Scans for Ivanti Connect "Secure" VPN Vulnerability (CVE-2023-46805, CVE-2024-21887)
Last week, Volexity published a blog describing two vulnerabilities in Ivanti's Connect "Secure" VPN [1]. These vulnerabilities have been exploited in limited, targeted attacks. At this point, Ivanti released a configuration workaround but no patch for this vulnerability. The configuration can be applied in the form of an encrypted XML file.
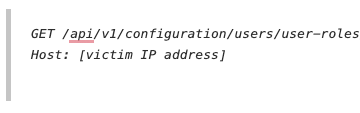
Watchtowr, a company in the vulnerability scanning business, investigated the configuration change created by Ivanti and shared how it detects if an Ivanti instance had the configuration change applied. After the change is applied, requests to a specific REST API URL (/api/v1/configuration/users/user-roles/user-role/rest-userrole1/web/web-bookmarks/bookmark) will include a complete HTML body. Before the patch is applied, only headers are received from the device [2].
Starting on Sunday, our honeypots detected the first scans for this URL. This is likely due to attackers building target lists while working on the exploit. Neither Volexity nor Watchtowr have released exploits for the vulnerability. Ivanti delivers the Connect "Secure" VPN as a virtual appliance with an obfuscated disk image. Still, the obfuscation is easily bypassed, and exploits are likely available to a wider and wider group of attackers. Ransomware attackers are likely already taking advantage of the vulnerability.
Currently, one IP address participating in these scans is 176.58.124.134. It has taken part in some scans for various vulnerabilities in the past. I am not yet able to confirm that any systems identified as vulnerable will be attacked. Still, at least, it looks like this attacker is building a target list for later exploitation.
Shadowserver stated that they are performing some scans for vulnerable instances. The website associated with the IP has a simple banner stating that the host is used to scan for vulnerable systems, and this may be a Shadowserver system.
The requests use minimal HTTP/1.1 requests with only the required host header:
GET /api/v1/configuration/users/user-roles/user-role/rest-userrole1/web/web-bookmarks/bookmark HTTP/1.1
Host: [victim IP address]
 [1] https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
[1] https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
[2] https://labs.watchtowr.com/welcome-to-2024-the-sslvpn-chaos-continues-ivanti-cve-2023-46805-cve-2024-21887/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments