Another Day, Another Wave of Phishing Emails
I'm collecting a lot of phishing samples every day and most of them are part of big waves of spam... Millions of messages are sent with hope that at least some victims will fall in the trap. And sometimes, you find a nice (different) one like yesterday. It was a classic email with the subject "Important Notice" enticing the victim to open the attached file. The malicious file was an HTML document with an obfuscated JavaScript:
document.write(unescape('%3c%21%64%6f%63%74%79%70%65%20%68%74%6d%6c%3e%0d%0a%3c%68%74%6d%6c%3e%0d%0a%
3c%68%65%61%64%3e%0d%0a%3c%6d%65%74%61%20%63%68%61%72%73%65%74%3d%22%75%74%66%2d%38%22%3e%0d%0a%3c%74
%69%74%6c%65%3e%45%78%63%65%6c%20%4f%6e%6c%69%6e%65%3c%2f%74%69%74%6c%65%3e%0d%0a%3c%6d%65%74%61%20%6
e%61%6d%65%3d%22%67%65%6e%65%72%61%74%6f%72%22%20%63%6f%6e%74%65%6e%74%3d%22%57%59%53%49%57%59%47%20%
... (very long payload) ...
4%3d%22%22%3e%3c%2f%64%69%76%3e%0d%0a%3c%2f%62%6f%64%79%3e%0d%0a%3c%2f%68%74%6d%6c%3e'));
This is not complicated to de-obfuscate this payload (the code is available here). The attacker generated a page with an online HTML editor and added a form to capture credentials. The rendered page looks like a fake Microsoft Excel screenshot popping up a dialog box:
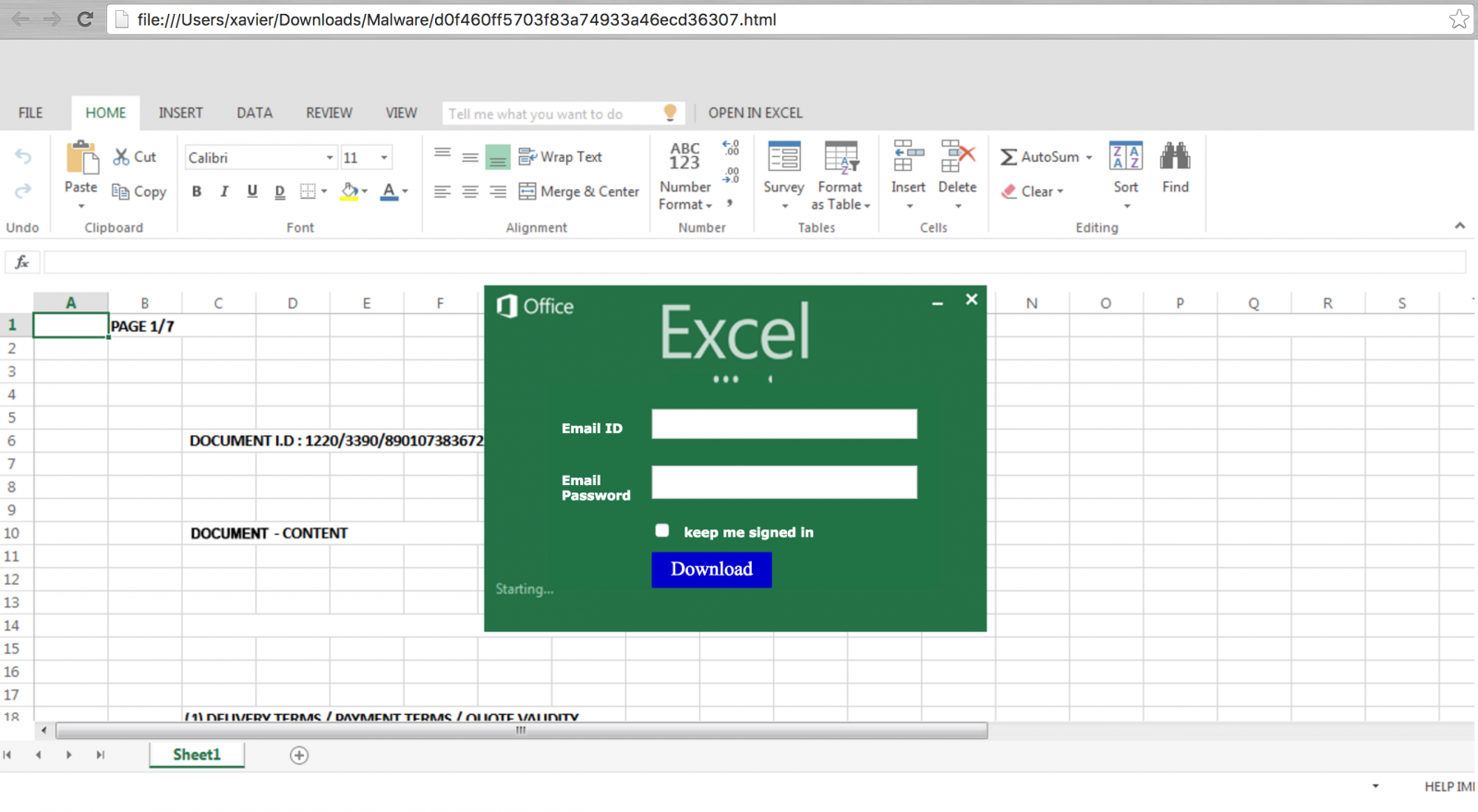
The HTML objects are downloaded from hxxp://tourkrabithailand.com/images/services/gr/ and credentials are posted to hxxp://mat-update.be/money/result.php. I contacted the Belgian CERT yesterday to report this website and the domain is already blocked.
Nothing fancy, bad design (why a blue "Download" button?) but it works! The JavaScript code runs below the radar with a low VT detection rate: 2/56 (link).
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
The volume of malicious email from EOP relays is so massive and the quantity of ham so vanishingly minuscule that here the EOP relay ranges are dumped into a pit by a firewall ACL.
Anonymous
May 13th 2016
9 years ago
outlook.com. 300 IN TXT "v=spf1 include:spf-a.outlook.com include:spf-b.outlook.com ip4:157.55.9.128/25 include:spf.protection.outlook.com include:spf-a.hotmail.com include:_spf-ssg-b.microsoft.com include:_spf-ssg-c.microsoft.com ~all"
But if the receiving MTA does not check the record... It's useless...
Anonymous
May 13th 2016
9 years ago
>
What has that to do with it? All the ransomware spam emanating from EOP is relayed _through_ Microsoft relays and complies perfectly with SPF and DMARC (MS does not sign with DKIM).
For some documentation on how bad it take a look at the ISC spam filter logs and see
https://www.spamhaus.org/sbl/listings/microsoft.com
and check the entries for x.x.x.0/32 where Spamhaus is reluctant to blacklist EOP relays (hence the .0/32) but documents the problem. Other SBL listings relate to Azure which obviously should be ACLed into oblivion (along with AWS).
-----
The _question_ is why won't Microsoft apply intelligence and resources to preventing abuse as Google has for eight years and Yahoo has since Marissa Mayer took the helm?
Anonymous
May 13th 2016
9 years ago