Peeking into Excel files
Since late 2014, malicious Office documents with macros appeared in the wild again. Malware authors don't always rely on VBA macros to execute their payload, exploits and feature abuse are part of their bag of tricks too.
Recently, I had a look at an Excel sample (MD5 656d7c4027ba0db106fb4d67859e2e35) with a formula that downloads and executes a COM scriptlet. This formula starts with Package, a string that can be found within the Workbook stream:
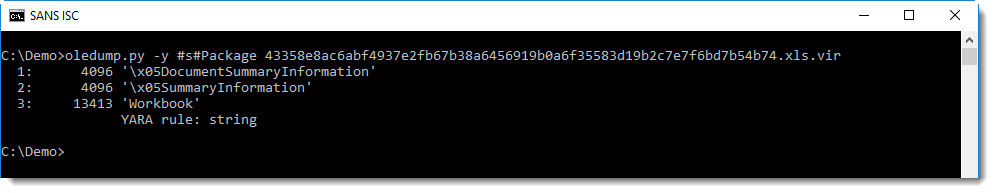
However, just the presence of string Package in this file is not a good indicator for a malicious document.
With my plugin for the BIFF file format plugin_biff (the original file format for Excel files, still used for the Workbook stream in OLE files), one can now search for strings inside BIFF records:
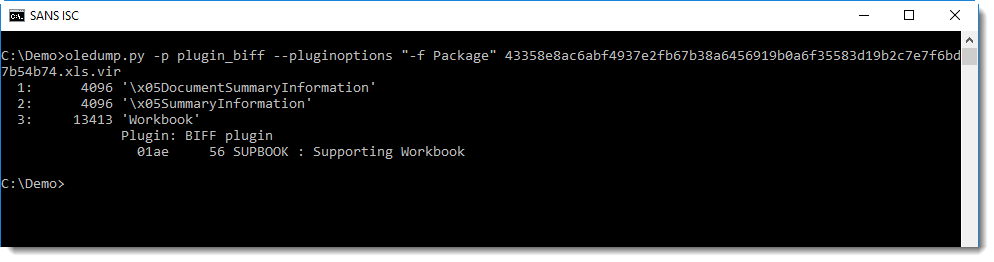
From this output, we know that string Package is present in BIFF record type 01AE, aka Supporting Workbook.
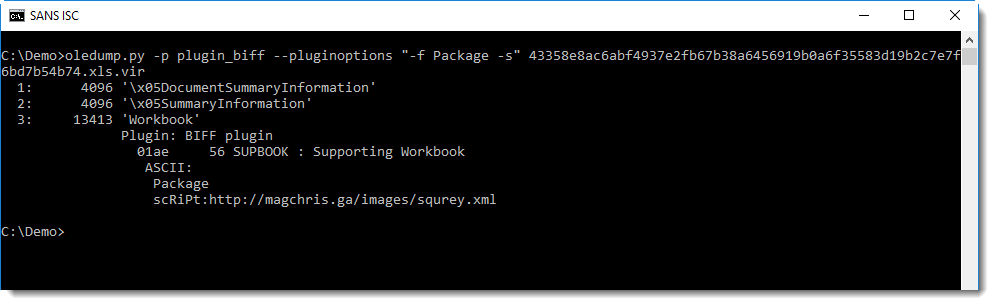
With plugin option -s, we can dump all the strings found in the data of this record, and thus extract the URL:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments