MISP - Malware Information Sharing Platform
In a previous diary (“Unity Makes Strength”), I briefly mentioned MISP (which means "Malware Information Sharing Platform"). Since this tool is becoming more and more popular, I’d like to give more details about it. “Sharing is key” could be the slogan of MISP. The idea is to allow different organizations to share IOC’s ("Indicators of Compromize) like IP addresses, domains, hashes, URLs, filenames, ... The goal is to increase their ability to protect themselves against malicious activities. With millions of new samples spread in the wild everyday, new domain generation algorithms (DGA’s) and ever-changing C2 topologies, it’s mandatory to join our forces to fight the bad guys.
The core components of MISP are classic: a database and a web interface which looks like a classic ticketing system where people can manage their IoC’s:
.png)
But, with the growing amount of data to manage, the key is automation. MISP has many ways to be interconnected to 3rd party systems. How? MISP offers a great REST API to manage IOC’s in both ways. It can generate:
- Snort/Suricata IDS rules
- STIX
- OpenIOC
- Text of CSV exports.
In the other way, manual input of new IOC’s can be a real pain. They can be imported using:
- A free-text tool
- OpenIOC
- Batch import
- Directly from some sandbox (ex: GFI)
Here is an example of REST API call to extract a list of malicious domains:
#!/usr/bin/python import urllib2 authkey = '' req = urllib2.Request('https://127.0.0.1/events/csv/download/false/false/!splunk_ignore/Network%20activity/domain/false/false/false/5d') req.add_header('Authorization', authkey) res = urllib2.urlopen(req) content = res.read() print content
This simple Python script extracts the list of malicious domains for the last 5 days:
$ python misp_get_domains.py uuid,event_id,category,type,value,comment,to_ids,date 57309706-6d88-45cd-9fe3-49d1950d210f,2372,Network activity,domain,"coffeol.com","C2s",1,20160509 57309707-363c-447a-afdb-4648950d210f,2372,Network activity,domain,"updo.nl","C2s",1,20160509 57320a09-aa54-4ee2-99cc-409c95ca48b7,2375,Network activity,domain,"eclipse-upload.com","",1,20160510 57321711-6100-49c4-bc16-573295ca48b7,2376,Network activity,domain,"goog-upps.pw","Imported via the freetext import.",1,20160510 57321711-6454-4801-840e-573295ca48b7,2376,Network activity,domain,"new-uppdate.pw","Imported via the freetext import.",1,20160510 57321713-feac-460e-8c63-573295ca48b7,2376,Network activity,domain,"google-market2016.com","Imported via the freetext import.",1,20160510 57321719-5144-466e-9bba-573295ca48b7,2376,Network activity,domain,"android-update16.pw","Imported via the freetext import.",1,20160510 5732171a-1404-41b5-8eb1-573295ca48b7,2376,Network activity,domain,"android-update14.pw","Imported via the freetext import.",1,20160510 5732171a-28d4-4700-9491-573295ca48b7,2376,Network activity,domain,"android-update15.pw","Imported via the freetext import.",1,20160510 ...
But, the most interesting feature is maybe the integration of MISP instances between organizations. I’m running a local MISP instance which is synchronized with other ones. I’ll receive automatically new IOCs but all my locally created data will be spread to my “peers”. But, even if sharing is key, there are always some data that must remain inside an organization for multiple purposes. Some organizations will not share all information with me and same for me. There are ways to implement granularity and share only what you want (ex: based on TLP). You can also choose how the events will be distributed across communities:
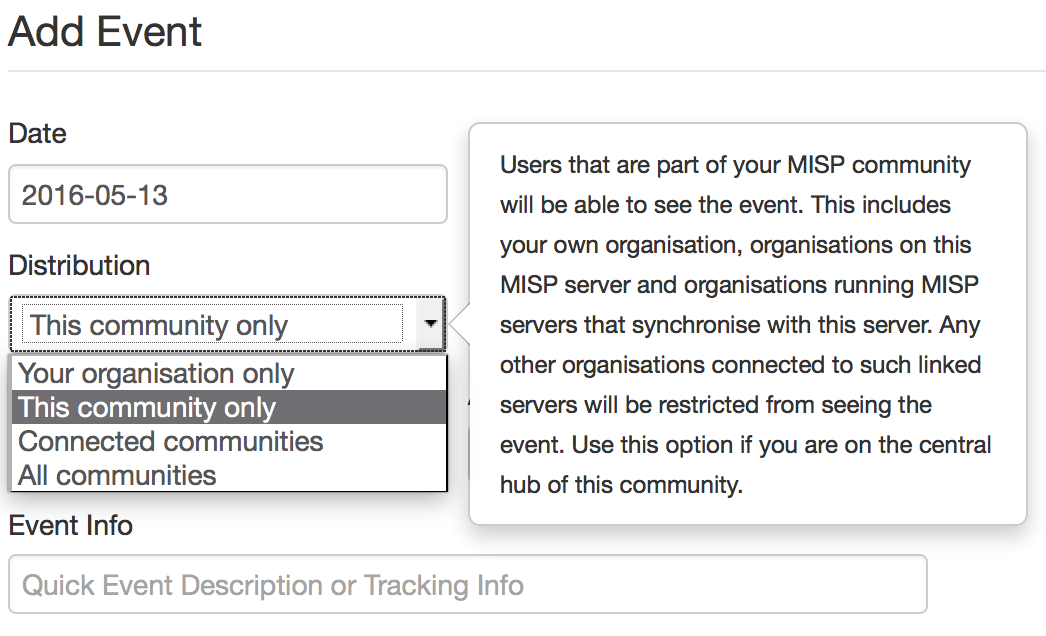
Today, MISP is more and more deployed and used by CERTs but also private organizations who need to increase their ability to detect malicious activity on their networks. The official MISP website is: misp-project.org. If you want to test it, I’m also maintaining a Docker container ready to use. And you? Do you already use MISP? How did you integrate it within your defense layers? Would you be interested to have access to a MISP instance?
My next class:
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |
×
![modal content]()
Diary Archives


Comments
Anonymous
May 13th 2016
9 years ago
Anonymous
May 13th 2016
9 years ago
For those interested in automation, there is a very nice python library called PyMISP.
It makes the job to talk to the API even more easy.
The code and examples can be found on GitHub: https://github.com/MISP/PyMISP
Anonymous
May 13th 2016
9 years ago
See also: https://github.com/MISP/misp.github.io
Anonymous
May 13th 2016
9 years ago
Anonymous
May 13th 2016
9 years ago
Anonymous
May 13th 2016
9 years ago