Oracle July 2014 CPU (patch bundle)
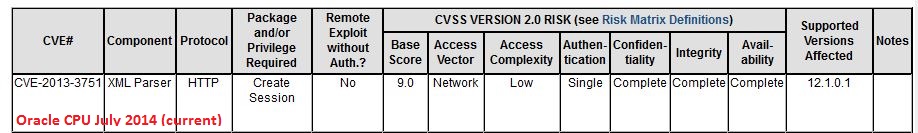
In addition to the Java vulnerabilities that I covered earlier, there is at least one more vulnerability that warrants attention. CVE-2013-3751, a problem in the XML parser of Oracle Database. Reading the description, I had a bit of a déjà-vu, also because of the CVE number from last year. And digging into past alerts, I found that, yes, this has indeed been patched before:
Looks like the Oracle 12 code was forked before the 11g patch went in, and nobody ported it over, so Oracle 12 remained exposed to the same bug until now. This speaks volumes about Oracle's software development life cycle and security processes... Dear Larry Ellison: how about writing a "Trustworthy Computing" memo for your staff, and then following through on it? I'm sure Bill Gates won't mind much if you simply copy his from 2002 and do a little search-and-replace.
For other untrustworthy computing features brought to you by this month's CPU patch bundle, see https://blogs.oracle.com/security/ and http://www.oracle.com/technetwork/topics/security/cpujul2014-1972956.html



Comments
Nice finding! We were irritated too because of the collision we've observed in our vulnerability database:
* http://www.scip.ch/en/?vuldb.67053
I wonder sometimes how "big companies" handle things that feel like even smaller companies should be able to address them with some level of accuracy/reliability.
Bye, Marc
Anonymous
Jul 16th 2014
1 decade ago