Those strange e-mails with URLs in them can lead to Android malware
You've probably gotten a few of these e-mails over the last few months (I saw the first one of this latest kind in early Feb), we got one to the handlers list earlier this week which prompted this diary. They seem pretty innocuous, they have little or no text and a URL like the one shown below.
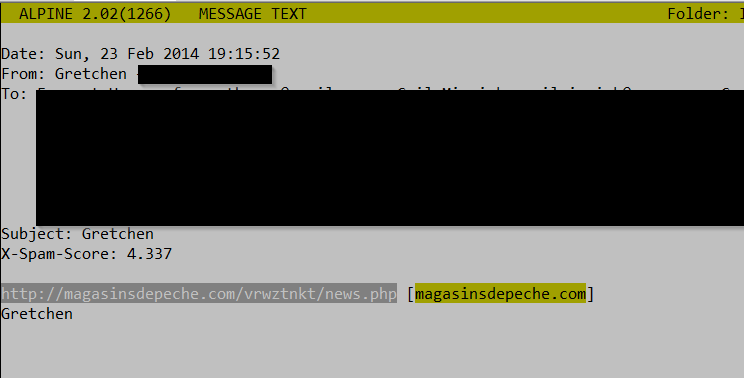
Note: the above link doesn't lead to the malware anymore, so I didn't obscure it.
Most seem to be sent from Yahoo! (or Yahoo!-related e-mail addresses), so they may be coming from addresses that were compromised during the breach of Yahoo! back in January. The odd thing about this is that, if you follow the URL from a Linux, Windows, or Mac you get a spammy website (I don't remember if it was Canadian pharmacies, or what), but what a colleague of mine at $dayjob (all credit goes to Stan) discovered is that if you opened the e-mail on an Android device (or followed the links with an Android user-agent and referrers), this instead leads to downloading of the latest version of the DroidNotCompatible Android malware (which is, itself, and interesting specimen, but I'll leave that for another diary). The first URL led to a 302 redirect to a page that included the malicious APK in a META refresh tag. You can change the user-agent string with the -U switch to wget or the -A switch to curl if you want to try grabbing things from the Linux/Unix commandline (which is, of course, how you all surf the internet anyway, right?).
The take away, if there is one, is that when tracing suspicious URLs, don't just assume the site is not interesting just because nothing bad happened when you looked at it from your sacrificial browsing environment (you all have one of these whether you realize it or not, the bad news is it may be your main system). Try with additional user-agents (and/or referrers) and see what happens. Do you have a collection of your favorite user-agent strings you like to use? If there is enough interest, perhaps we'll put up a page either here on the main site or over on the handlers server with some of the more useful ones.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments
http://blog.dynamoo.com/2014/02/something-evil-on-74501228-56136231-and.html
And I've reported probably over a hundred to SBW.
http://pastebin.com/rXktA0DG
http://pastebin.com/tayY6HgS
http://pastebin.com/mBqdH3mg
http://pastebin.com/t0SaEmvN
http://pastebin.com/SvkMaZGV
Anonymous
Apr 7th 2014
1 decade ago
1: mobile.downloadadobecentral.ru/FLVupdate.php
2: mobile.downloadmobilessoftware.ru/FLVupdate.php (two s)
3: mobile.downloadmobilesoftware.ru/FLVupdate.php (one s)
4: downloadappsstation.ru/securityupdate.php
5: androidonlineupdatecdn.ru/securityupdate.php
Anonymous
Apr 8th 2014
1 decade ago