Scanning for Fortinet ssh backdoor
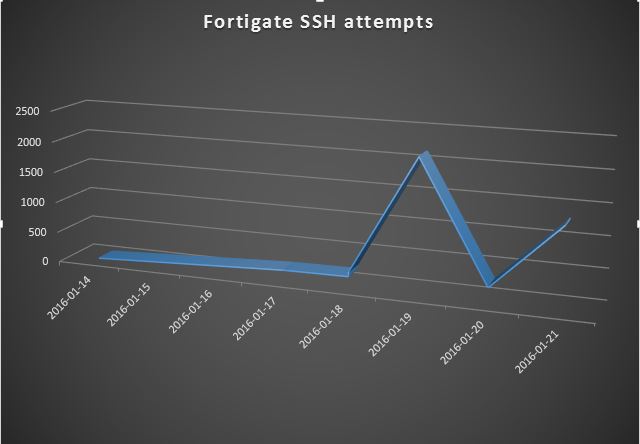
On 11 Jan, a Python script was posted on the full-disclosure mailing list that took advantage of a hardcoded ssh password in some older versions of various products from Fortinet (see complete list in Ref [1] below). Looking at our collected ssh data, we've seen an increase in scanning for those devices in the days since the revelation of the vulnerability. Nearly all of this scanning has come from two IPs in China (124.160.116.194 and 183.131.19.18). So if you haven't already applied patches and put ACLs/firewall rules in front of these devices limiting access to ssh from only specific management IPs, you have probably already been scanned and possibly pwned.
References:
[1] http://www.fortiguard.com/advisory/multiple-products-ssh-undocumented-login-vulnerability
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments
Anonymous
Jan 22nd 2016
1 decade ago
Anonymous
Jan 22nd 2016
1 decade ago
Anonymous
Jan 22nd 2016
1 decade ago
Anonymous
Jan 22nd 2016
1 decade ago