DDOS is down, but still a concern for ISPs
For many reasons,most ISPs are finding that service affecting DDOSes, which were a common occurrence as little as a year ago are rare in the later half of 2015 and so far in 2016. Hopefully the arrest of some alleged members of DD4BC will also put a damper on the DDOS for ransom fad. That said DDOS is not dead. It appears booters services, DDOS for hire services with intent to be a nuisance for individual Internet users, are still a problem which ISPs worldwide are seeing.
The graph shows the common UDP traffic for one ISP.
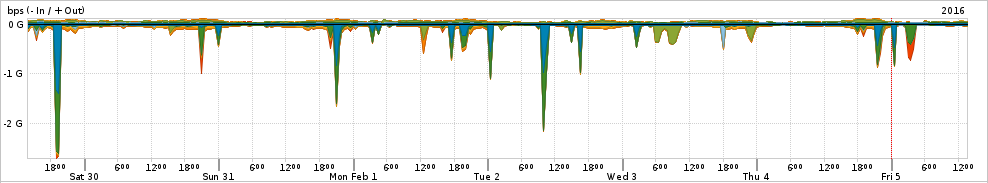
The large spikes show DDOS attacks, typically aimed at a single IP. As you can seen the traffic is typically a mix of DNS, port 0, with some chargen thrown in. For some reason SSDP, which was a large part of attacks in the recent past, has become a small part of the traffic mix in today's attacks.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments
1. One can't generalize from a single ISP's statistics. Take a look at the most recent WISR from Arbor Networks to get a more comprehensive view, based upon data from 300+ network operators worldwide:
http://www.arbornetworks.com/resources/annual-security-report
[Full disclosure: I work for Arbor Networks.]
2. The 'Port 0' UDP traffic you cite isn't UDP/0 - it's non-initial UDP fragments which are part of UDP reflection/amplification attacks such as SSDP, DNS, chargen, et. al. (not ntp). Most flow telemetry exporters represent it as port 0, but it means non-initial fragments, and flow telemetry collection/analysis systems should (but often don't) report it correctly.
I've logged into my SANS account, so I don't know why I'm being labeled as 'Anonymous' by the commenting system. My name is Roland Dobbins.
Anonymous
Feb 7th 2016
1 decade ago