Phishing Kit Collecting Victim's IP Address
While reviewing my last findings today, I found a phishing email that delivered a classic .shtml file called "PROFORMA INVOICE.shtml". Right now, nothing special, emails like this one are widespread. When you open the file in a sandbox, it reveals a classic form:
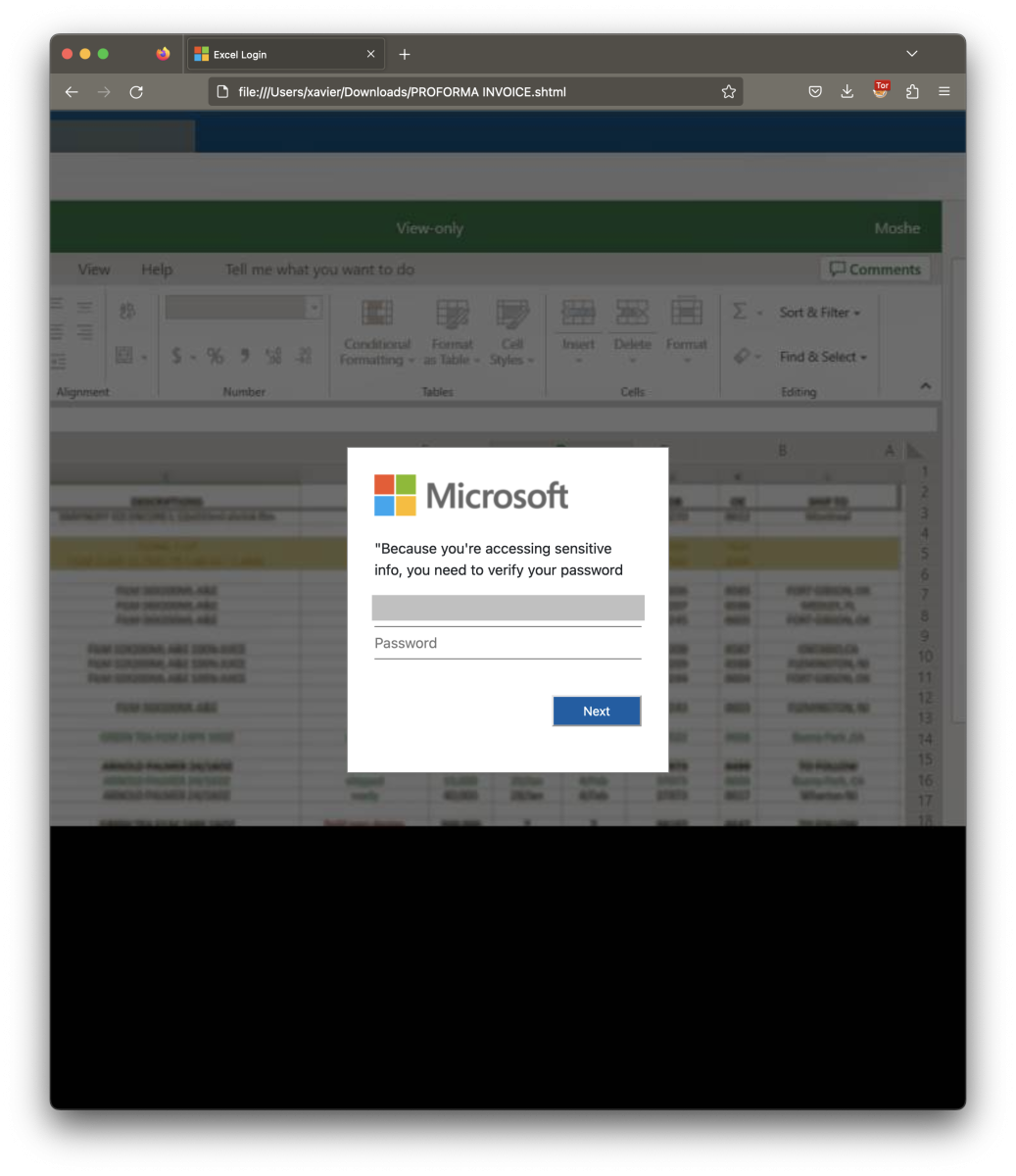
The potential victim is asked to enter his/her M365 credentials to reveal the Excel sheet (the email address has been obfuscated). I had a quick look at the HTML code and found something interesting in the HTTP form:
<input type="hidden" name="ip" id="hIP">
This means that a variable called "ip" will be submitted to the form simultaneously with the credentials. While checking deeper, there was some obfuscated JavaScript code below in the code:
<script>
const getip = async () => {
const payl = await postData("https://api.ipify.org/?format=json", {}, "GET");
document.getElementById("hIP").value = payl.ip;
return payl.ip;
}
getip();
async function postData(url = '', data = {}, method="POST") {
const response = await fetch(url, {
method,
mode: 'cors',
cache: 'no-cache',
headers: {
'Content-Type': 'application/json'
},
body: (method.toLowerCase() === "post") ? JSON.stringify(data) : null
});
return response.json(); // parses JSON response into native JavaScript objects
}
</script>
The line in red assigns the victim's public IP address to hIP that will be exfiltrated with the credentials.
Note that this piece of JavaScript is a perfect example of how to contact an API and extract data from the JSON response!
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
May 24th 2023
2 years ago