The strange case of Great honeypot of China
Looking at changes that the internet as a whole goes through over time can be quite edifying. Since old servers are being decommissioned and new ones are being added all the time, the internet “landscape” can change significantly even over the course of a year or several months[1].
Because very few of us have ever had access to our own Carna botnet[2] or other solution, which would enable us to periodically scan the entire public IP space, we have to depend on information provided to us by specialized services (e.g., Censys or Shodan), which conduct such scans on our behalf, to learn of these changes.
Since we are dependent on these third-party services, which are, from our viewpoint, basically “black boxes”, any large spikes that may be seen in data gathered from them may be the result of a real, rapid change in the public IP space, or the result of misconfiguration or error in some internal mechanism used by these services. And, unfortunately, it is not always easy to say which is which… Which holds true even for a recent spike in the number of honeypots that Shodan detected.
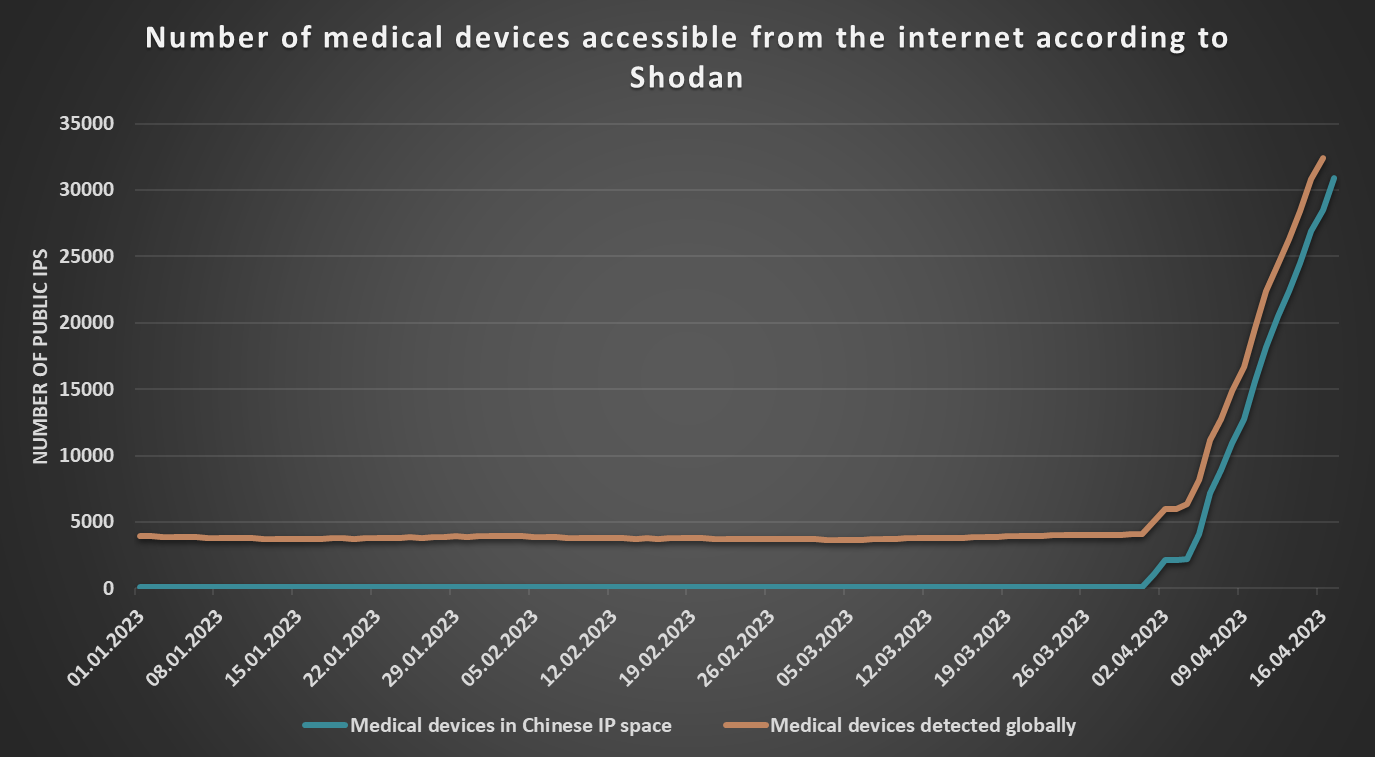
As I mentioned in some of my previous Diaries[3], I use my TriOp tool to periodically gather significant amounts of data from Shodan about the global internet landscape, as well as about the situation in different countries. Among other information, I use the tool to gather the number of devices that Shodan classifies as “medical” systems, which are accessible from the internet, and a few weeks ago, a script that I use to identify significant changes in the data started to generate daily notices about a sharp relative increase in such systems in China (and, several days later, about a corresponding relative increase on a global level).
In view of the continuous nature of the change, I decided to take a closer look at what was happening.
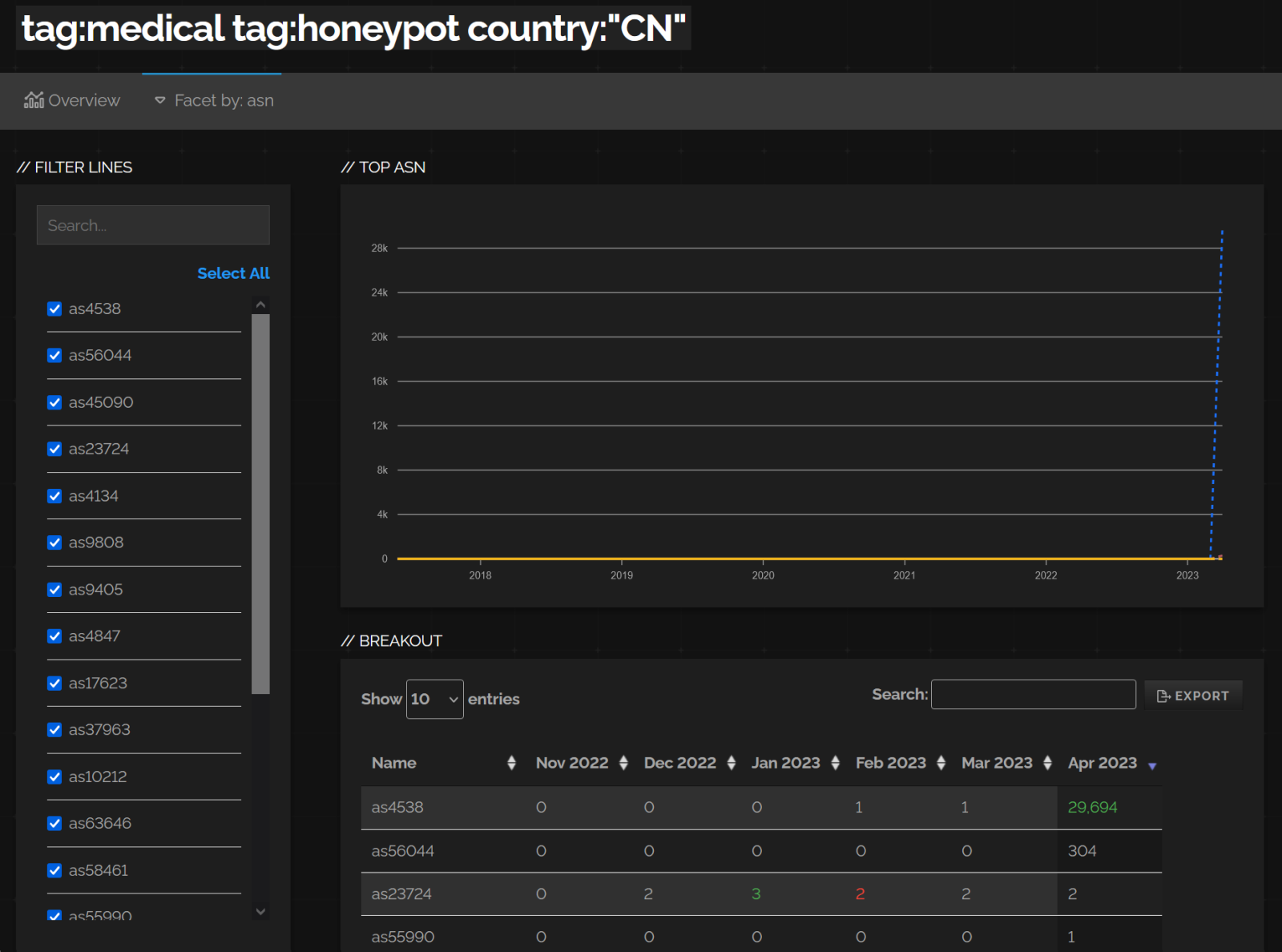
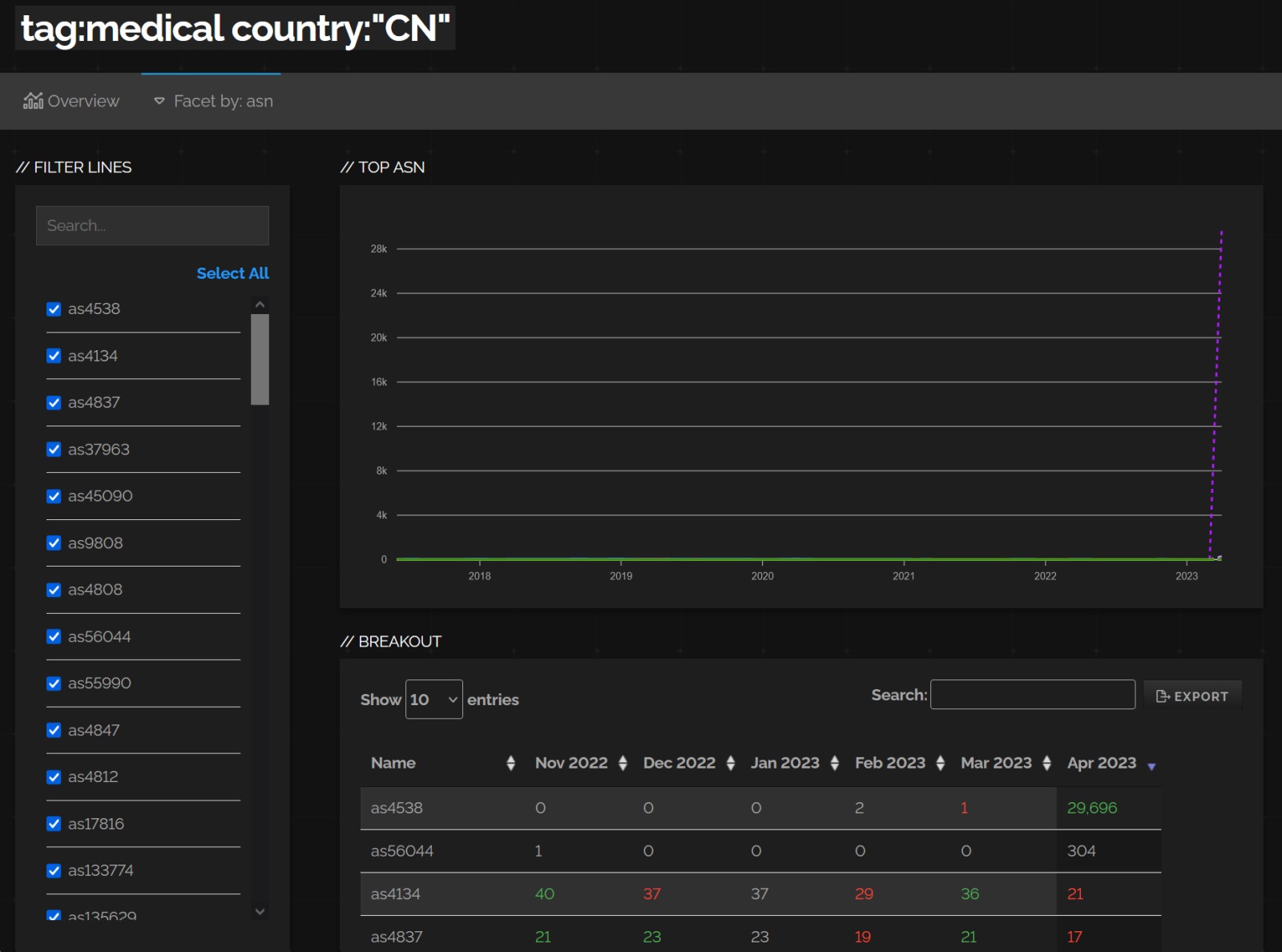
After a little bit of digging, it turned out that basically all of the newly detected systems were also classified as “honeypots” and were in network ranges assigned to the China Education and Research Network Center (specifically, to the AS4538), as you may see in the following images showing the output from Shodan Trends service.
I have tried to manually scan relevant ports (e.g., TCP 11112/DICOM) on several of the newly detected systems using Nmap, however, none of them appeared to be opened. Nevertheless, even though I did the scan from several different locations around the world, this doesn’t necessarily make the Shodan results incorrect, since there may be some very strict geolocation-based filtering in place (e.g., access to these systems may only be allowed to Chinese IPs).
However, what makes it more probable that the sharp increase in the number of “medical honeypots” is a false positive, is the fact that this wasn’t the end of the interesting “spikes” related to AS4538.
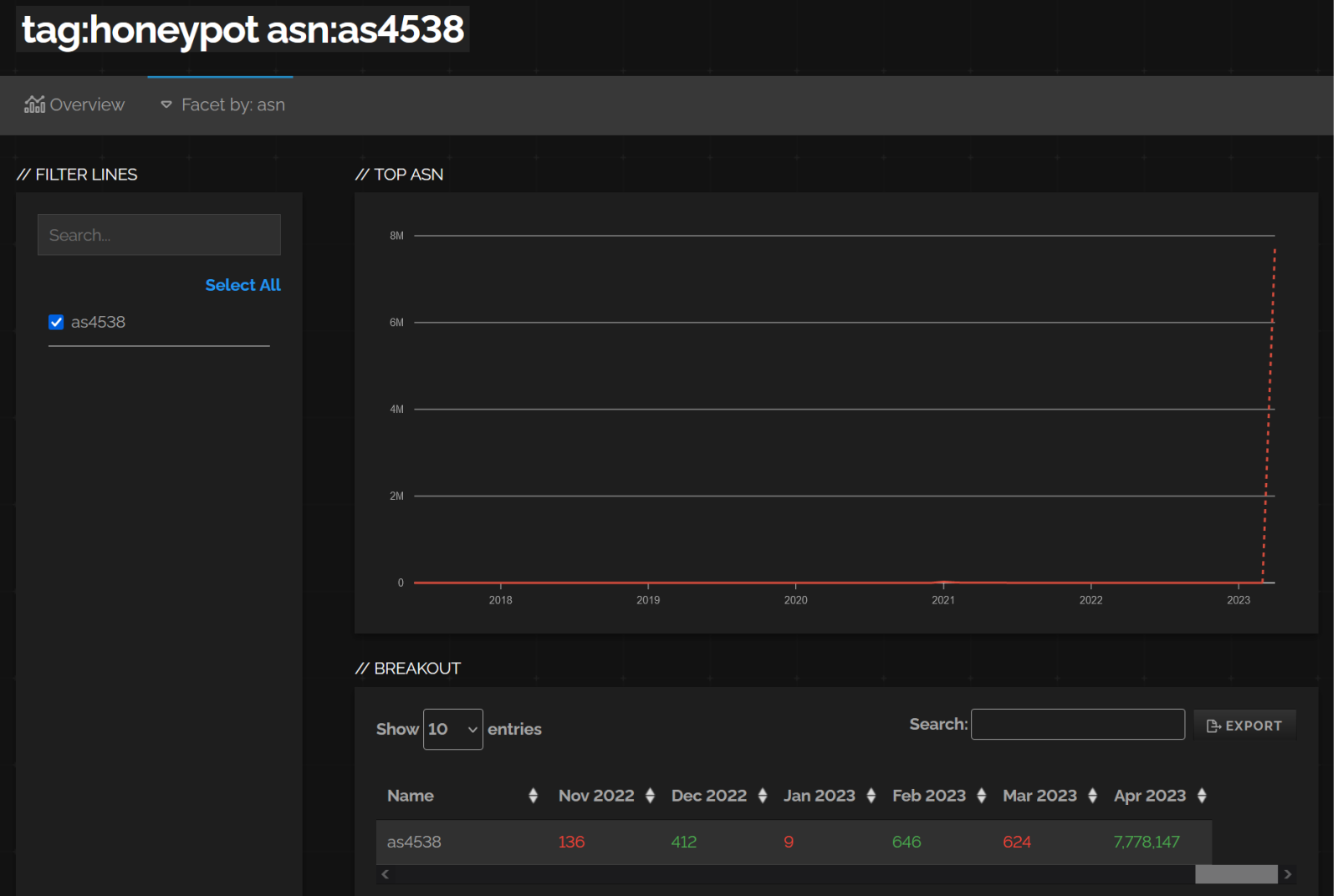
After a little more digging, I noticed that besides an increase in the number of medical devices, Shodan also saw a very large increase in the number of systems it classified as honeypots in the same AS – specifically, an increase from approximately 600 public IPs, where honeypots were detected in February and March, to well over 7.5 million public IPs in April (at the time of writing, Shodan actually returns the count of honeypots detected in the AS at over 8.1 million).
This would seem to indicate that either the Chinese academic sector (based on the AS owner) just built the largest-ever research honeypot (the “Great honeypot of China”, if you will), or – which is probably more likely – that there was some error in the “black box” of Shodan in relation to classifying systems as honeypots.
Whatever the case is, the data we have available at this point is certainly intriguing, to say the least… I will try to monitor how the situation develops, and, if anything interesting turns out, we might get back to the topic in another Diary sometime in the future.
[1] https://untrustednetwork.net/en/series/open-port-statistics/
[2] https://census2012.sourceforge.net/paper.html
[3] https://isc.sans.edu/diary/TriOp+tool+for+gathering+not+just+securityrelated+data+from+Shodanio+tool+drop/27034
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments