Another Maldoc? I'm Afraid So...
Guess what? Yep, there's yet another type of malicious document going around. Like last time, it's a MIME file with an MSO file containing an OLE file.
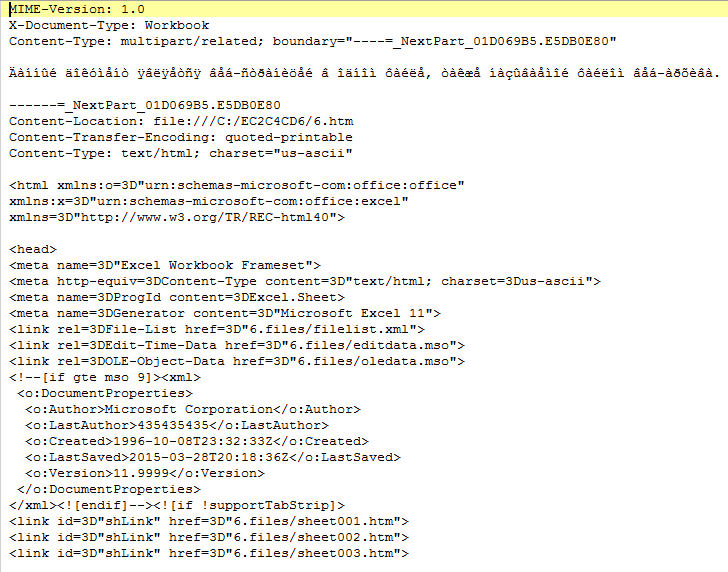
The sample (schro_193B11.xls 7F8C5E8B7157B04FA8E9CEEF13C28AB9) is an Excel spreadsheet saved as a MIME file:
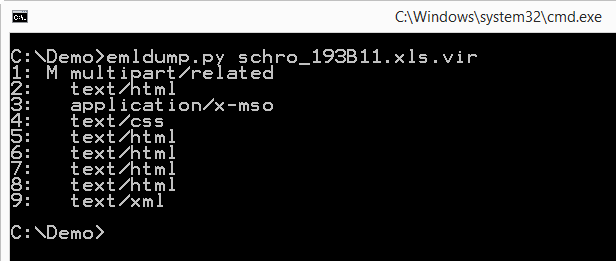
But this time, the compressed data is at another position inside the MSO file:

So I updated my oledump tool (V0.0.16) to search for compressed data inside MSO files (in stead of looking at a fixed position 50).
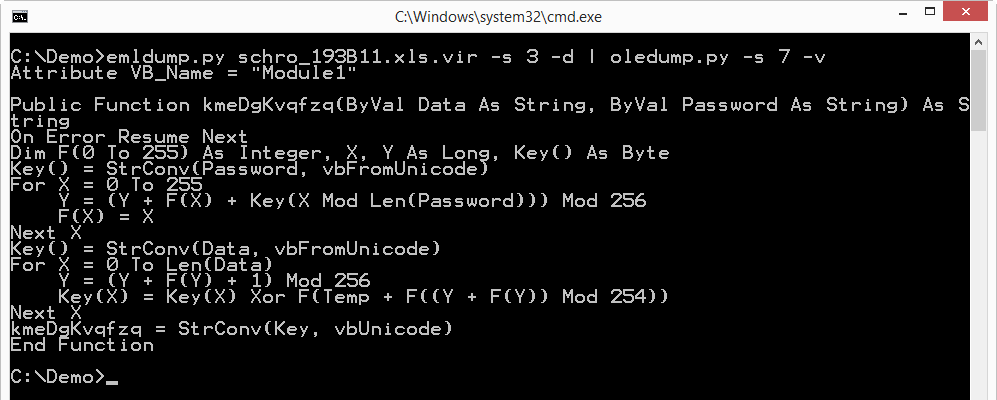
The string encoding used in the VBA code is interesting. It is reminiscent of RC4:
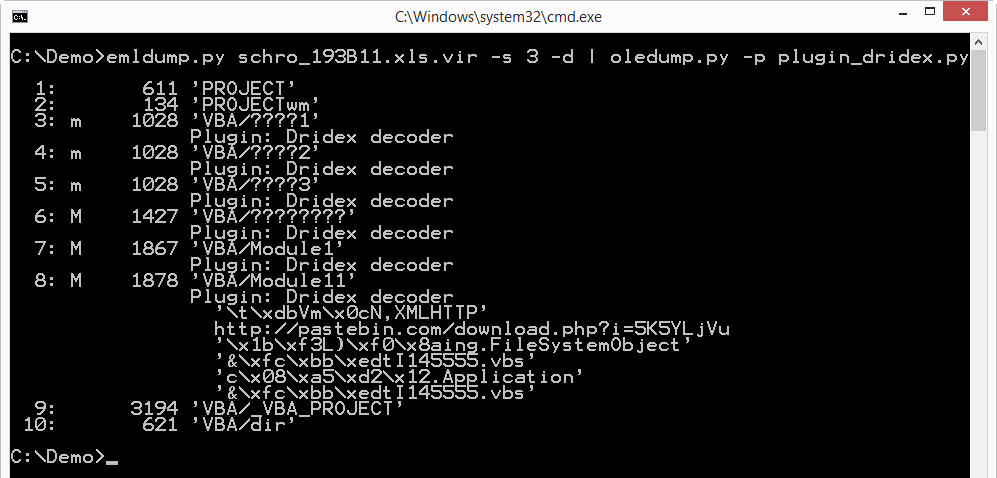
I also updated my plugin plugin_dridex with this encoding:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives


Comments
Guess what: SAFER alias software restriction policies blocks both the execution of the .VBS and the downloaded malware!
Anonymous
May 16th 2015
1 decade ago
"SANDBOX_INERT: If this value is used, the system does not check AppLocker rules or apply Software Restriction Policies."
I reported this 4 years ago:
http://blog.didierstevens.com/2011/01/25/circumventing-srp-and-applocker-to-create-a-new-process-by-design/
As a result of my blogposts, Microsoft designed a hotfix to disable this bypass.
https://support.microsoft.com/en-us/kb/2532445
This hotfix is not installed by default.
Anonymous
May 16th 2015
1 decade ago
Anonymous
May 16th 2015
1 decade ago