Fun with Passphrases!
As systems administrators and security folks, we've all had our fill of our users and customers using simple passwords. Most operating systems these days now enforce some level of password complexity by default, with options to "beef up" the password requirements for passwords.
The prevailing wisdom today is to use passphrases - demonstrated nicely by our bud at xkcd - http://xkcd.com/936/
So I routinely have very long pass phrases for public facing accounts. Imagine my surprise when I was creating a new account on major cloud service (the one that starts with an "O" and ends with a "365"), and found that I was limited to a 16 character password.
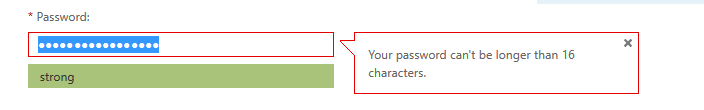
Needless to say I have a case open to see if that limit can be removed. I'm not looking for no limit / invitation to a buffer overflow status on the password field, but something bigger than 16 would really be appreciated !


Comments
Anonymous
Apr 24th 2014
1 decade ago
Anonymous
Apr 24th 2014
1 decade ago
Using the xkcd method, many passwords are hackable using oclhashcat. But bruteforcing all NTLM 8 lower chars+numbers is trivial, taking minutes. But luckily Microsoft is such a small company with no significant market presence, so they do not need to use salt, or use a good algorithm.
Anonymous
Apr 24th 2014
1 decade ago
http://social.technet.microsoft.com/Forums/lync/en-US/5343388f-c92c-46cc-9410-698739404af8/16-character-password-limitation-on-mac-lync-clients?forum=ocsclients
http://alexduggleby.com/2011/07/18/office-365-does-not-allow-more-than-16-character-passwords-or-why-why-why/
But does not explain why it is still limited.
Js
Anonymous
Apr 24th 2014
1 decade ago
Anonymous
Apr 24th 2014
1 decade ago
Anonymous
Apr 24th 2014
1 decade ago
Anonymous
Apr 24th 2014
1 decade ago
I visit a site that checks the "haystacks" and allows me to generate any length. Even with this one @ 16 QyM#rz[9'O<"IvO# returns this. On a 30 day rotational routine (yes a PITA, but breaches are worse) gives me some comfort. For those that wish to look up a decent article on wired, "kill the P@55W0rD" is a real eye opener and it dates back to 12-12.
But security, Admins even people with home systems hear complaints all the time.. I can't remember my PW, you create in DC too long and they lament. Feel like Gumby's arms.
WIth regards to cloud service.... heard of this? They will do it for you. Systems still running it.
https://support.microsoft.com/kb/2744850
http://www.h-online.com/security/news/item/Cloud-service-cracks-VPN-passwords-in-24-hours-1656104.html
https://github.com/moxie0/chapcrack
Search Space Depth (Alphabet): 26+26+10+33 = 95
Search Space Length (Characters): 16 characters
Exact Search Space Size (Count):
(count of all possible passwords
with this alphabet size and up
to this password's length) 44,480,886,725,444,
405,624,219,204,517,120
Search Space Size (as a power of 10): 4.45 x 1031
Time Required to Exhaustively Search this Password's Space:
Online Attack Scenario:
(Assuming one thousand guesses per second) 14.14 million trillion centuries
Offline Fast Attack Scenario:
(Assuming one hundred billion guesses per second) 1.41 hundred billion centuries
Massive Cracking Array Scenario:
(Assuming one hundred trillion guesses per second) 1.41 hundred million centuries
Anonymous
Apr 24th 2014
1 decade ago
It doesn't appear that they have any immediate intention of committing to a change which would allow for longer passwords.
Anonymous
Apr 24th 2014
1 decade ago
(I've changed the library site to a secure note in lastpass to "manage" my security score)
Anonymous
Apr 24th 2014
1 decade ago