Tor Use Uptick
The Tor Metrics Portal is reporting a jump in their user metrics (https://metrics.torproject.org/users.html)
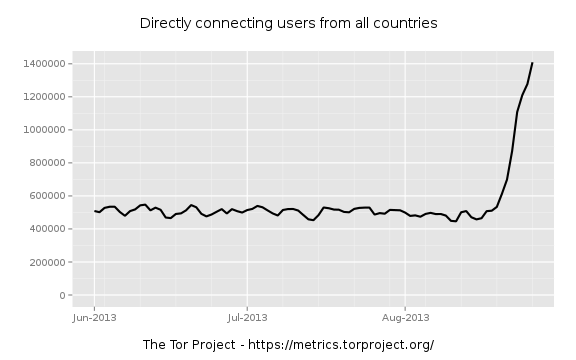
This is causing a bit of discussion and as people share observations and data with each other a few hypotheses bubble up.
- It's a new malware variant.
- It's people responding to news of government surveillance.
- It's a reporting error.
We've received a few reports here about vulnerability scans coming in from Tor nodes, and a report of a compromised set of machines that had tor clients installed on them. As more data are shared and samples come to the surface, let's look at the Tor Project's own data a little more closely.
First, what are they actually counting? According to their site:
"After being connected to the Tor network, users need to refresh their list of running relays on a regular basis. They send their requests to one out of a few hundred directory mirrors to save bandwidth of the directory authorities. The following graphs show an estimate of recurring Tor users based on the requests seen by a few dozen directory mirrors."
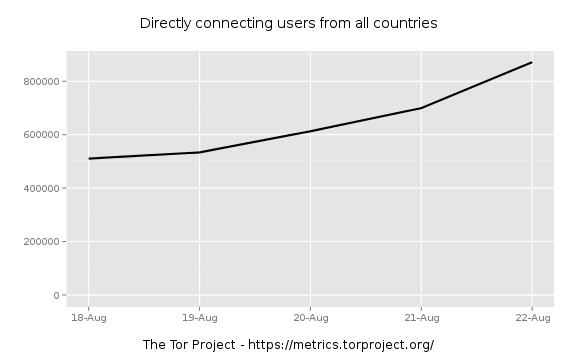
So we're seeing an uptick in directory requests. When did this start? Looks mid August, so let's zoom in and see. I try a little binary search to narrow it down. First zooming to AUG-15 through AUG-30:
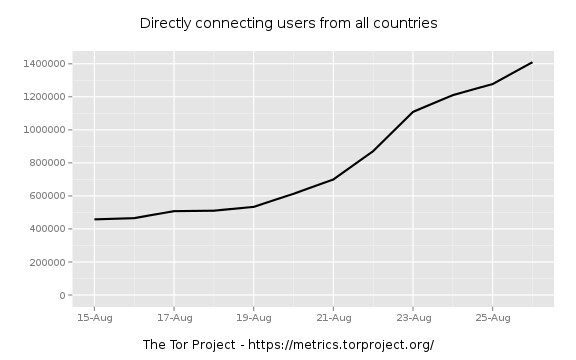
Zooming in further to find were the jump really starts:
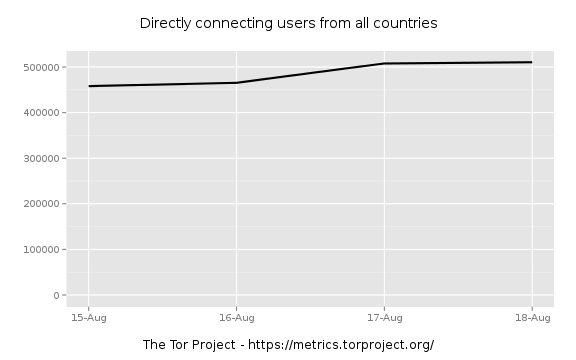
Things are still flat on the 19th.
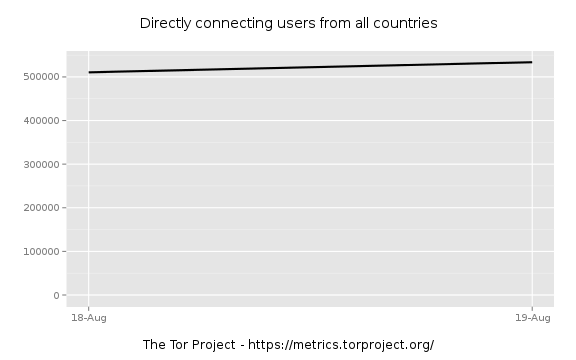
I'm liking the 19th as the beginning.
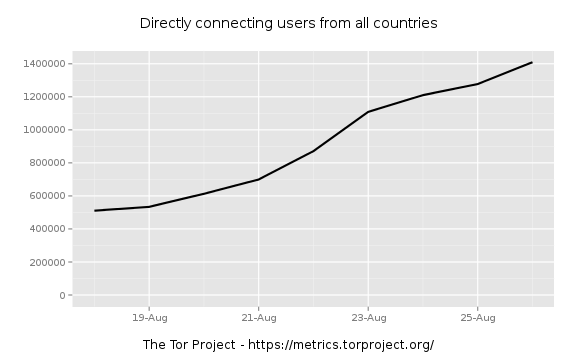
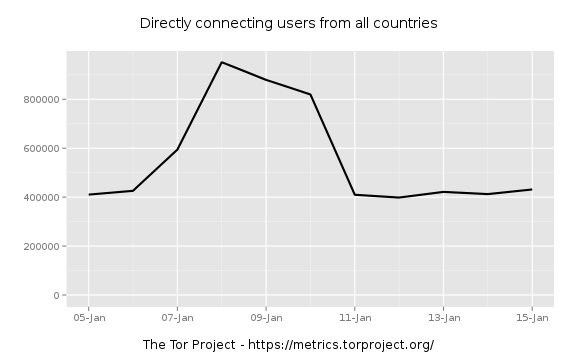
Has this happened before? Let's really widen the scope a bit.
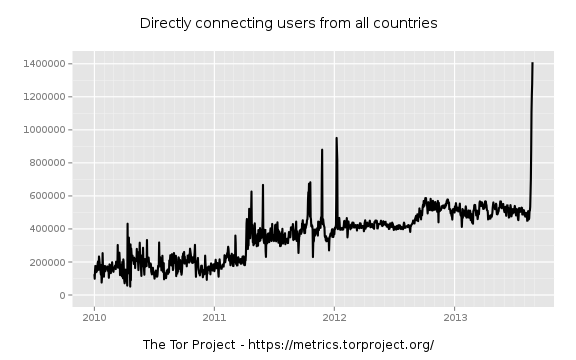
So we had a recent spike in early 2012.
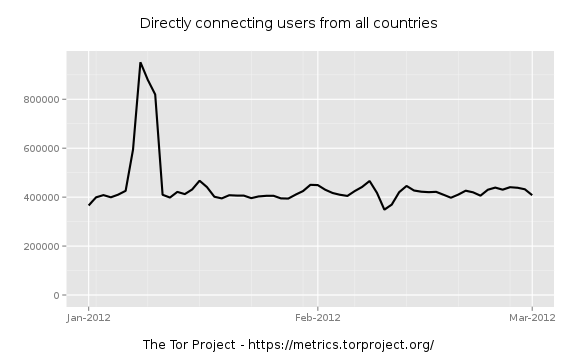
There appears to be a similar doubling of users between 06-JAN and 11-JAN in 2012
Are you seeing an uptick in TOR activity in your networks? Share you observations, and especially any malware (https://isc.sans.edu/contact.html)


Comments
Sounds like quite an obvious way for malware to communicate with C&C. Until now we could see that happening with an IDS by analysing outgoing traffic, or given a list of bad reputation networks. And the C&C servers could be easily found and shut down.
Tor may appear as ordinary HTTPS traffic, to hosts that are essentially trusted, and new hosts will come and go. If this is visible at the moment, because they connect directly to some directory services, maybe they'll just avoid doing that in future.
A Tor hidden service is, by design, impossible to locate. Although that host must be getting an awful lot of traffic directed at them right now.
Anonymous
Aug 31st 2013
1 decade ago
@Steven C.: The only way to tell would be to run the IPs of incoming traffic from your network against a TOR DNSbl or node checker such as this one: https://www.dan.me.uk/torcheck
Anonymous
Sep 1st 2013
1 decade ago
Snowden hit the scene on 08-JUN-2013. Freedom hosting was around 04-AUG-2013. Piratebrowser appears in the press 11-AUG-2013.
I can't imagine any of these events tripling the number of users. 1,200,000 new requests That's comparable to the population of Estonia, or a very large chunk of Philadelphia.
I think something else is generating these list-refreshes.
Anonymous
Sep 1st 2013
1 decade ago
Anonymous
Sep 1st 2013
1 decade ago
Snowden hit the scene on 08-JUN-2013. Freedom hosting was around 04-AUG-2013. Piratebrowser appears in the press 11-AUG-2013.
I can't imagine any of these events tripling the number of users. 1,200,000 new requests That's comparable to the population of Estonia, or a very large chunk of Philadelphia.
I think something else is generating these list-refreshes.[/quote]
Call me hopeful, but I think it is possible that this is an uptick in organic and legitimate usage. It's true that the Snowden, Freedom Hosting and Piratebrowser events do not directly correlate, but let's look at the bigger picture here... (Just looking at the USA, but I think the phenomenon extends past that jurisdiction.)
Between 2003 and 2006 about 192,000 NSLs (National Security Letters) were issued to Americans and yet during that time you did not hear much about Internet privacy in the press.
Fast-forward to more recent times -- Nicholas Merrill (Calyx ISP), Julian Assange (Wikileaks), SOPA, Bradley Manning, Edward Snowden, Ladar Levison (Lavabit), Mike Janke (SilentCircle), etc. -- and you see steadily mounting press relating to Internet privacy, and therefore increasing public awareness.
Is it unlikely this uptick was caused by growing awareness? Maybe. But, it certainly is possible. I suppose it's also possible that we have a combination of forces at play here, considering that an increase in general usage could in theory also carry with it an increase in malware on said network.
Among my own network of peers that are not involved in InfoSec I have been advocating for privacy-protecting alternatives to mainstream Internet services for several years. Despite my efforts, I have noticed a significant uptick of interest in my personal network over the past few months, just as the general public and press simultaneously become more concerned with the topic.
With the recent shut down of privacy focused e-mail companies (like Lavabit and SilentCircle) it is also reasonable to believe that many users of these services have since started resorting to Tor Mail or the like.
While I speak mostly of the USA here I do know that many similar situations and even more restrictive ones do exist around the world, providing further circumstantial evidence of motive for the masses to migrate toward using privacy-protecting Internet services.
We all know of the "bandwagon effect." Like Facebook, if seemingly everyone with similar goals starts using a particular service to achieve them, it can quickly take off. In other words, once a privacy-protecting service is viewed as the de facto solution, people will feel they should use that one particularly so that they may privately communicate with a broader audience. If we are indeed seeing an uptick in real usage, this phenomenon is surely to be at play alongside. It's possible that the PirateBrowser may have contributed to or even started this chain of events. It may be hard for us to see this, but some of the less technical people who value privacy may have been daunted by the idea of using the Tor network in the past, preferring "simpler" options like Hushmail or Lavabit. Recent events may have pushed them "over the edge" so to speak, thereby helping to establish Tor based services as a more common solution. Of course, such an increase in usage and activity on the network would entice more "rogue forces" (malware, scanners, etc.) to become active there as well, increasing the traffic levels even further.
Finally, I wonder if any large organizations have begun using Tor recently? I wouldn't be surprised to see journalism, human rights or healthcare organizations (just for example) begin implementing vast Tor based services and policies. If this were to happen, it could surely cause a surge in activity.
Admittedly, none of this explains the prior spikes outlined, although the previous spikes do appear to be less gradual and shorter in duration.
I'm not saying I'm right here, but I do think it's worth considering, and it's definitely worth hoping for. The general public becoming keenly aware of the state of Internet privacy is the most likely catalyst for policy change.
P.S. Only slightly related but must see video of then Senator Obama speaking on the issue of NSLs, American's right to privacy and the Patriot Act: http://www.youtube.com/watch?v=5ylVOdriEyA
Anonymous
Sep 2nd 2013
1 decade ago
With the Syria conflict going on is it possible that we are seeing an uptick due to increased military usage? It's also possible that "rogue entities" such as the SEA (Syrian Electronic Army) have become more active on Tor in response to the situation.
Anonymous
Sep 3rd 2013
1 decade ago
At http://prism-break.org/media/ is a pretty good chronology of media reports that mentioned that particular information portal, so perhaps also, or at least indirectly, were promoting Tor and other privacy techniques in their stories. Many were published 2013-06 through 2013-08 with no apparent upward trend, until that sudden, dramatic increase around 2013-08-19
An increase in 'conventional' Tor usage should mean an increase in Tor exit traffic hitting servers. I would bet that if people could check this, there would be no such increase on the same magnitude as Tor *client* usage suggested by those metrics. That's why I guessed this is a botnet phoning home to a hidden service or something else nefarious.
Anonymous
Sep 4th 2013
1 decade ago
Anonymous
Sep 5th 2013
1 decade ago