In Need of a OTP Manager Soon?
Even if everybody agrees to say that passwords are a weak way to protect access to sensitive or private information, they remain still today the default method implemented by many online services. A password, as complex as it may be, is easy to steal or leak. Tools like Mimikatz or memory scrappers[1] are common today. For a while, major players on the Internet started to implement two-factors authentication (2FA) or multi-factors authentication (MFA). Just to remind you, this authentication mechanism is based on a combination of:
- something "you know" (a password, a PIN or pass phrase)
- something "you have" (a token, a smart card)
- something "you are" (your fingerprint, retina, hand palm, …)
From a cost and ease of implementation point of view, the most common combination remains a password and a temporary code or "OTP". They are commercial solutions based on physical tokens but today with the explosion of smartphones, the Google Authenticator[2] and compatible applications became the most used platform. Once the application is installed, every time you activate the OTP feature on a compatible website, you scan a QR code and that’s it!
An alternative way (not available on all sites) is to use the Base32 or HEX key like on the ISC website:
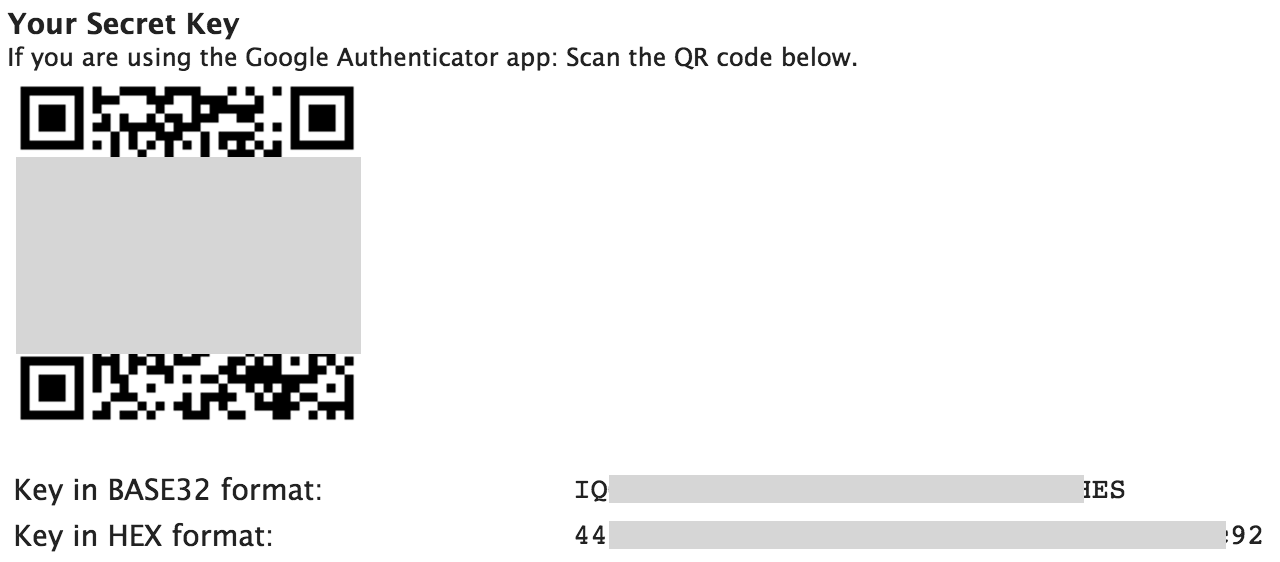
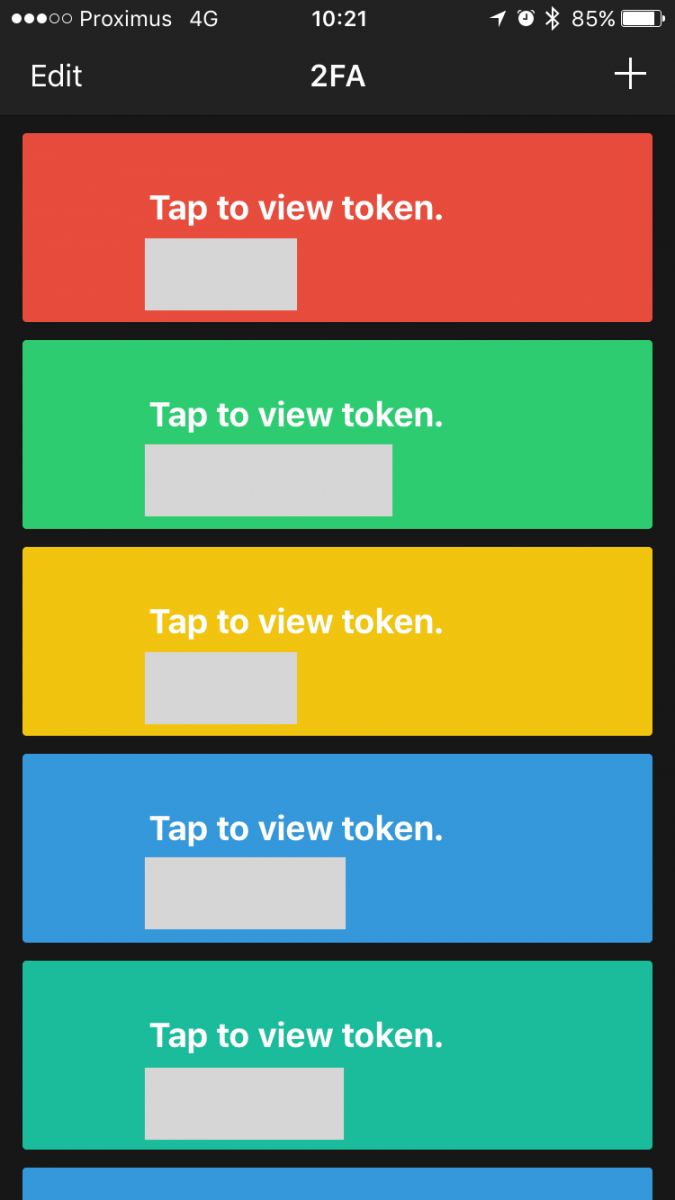
When available, I always enable OTP on my online accounts (Twitter, Github, Apple, Dropbox, … but also on my own resources like my blog or my private ownCloud). On my iPhone, I’m using the 2FA app because it has a simple GUI and it provides an Apple watch version (It is so convenient to have tokens just on your wrist!). But my collection of tokens is constantly growing:
I can’t imagine losing all those tokens! We use password managers for a while (well, I hope you do) but will we need a “OTP Manager” soon? The other question is: How to safely keep track and backup your tokens? They are available in your pocket but a smartphone is easy to loose, to be stolen or broken. Most websites propose a procedure to recover your access if you lost your token but there isn't a unique procedure: Some propose recovery codes (that must also be safely stored somewhere), emails or SMS code (and, guess what, usually the same phone is used to receive the recovery SMS).
Here are some best practices:
- Always read carefully the recovery procedure
- Copy / print backup codes
- Link your account to a mobile phone (to receive SMS)
- Link your account to a valid and rock-solid email address (not the one provided by your employer)
Personally, what I do:
- When the QR code is displayed on the website, I take a screenshot of the code and rename the picture QR_websitename_
.png When the Base32 or HEX key is provided, I write them in a text file KEY_websitename.txt Files are zipped, encrypted with my PGP key and stored offline Link the account to a different SIM / phone number that can be used in any old-fashioned phone
Note that some 2FA apps, like Authy, propose a backup solution (usually in the cloud - it's up to you to trust it or not). To conclude, OTP passwords are a good way to protect your accounts but have a good recovery procedure to avoid losing control of your accounts. And you? What how to you address this issue? Share your input!
[1] https://blog.blechschmidt.saarland/memory-recovery/
[2] https://support.google.com/accounts/answer/1066447
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Sep 16th 2016
9 years ago
This simply generates a url in the format otpauth://totp/mydomain.com?secret=UYMIODYLDUSYMBVV for time based and otpauth://hotp/mydomain.com?secret=UYMIODYLDUSYMBVV for counter based. This string is then encoded as a qr code.
Perhaps a better backup strategy would be to convert the qr code to a url and backup that.
Hélio Rosa
Anonymous
Sep 16th 2016
9 years ago
Anonymous
Sep 18th 2016
9 years ago
Anonymous
Sep 20th 2016
9 years ago
Anonymous
Sep 28th 2016
9 years ago