Size Matters for Many Security Controls
This week, I'm teaching FOR610 in Manchester, and while my students are busy resolving some challenges, I'm looking at my hunting results from the previous days. I found an interesting sample. The file was delivered via an email with a URL pointing to a well-known file-sharing service: hxxps://www[.]Mediafire[.]com/file/o3m15ydxnhlm9w0/New+Purchase+Order+pdf.tgz/file. The file is not available anymore, but I was able to find it back on VirusTotal: "New Purchase Order pdf.tgz" (SHA256:7f351b32e6209496ef59c511dffaf9312508b53e476b1e77171af3d433b94087[1]) with a low score of 3/54.
When I looked at the file, I received an error because the storage I'm using to store my samples to investigate was... full! The file is indeed compressed, and its original size is 1000001536 bytes. It's not a pdf file but a tar archive:
remnux@remnux:/MalwareZoo/20231028$ gzip -d -c 'New Purchase Order pdf.tgz' | tar tvf - -rwxr-xr-x 0/0 1000000000 2023-10-24 22:41 t62rs98N94MaHQL.exe
The PE file has a size of 1GB! The file has been padded with a lot of NULL characters:
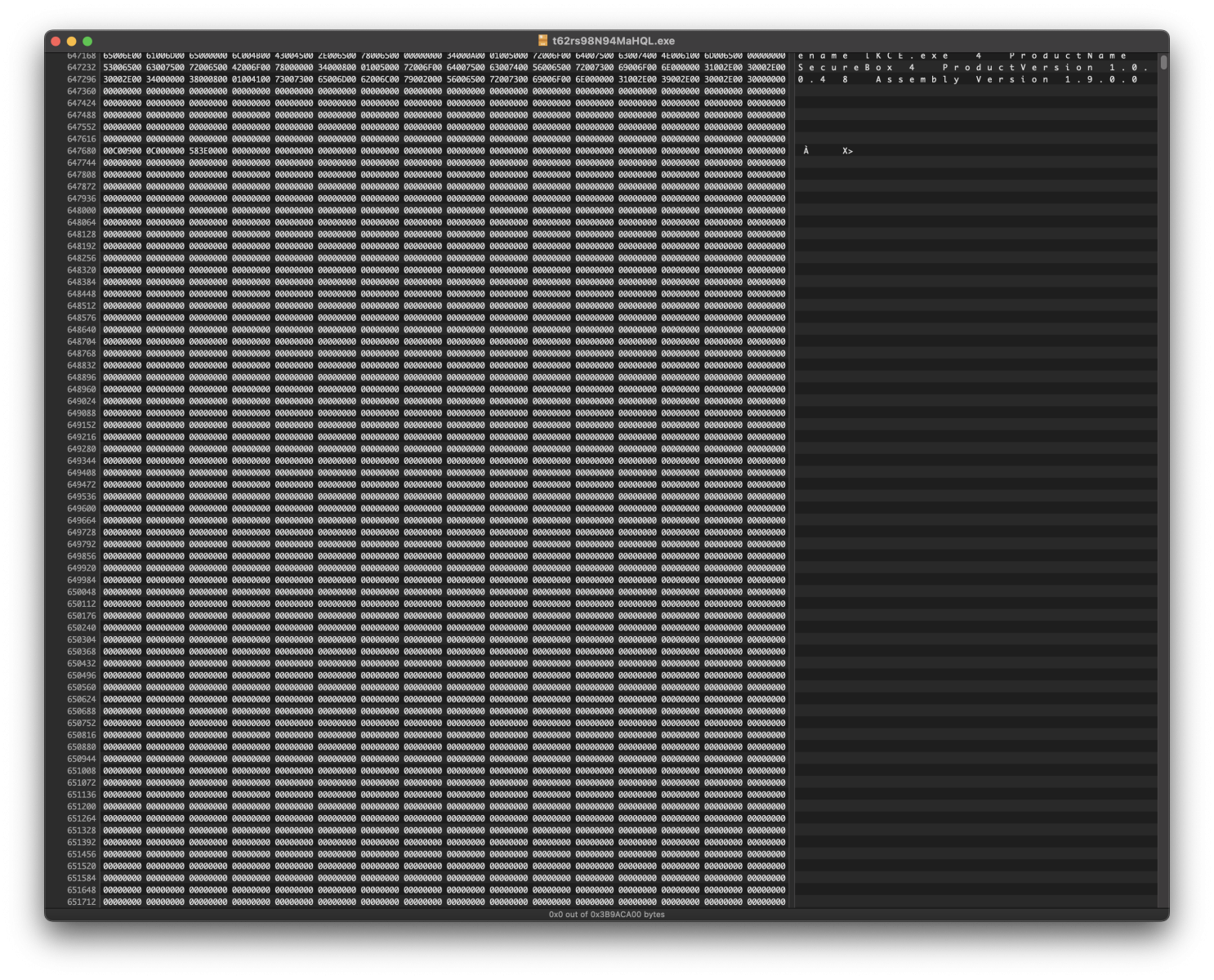
What's the purpose of this? To defeat many security controls. For performance reasons, most will not allow the processing of files above a specific size. PE files can be padded with many zeros; it won't break because all sections in the file (.text, .data, .rdata, etc.) are defined in the PE headers, and the loader will ignore the remaining bytes. It will also generate another hash for the file. This is a common technique that MITRE also lists as T1027.[2].
How do you analyze this type of file? I removed most of the trailing NULL characters (be sure not to remove all of them - keep a safe amount) to reduce the file size, then analyze it as usual.
[1] https://www.virustotal.com/gui/file/7f351b32e6209496ef59c511dffaf9312508b53e476b1e77171af3d433b94087
[2] https://attack.mitre.org/techniques/T1027/001/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments