Code Reuse In the Malware Landscape
Code re-use is classic behavior for many developers and this looks legit: Why reinvent the wheel if you can find some pieces of code that do what you are trying to achieve? If you publish a nice piece of code on platforms like GitHub, there are chances that your project will be used and sometimes forked by other developers who will add features, fix issues, etc. That's the magic of the Internet. But attackers are also looking for interesting code to borrow on GitHub. A few weeks ago, I wrote a diary about Excel Add-In's[1] used to distribute malware.
This morning,I spotted another campaign that uses the same technique. Emails are sent to victims asking them to have a look at important documents. The payload is delivered in a ZIP archive "Attachments.zip". The archive contains two XLL files:
remnux@remnux:/MalwareZoo/20220105$ unzip -t Attachments.zip
Archive: Attachments.zip
testing: Proposal Listing.xll OK
testing: Proposal Listing continue.xll OK
No errors detected in compressed data of Attachments.zip.
Both files are indeed Excel Add-In both for different architectures:
remnux@remnux:/MalwareZoo/20220105$ file Proposal\ Listing* Proposal Listing continue.xll: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows Proposal Listing.xll: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
These XLL files are interesting because they are based on a project called ExcelDNA:
remnux@remnux:/MalwareZoo/20220105$ pedump Proposal\ Listing\ continue.xll |tail -28 === VERSION INFO === # VS_FIXEDFILEINFO: FileVersion : 1.1.0.3 ProductVersion : 1.1.0.3 StrucVersion : 0x10000 FileFlagsMask : 0x17 FileFlags : 0 FileOS : 4 FileType : 2 FileSubtype : 0 # StringTable 080004b0: Comments : "Unmanaged loader shim for Excel-DNA Add-Ins" CompanyName : "Govert van Drimmelen" FileDescription : "Excel-DNA Dynamic Link Library" FileVersion : "1.1.0.3" InternalName : "ExcelDna" LegalCopyright : "Copyright (C) 2005-2020 Govert van Drimmelen" OriginalFilename : "ExcelDna.xll" ProductName : "Excel-DNA Add-In Framework for Microsoft Excel" ProductVersion : "1.1" VarFileInfo : [ 0x800, 0x4b0 ] === Packer / Compiler === MS Visual C++ 6.0 - 8.0
Searching for "Govert van Drimmelen" will redirect you to a GitHub project[2]. And to confirm the code re-use, we can search for code similarities:
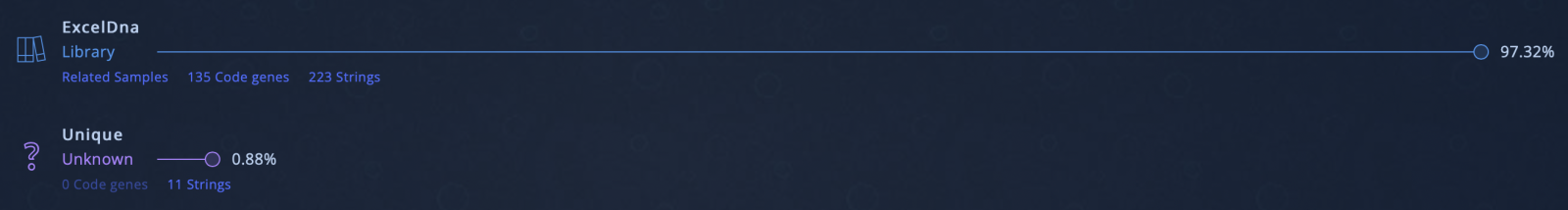
97% of the code is common with the ExcelDna sample Add-In! (Source: Intezer Analyze). The dropped malware is an info stealer. Malware families sometimes share a lot of "bad" code but malware developers are also looking for interesting "safe" code!
[1] https://isc.sans.edu/forums/diary/Downloader+Disguised+as+Excel+AddIn+XLL/28052
[2] https://github.com/govert/ExcelDna
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments