Angular-base64-update Demo Script Exploited (CVE-2024-42640)
Demo scripts left behind after installing applications or frameworks are an ongoing problem. After installation, removing any "demo" or "example" folders is usually best. A few days ago, Ravindu Wickramasinghe noticed that the Angular-base64-upload project is leaving behind a demo folder with a script allowing arbitrary file uploads without authentication [1]. Exploitation of the vulnerability is trivial. An attacker may use the file upload script to upload a web shell, and in response, the attacker will obtain remote command execution with all the privileges granted to the web server.
Sadly, the project is also no longer maintained. But a patch is not needed. Removing the vulnerable script (and likely the entire demo folder) should be an appropriate response.
Shortly after the blog post's publication, we detected exploit attempts in our web honeypot logs. On October 14th, we saw about 3,000 scans for
/angular-base64-upload/demo/server.php
Just note that requests for URLs containing "demo" are pretty standard. Interestingly, there was an increase in these requests starting in July.
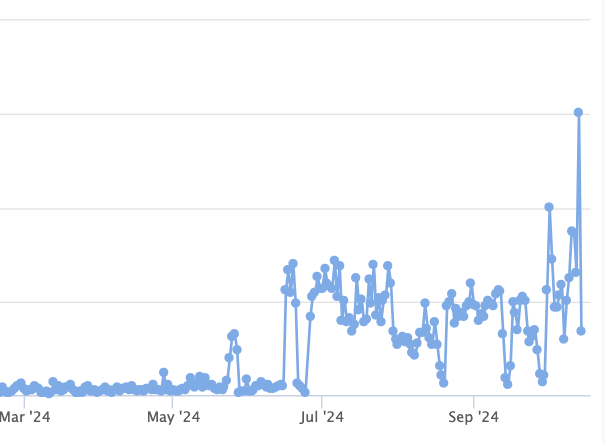
Graph of requests containing the string "demo".
[1] https://www.zyenra.com/blog/unauthenticated-rce-in-angular-base64-upload.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments