Even Bad Malware Works
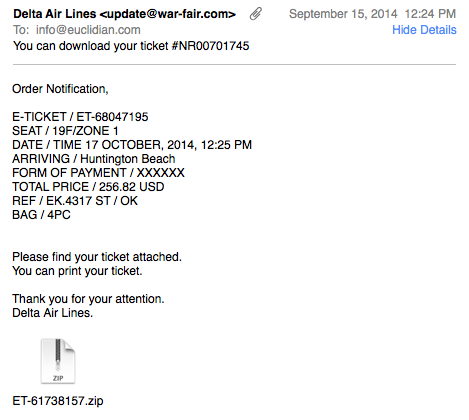
For a few weeks now, I keep receiving a few "Delta Ticket" e-mails a day with zipped executables as attachments. The e-mails are done about as bad as it gets:
- The "From" address uses a random domain
- The e-mail does not use the typical "Delta" formating/branding.
- The attachment is a straight executable, just zipped.
- Antivirus is ok on a new sample received right now (8/55 according to virustotal) and excellent (>30/55) on older samples. [1]
- The e-mail (flight information) is very specific and does not appear to be customized to the sender
- Delta doesn't send tickets as attachments like this.
So they could do a lot better. The sad part is, that they apparently have no need to do better.
The "From" name, which is what most people are looking at, reads "Delta Air Lines". Some major/popular AV tools still don't detect it well at all, and well, users like to click on stuff I guess.
The initial piece of malware appears to be a generic downloader. In my system, it installed what looked like a fake Adobe update. Still running it to see what is exactly going on, but not expecting too much.
[1] https://www.virustotal.com/en/file/4cf652e71bbbe37eecda58169471df27db15ca1e5a8f14006128a4883b095409/analysis/1410799974/
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
I was supposed to reply to a Gmail account?
Bank of Africa uses Gmail?
Anonymous
Sep 15th 2014
1 decade ago
Software restriction policies in Windows, however, has a lot of the qualities that are needed (e.g. free, built-in).
Anonymous
Sep 16th 2014
1 decade ago
Software restriction policies in Windows, however, has a lot of the qualities that are needed (e.g. free, built-in).
Anonymous
Sep 16th 2014
1 decade ago