Running Snort on ESXi using the Distributed Switch
| This is a guest diary contributed by Basil Alawi |
In a previous diary I wrote about running snort on Vmware ESXi[1] . While that setup might be suitable for small setup with one ESXi host, it might be not suitable for larger implementations with multiple VSphere hosts. In this diary I will discuss deploying Snort on larger implementation with SPAN/Mirror ports.
SPAN ports require VMware Distributed Switch (dvSwitch) or Cisco Nexus 1000v. VMware dvSwich is available with VMware VSphere Enterprise Plus while Cisco Nexus 1000v is third party add-on. Both solutions required VSphere Enterprise Plus and VMware vCenter.
Test Lab
The test lab consists of Vmware ESXi 5.1 as host, VMware vCenter 5.1, Kali Linux, Security Onion and Metaspoitable VM. ESXi 5.1 will be the host system and Kali VM will be the attack server, while Metaspoitable will be the target and Security Onion will run the snort instance. (Figure 1).
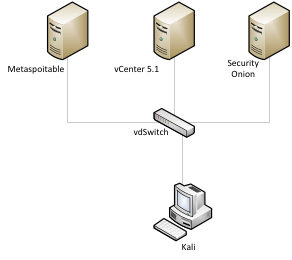
Figure 1(Test Lab)
Configuring dvSwitch:
The VMware vDS extends the feature set of the VMware Standard Switch, while simplifying network provisioning, monitoring, and management through an abstracted, single distributed switch representation of multiple VMware ESX and ESXi Servers in a VMware data center[2].
To configure the SPAN ports on VMware dvSwitch :
1. Log in to the vSphere Client and select the Networking inventory view
2. Right-click the vSphere distributed switch in the inventory pane, and select Edit Settings (Figure 2)
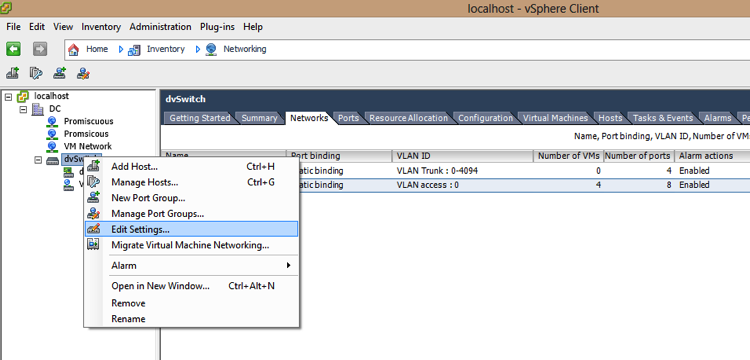
Figure 2
3- On the Port Mirroring tab, click Add
4-Enter a Name and Description for the port mirroring session
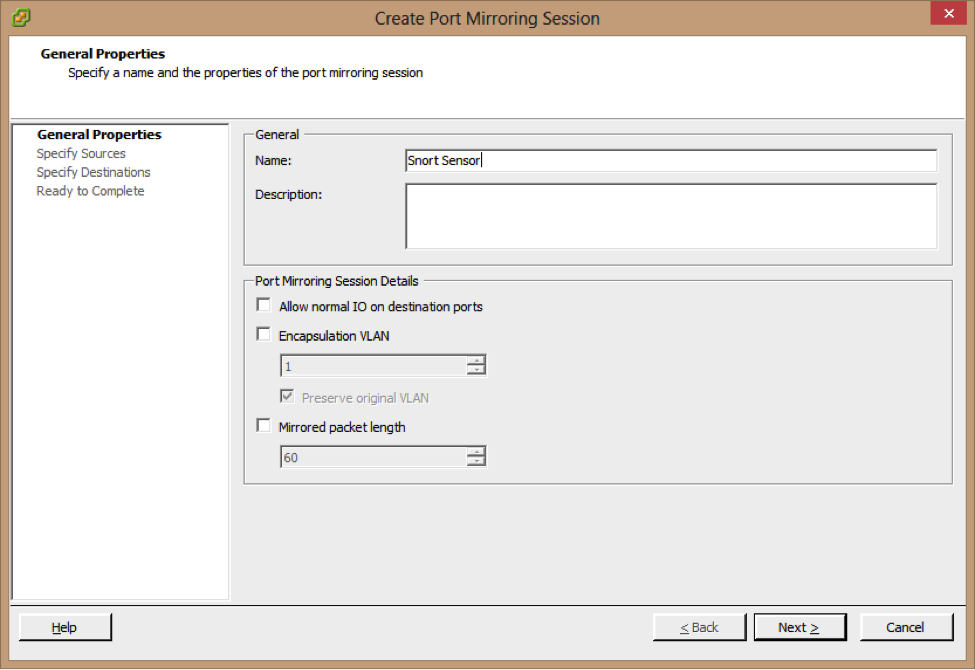
5- Make sure that the Allow normal IO on destination ports checkbox is deselected If you do not select this option, mirrored traffic will be allowed out on destination ports, but no traffic will
Be allowed in.
6-Click Next
7- Choose whether to use this source for Ingress or Egress traffic, or choose Ingress/Egress to use this source for both types of traffic.
8-Type the source port IDs and click >> to add the sources to the port mirroring session.
9- Click Next.
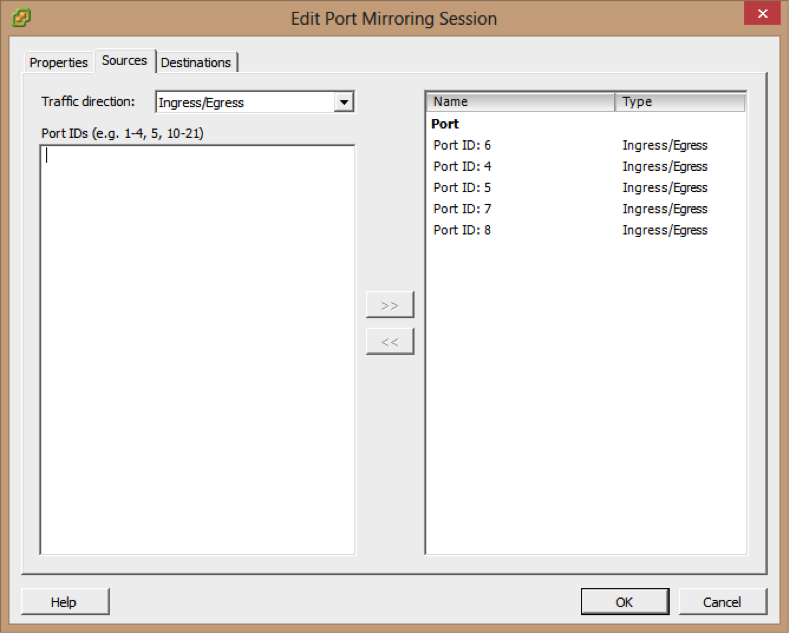
10- Choose the Destination type port ID.
11- Type the destination port IDs and click >> to add the destination to the port mirroring session
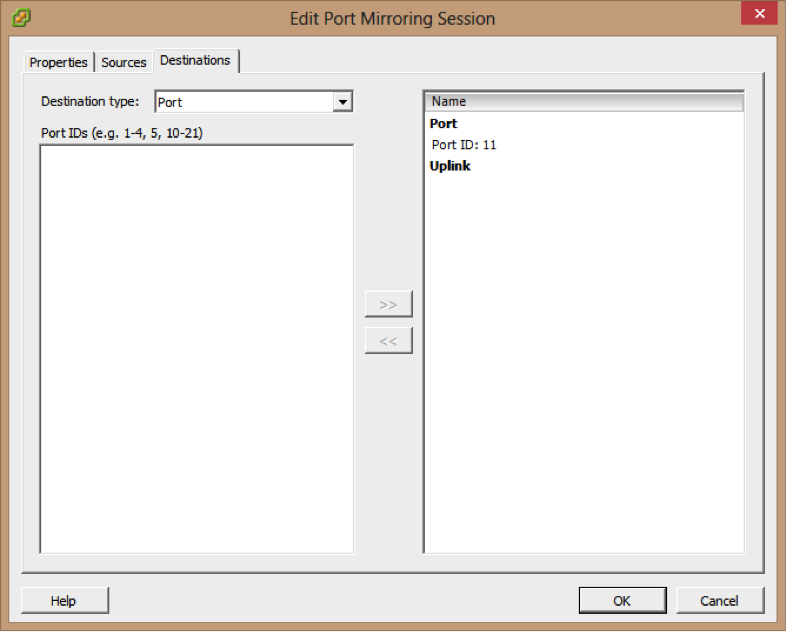
12- Click Next
13- Verify that the listed name and settings for the new port mirroring session are correct
14- Click Enable this port mirroring session to start the port mirroring session immediately.
15- Click Finish.
For this lab the traffic going to metaspoitable VM will be mirror to eth1 on Security Onion Server.
Running sniffer on eth1 can confirm that the mirror configuration is working as it should be:
|
tcpdump –nni eth1 |
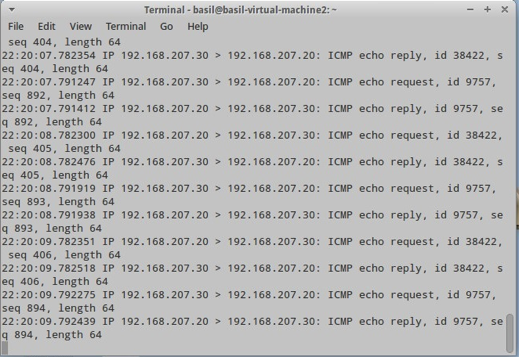
Testing Snort
The first test is fingerprinting the metaspoitable vm with nmap and snort detected this attempted successfully.
|
nmap –O 192.168.207.20 |
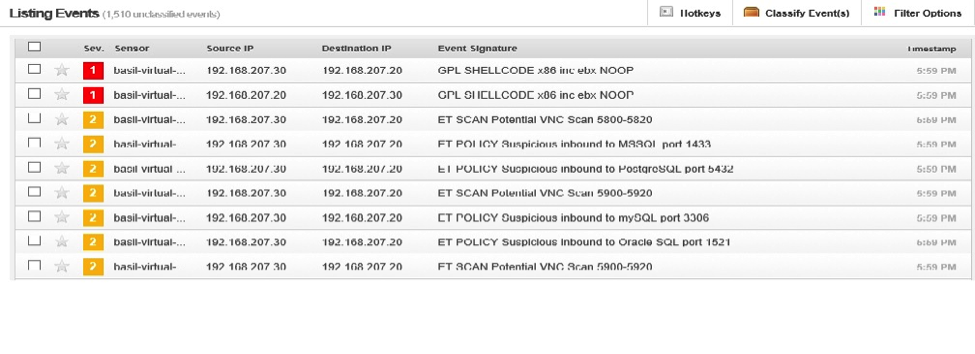
The second test is trying to brute forcing metaspoitable root password using hydra
|
hydra –l root –P passwords.txt 192.168.207.20 ftp |
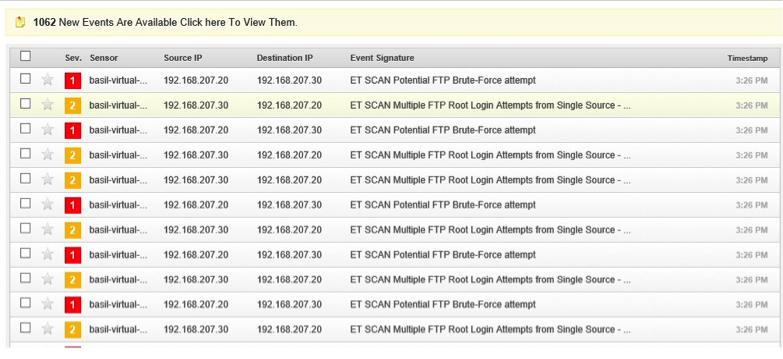
The third attempt was using metasploit to exploit metaspoitable:
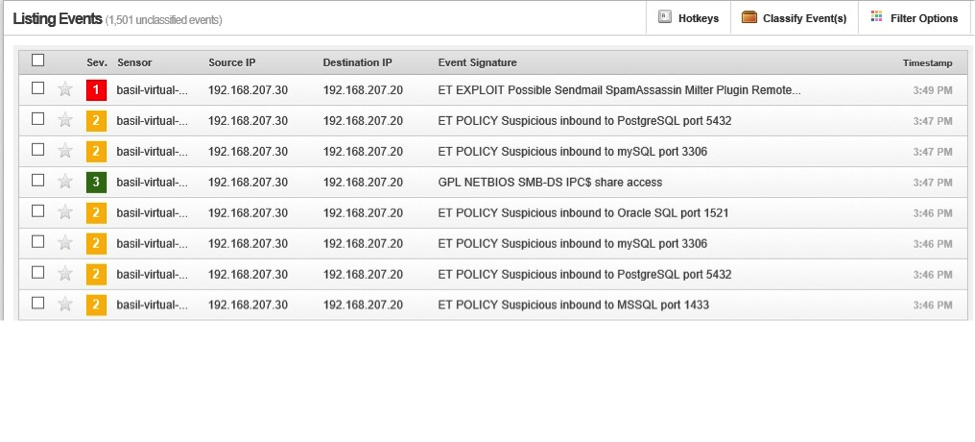
[1] https://isc.sans.edu/diary/Running+Snort+on+VMWare+ESXi/15899
[2] http://www.vmware.com/files/pdf/technology/cisco_vmware_virtualizing_the_datacenter.pdf
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
It's not very fit for monitoring the traffic being received by /many/ of the virtual machines in the environment though,
because you have to specify all these source ports to mirror manually; and therefore, update them when creating new VMs or changing the networking on a VM; easy to make an error here that results in something going unmonitored...
Therefore, the 3rd party commercial solutions that facilitate tapping the inter-VM traffic are worth considering.
Anonymous
Aug 19th 2013
1 decade ago
Infosanity covered an additional method of making your vSwitch a "vHub" previously: http://blog.infosanity.co.uk/2011/05/20/network-sniffing-in-vmware-esxi/
Anonymous
Aug 21st 2013
1 decade ago
source port IDs - these are the port ID listed against VM host servers and can be found from vDistibuted Switch --> 'Ports' tab?
destination port IDs - Is it the port ID assigned against Security Onion vm as Connectee?
Thanks in advance
Mil10
Anonymous
Apr 24th 2015
1 decade ago
Anonymous
Apr 24th 2015
1 decade ago
Anonymous
Jun 30th 2015
1 decade ago