Voice Message Notifications Deliver Ransomware
Bad guys need to constantly find new ways to lure their victims. If billing notifications were very common for a while, not all people in a company are working with such kind of documents. Which types of notification do they have in common? All of them have a phone number and with modern communication channels ("Unified Communications") like Microsoft Lync or Cisco, everybody can receive a mail with a voice mail notification. Even residential systems can deliver voice message notifications.
Here is an example displayed in Microsoft Outlook:
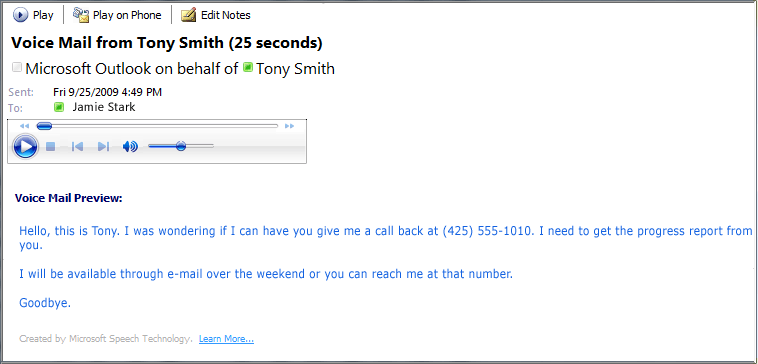
Today, I received a wave of emails like the following:
From: voicemail@rootshell.be To: [redacted]Subject: [Vigor2820 Series] New voice mail message from 01422520472 on 2016/08/23 15:55:25 Dear [ redacted]: There is a message for you from 01422520472, on 2016/08/23 15:55:25 . You might want to check it when you get a chance.Thanks!
The sender is spoofed with the victim domain name. The following file was attached to the message:
$ unzip Message_from_01422520472.wav.zip
Archive: Message_from_01422520472.wav.zip
testing: 197577509502.wsf OK
No errors detected in compressed data of Message_from_01422520472.wav.zip.
$ md5sum 197577509502.wsf
f2ee33a688a45b161d3191693196cb1d 197577509502.wsf
Note the '.wav.zip' extension to lure the user. As usual, the payload is heavily obfuscated and the AV detection ratio is still very low (6/55 at 11:55:00 UTC)[1]
Vigor is UK company building ADSL residential modems[2]. This tends to think that the new wave is targeting residential customers.
Here are the C2 servers (for your IDS):
89.42.39.81
213.205.40.169
51.254.55.171
194.67.210.183
185.51.247.211
185.129.148.19
91.201.202.125
[1] https://www.virustotal.com/en/file/97be73cf491cf8e4d30e0e6d9b73e95151f77b3e52813e06b2ef391fa6f26b2a/analysis/1471949327/
[2] http://www.draytek.co.uk/products/legacy/vigor-2820
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
The current count is approx 150, but we'll keep monitoring of course.
I've already submitted the list of IP addresses separately.
Please let me know if you would want me to set up a periodic refresh or if you would like further data such as spamd log extracts.
- Peter
PS (update 2016-08-24) final count is 207 unique IP addresses attempting to deliver, none got past our greylisting. A writeup with data and some massaging may follow soonish, time allowing (check back at bsdly.blogspot.com)
Anonymous
Aug 23rd 2016
9 years ago
We saw the same exact campaign this morning at our company
Anonymous
Aug 23rd 2016
9 years ago
foxhole_js.cdb and foxhole_filename.cdb also blocking them.
sanesecurity.com/usage/linux-scripts/
Anonymous
Aug 23rd 2016
9 years ago
Anonymous
Aug 24th 2016
9 years ago
Anonymous
Aug 24th 2016
9 years ago
It's up at http://bsdly.blogspot.com/2016/08/the-voicemail-scammers-never-got-past.html
Anonymous
Aug 29th 2016
9 years ago
To download or see further information regarding RansomSaver please visit http://synergy-usa-llc.com/ransomsaver-overview.html
Anonymous
Oct 21st 2016
9 years ago