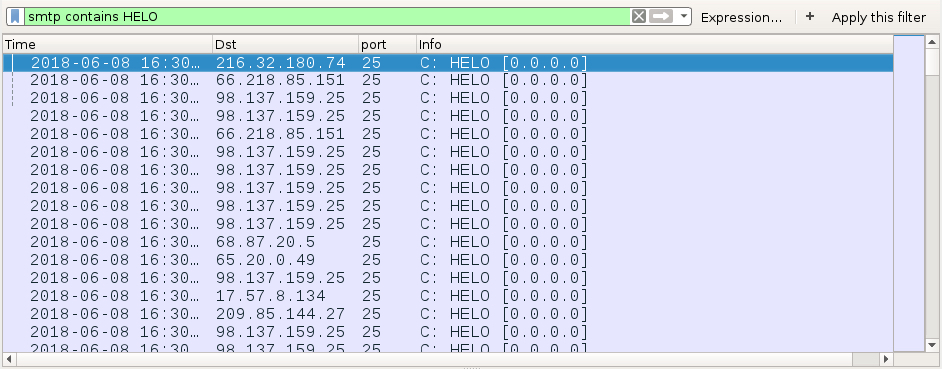
Shown above: Filtering on SMTP traffic to find spoofed hosts used when contacting the recipient's mail server.
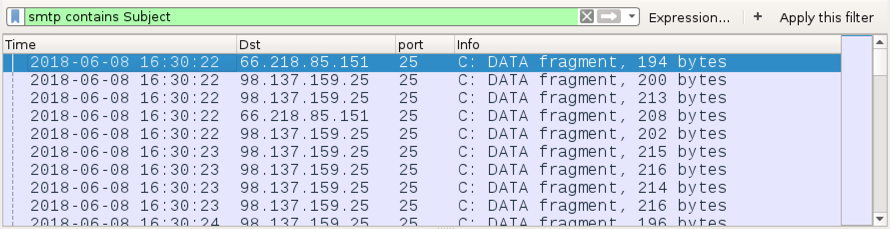
Shown above: Filtering on smtp contains Subject (case sensitive) shows several emails that were not outright rejected.
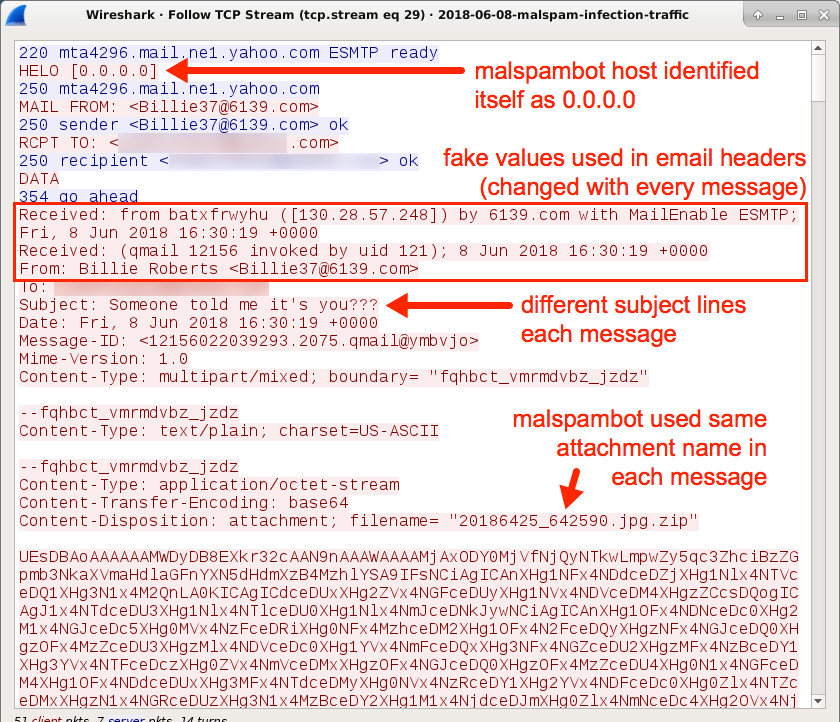
Shown above: Following the TCP stream for one of the malspam messages.
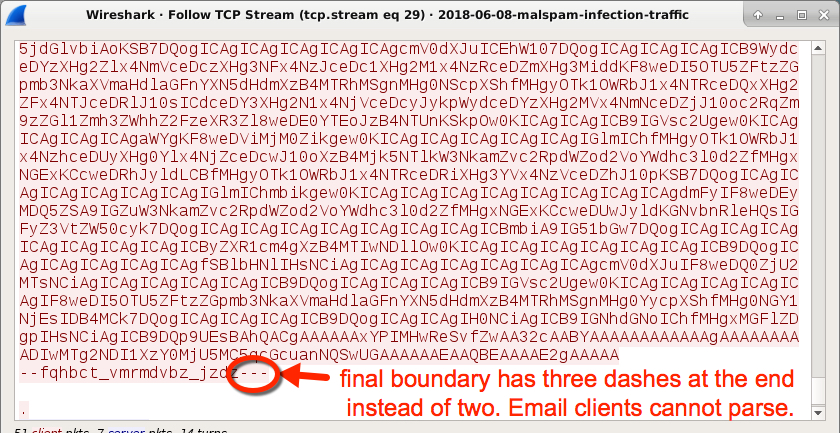
Shown above: Near the bottom of the TCP stream, you see the error in the closing boundary tag.
Forensics on an infected Windows host
I used a Windows 7 host for the infection traffic. I was unsuccessful when I tried infecting a Windows 10 host. My infected Windows 7 host had registry entries to keep the malware persistent. One of the malware binaries was also saved to a USB drive that happened to be plugged into the infected lab host.
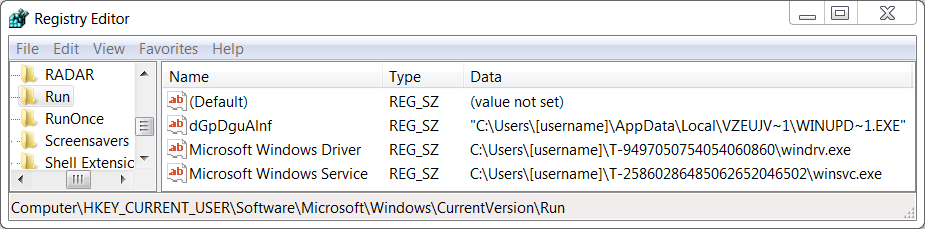
Shown above: Registry entries on my infected Windows 7 host.

Shown above: Contents of a USB thumb drive taken from my infected Windows 7 host.
Indicators
The following are indicators found during my investigation:
SHA256 hash: 4412d28a156716d16eb684ea4699a69f06f0346d99c23cd84065433252f02b99
- File size: 26,219 bytes
- File description: Original .js file I was notified about
SHA256 hash: 2e5674a738e1409d32a559d4bddcff3243fdf68b4fc4482b29dff38dfa6e3dc1
- File size: 26,591 bytes
- File location: hxxp://92.63.197.60/d.js
- File description: Malicious JavaScript from malspam sent by my malspambot lab host
SHA256 hash: 3c0fd1377e620229daa0175758112f712f54474db2135c695761afffef6510ea
- File size: 26,733 bytes
- File name: 20186425_642590.jpg.zip
- File description: The actual zip attachment in malspam sent by my malspambot lab host
SHA256 hash: 1be4cbc9f9b6eea7804e08df92cff7453aa72f0bb862b0fb8f118c5e3ffdaad6
- File size: 168,960 bytes
- File location: hxxp://92.63.197.60/c.exe
- File description: malware (unspecified)
SHA256 hash: 73f0880358701566ed1792014b639c02f357da42981344a6ad644aae494d3e36
- File size: 808,960 bytes
- File location: hxxp://92.63.197.60/m.exe
- File description: Cryptocurrency miner (Monero)
SHA256 hash: fdb9eacca47469ddb1d91694171fb1df8f891fb12a6c6a8184a5def539784cc6
- File size: 172,032 bytes
- File location: hxxp://92.63.197.60/o.exe
- File description: malware (unspecified)
SHA256 hash: 1437e8518c62383d57fd38debdad1a76813c229061d3aa060c2f3151eac41027
- File size: 219,648 bytes
- File location: hxxp://92.63.197.60/t.exe
- File description: malware (unspecified)
Network traffic from the infection:
- 92.63.197.60 over TCP port 80 - 92.63.197.60 - follow-up malware and other traffic
- 198.105.244.228 over TCP port 80 - booomaahuuoooapl.ru - attempts at same downloads as seen with 92.63.197.60
- 107.191.99.227 over TCP port 3333 - monerohash.com - XMRig traffic (Monero coin miner)
- various IP addresses over TCP port 25 - SMTP traffic from my newly-infected malspambot host
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. The boundary errors in these malspam messages probably ensured none of the intended recipients even saw the malware. Furthermore, system administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Of note, email headers from this malspam are similar to what I've seen with the "Zero Gand" campaign in previous months. Today's wave of malspam probably used the same distribution channel as that earlier campaign.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments