Machine Code? No!
On the 4th of July, I posted diary entry "Machine Code?" with the following screenshot:
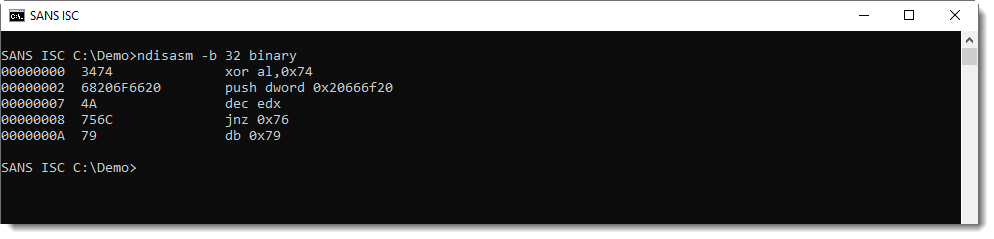
This is disassembler output from the "Netwide Assembler" for 32-bit code.
What was the content of file binary? This:
4th of July
I wanted to illustrate that a x86 disassembler will always produce output, even if you provide it input that is "not real" machine code.
Some time ago, I had a friend analyze a capture file: suspecting an exploit, he took the data out of a TCP packet and disassembled it. He was not familiar with assembler code or machine language, but since the disassembler produce a listing (without errors), he concluded that the data he found in that packet must be shellcode.
I explained to him that this was not the case: a disassembler will do its best to produce a listing whatever input you give it. It's up to the analyst to understand the purpose of the disassembled program, and decide if is indeed a program at all.
And that's not easy, it requires skill, especially with obfuscated shellcode.
If you don't have these skills, then there are still other methods you can use to determine if you are dealing with shellcode. One method is dynamic analysis: execute it, and see what happens.
I refer to diary entry "Analyzing Encoded Shellcode with scdbg" if you want to know more.
Conclusion: being able to produce a disassembly listing is not a reliable detection method for shellcode.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Following on from what you describe, I found this pretty comprehensive:
https://www.fireeye.com/blog/threat-research/2017/12/recognizing-and-avoiding-disassembled-junk.html
Anonymous
Jul 12th 2019
6 years ago
Anonymous
Jul 15th 2019
6 years ago