Remote Diagnostics with PSR
Have you ever been in this situation? Someone calls you for help and tries to explain their problem. They do such a poor job of explaining what they are seeing that you aren’t even sure what OS they are using much less how to fix their problem. You wish you had some way of remotely seeing their desktop, but the user is incapable of following instructions required for you to remotely connect to and administer their machine. This is especially frustrating when you are in the identification or containment phase of an incident. Communications is an essential element of handling incidents effectively. When you are in a pinch, here is a new tool to add to your tool belt.
Microsoft Windows 7 has a tool called PSR (Problem Sequence Recorder). PSR will capture screen images, mouse clicks and some keyboard input and put in into a zip file that can be emailed back to you. The information is recorded in the sequence that the user sees it. You can see what they clicked and the order in which they clicked it. You can see what was on their screen and to a very limited extent what they typed. If you just run PSR.EXE it will bring up a GUI (graphical user interface). It is really easy to use. It has a start button and a stop button. When you click stop it prompts you to save a file. It produces a zip file containing the diagnostic information that the user can email to you (assuming that they have SOME connectivity).
While the GUI is pretty simple, PSR has whole bunch of useful CLI (Command Line Interface) options. Instead of having them run the GUI you could have them run the following at the start line (Explorer Run).
psr.exe /start /output \\?\%USERPROFILE%\Desktop\diag.zip /maxsc 100 /sc 1 /gui 0
That will start recording the user’s screens, keys and clicks. “/output <path>” defines the path and file that will contain the screen captures and the rest of the data. “/maxsc 100” changes the maximum number of screen captures it will capture from the default of 25 to 100. “/sc 1” turns on screen captures. Alternatively if you don’t want screen captures you can turn them off with “/sc 0”. “/gui 0” prevents the graphical user interface from displaying. User interactions will be recorded until you run the following:
psr.exe /stop
This will create a file called “diag.zip” on the user’s desktop where they can grab it and send it to you. When you open it up you will find a .mth file with lots of useful information. When you open it with Internet Explorer you will see something like this:
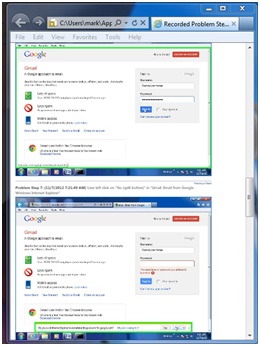
The green box shows where the user clicked on the screen. You can use this to see exactly what is on the user’s screen and make a more informed decision about how to respond.
I first started looking at PSR as a penetration testing tool. As you might imagine, the ability to capture screenshots, mouse clicks and keystrokes invisibly in the background is potentially useful to a penetration tester. However, I think it is more useful as an incident response tool. The screenshots can be useful to a penetration tester, but it doesn’t record all the keystrokes. You can include Event Tracing logs with the “/arcetl 1” option. Pauldotcom.com readers might know that I am very fond of ETW logs being used as a keylogger in a penetration test.
There are other interesting CLI options. For example, you can specify that you only want to record interactions with a specific process with the “/recordpid <process id#>” option. Here is the official list of CLI options from Microsoft's website. Examining the binary I notice there is also an undocumented “/uisavedir <directory>” option. For more information you can check out Microsoft's website at the link below. The list of command line options and examples from the Microsoft website are also below.
PSR Command Line Options
psr.exe [/start |/stop][/output <fullfilepath>] [/sc (0|1)] [/maxsc <value>]
[/sketch (0|1)] [/slides (0|1)] [/gui (0|1)]
[/arcetl (0|1)] [/arcxml (0|1)] [/arcmht (0|1)]
[/stopevent <eventname>] [/maxlogsize <value>] [/recordpid <pid>]
/start Start Recording. (Outputpath flag SHOULD be specified)
/stop Stop Recording.
/sc Capture screenshots for recorded steps.
/maxsc Maximum number of recent screen captures.
/maxlogsize Maximum log file size (in MB) before wrapping occurs.
/gui Display control GUI.
/arcetl Include raw ETW file in archive output.
/arcxml Include MHT file in archive output.
/recordpid Record all actions associated with given PID.
/sketch Sketch UI if no screenshot was saved.
/slides Create slide show HTML pages.
/output Store output of record session in given path.
/stopevent Event to signal after output files are generated.
PSR Usage Examples:
psr.exe
psr.exe /start /output fullfilepath.zip /sc1 /gui 0 /record <PID> /stopevent <eventname> /arcetl 1
psr.exe /start /output fullfilepath.xml /gui 0 /recordpid <PID> /stopevent <eventname>
psr.exe /start /output fullfilepath.xml /gui 0 /sc 1 /maxsc <number> /maxlogsize <value> /stopevent <eventname>
psr.exe /start /output %temp%\%computername%_PSR.zip /sc 1 /gui 1 /arcetl 1 /arcxml 1 /sketch 1 /slides 1
psr.exe /stop
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Follow me on Twitter @MarkBaggett
Mark Baggett


Comments