An Update On DVR Malware: A DVR Torture Chamber
Last week, the fact that someone leaked 1700 or so IP addresses with default username/password caused some people to get excited about the issue of default telnet credentials again. Ever since the "Mirai" outbreak, we do see a pretty constant stream of requests for port 23 (and to some extent 2323 as well as 22) searching for systems with default credentials. When Mirai came out, I did a quick experiment testing how long it would take to have a security camera DVR with default credentials infected. So I decided to repeat this experiment, to see if anything changed. Using an actual vulnerable DVR vs. a honeypot will be more realistic and provide better results.
I used an "Anran" branded DVR with default configuration. This particular model accepts "root" logins with the well-known password "xc3511". Many of the worms infecting these devices will disable telnet after a successful infection, to prevent others from exploiting the weak credentials. So to allow for continuous infections, I connected my DVR to a remote controlled power outlet, and power cycled it once every 5 minutes. I logged all traffic to and from the DVR. Here is a sketch of the setup:
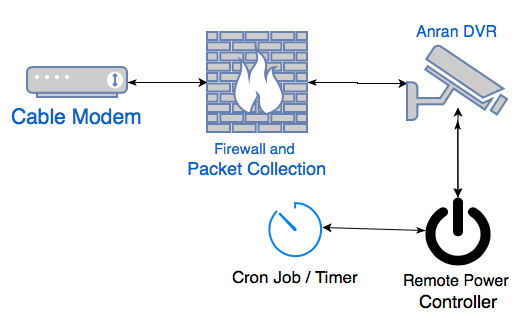
So every 5 minutes, the DVR rebooted and was ready for new connections. A reboot takes a bit less than 30 seconds. Traffic from the DVR outbound was blocked by the firewall to prevent it from infecting other systems. I kept this running for a bit less than two days. Here are some of the basic statistics from the experiment:
| Start Time | Aug 24th 11:53 am |
| End Time | Aug 26th 9:35 am |
| Data Collected | 3,098 MBytes, 36 Million Packets |
| Time Active | 45 hrs 42 min |
| Total connections to the DVR | 10,143 |
| Total login attempts using the "xc3511" password | 1254 Different IPs (every 2 minutes) |
So in short: Every 2 minutes the system was compromised by someone(thing) logging in using the correct credentials.
For the 1254 attacking IP addresses, Shodan had information for 592 of them. As expected, we do see our usual "suspects":
| Model / HTTP Banner | Count |
| GoAhead-Webs | 128 |
| Dahua DVR | 31 |
| DD-WRT | 21 |
| micro-httpd | 14 |
| EnGenius Router | 12 |
Notable manufacturers of the devices include TP-Link, AvTech, Synology, D-Link. In short, your usual "DO NOT CONNECT TO THE INTERNET" devices.
While I am calling the activity "Mirai," dozens of variants hit the DVR. The geographic distribution of these systems matches what we saw early on with Mira (only counting the hosts that had Shodan information):
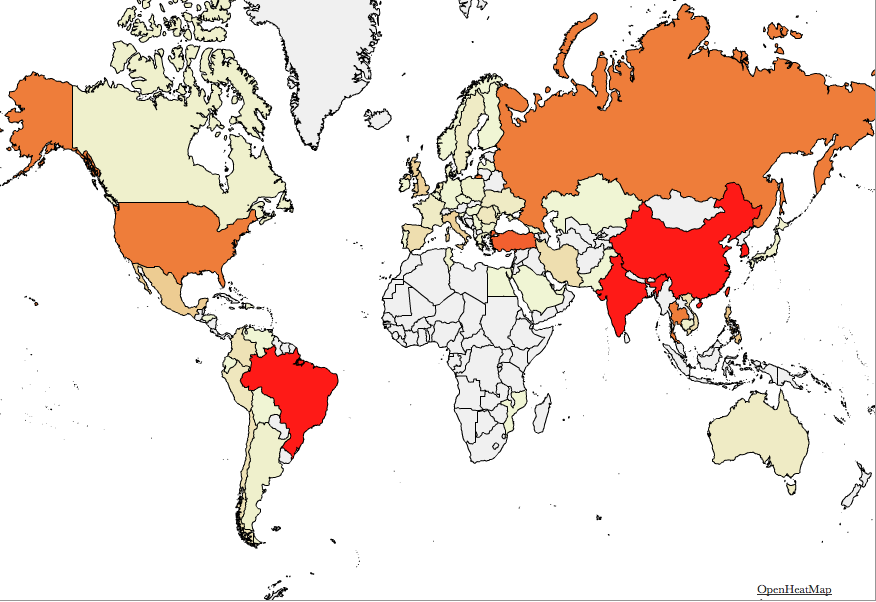
So in short: 1,700 additional vulnerable systems will not matter. We do see a pretty steady set of 100,000-150,000 sources participating in telnet scans. This problem isn't going away anytime soon. If people haven't heard yet about vulnerable DVRs and default passwords, then they will not read this article either. Variants like "Brickerbot," which supposedly attempted to break vulnerable devices, are ineffective because most of these devices can not be "bricked" by overwriting a disk with "dd." They may become temporarily unresponsive but will be fine after a reboot. Many of these devices are buggy enough, where the owner is used to regular reboots, and that is probably the only maintenance the owner will perform on these devices.
(ping me if you want a copy of the full pcap. The device was connected to a normal small business cable modem connection with 5 IP addresses)
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Total login attempts using the "xc3511" password by 1254 Different IPs (every 2 minutes) is disturbing. It would be interesting to know the "market age" of the telnet device as well. Any young device that has an overly significant amount of attacks would make its manufacturer rather suspect IMHO.
-b
Anonymous
Aug 28th 2017
8 years ago
Anonymous
Aug 28th 2017
8 years ago
Question: Was the device set up on an IP domain that is known to be owned/utilized by SANS?
If the device is on an IP domain that is known to be used by SANS for operations, could it have been a victim of one or more such entities that wish to embarrass or disrupt the ISC or SANS? It is certain that SANS and the ISC has its nemesis attackers out there.
I do not question the risk posed by IoT devices (I do hate them so). I just want to understand the parameters of the experiment.
Thank you again for all that you do Dr. J. :-)
Anonymous
Aug 28th 2017
8 years ago
Thank you. Johannes.
I wanna copy of the full pcap.
How can I get that?
Should I leave my e-mail? ^^
Anonymous
Aug 29th 2017
8 years ago
Regards.
Anonymous
Aug 30th 2017
8 years ago
Anonymous
Aug 30th 2017
8 years ago