Ongoing scans for Geoserver
Looking at today's weblogs from our honeypot, I noticed one IP in particular, 83.97.73.89, scanning for "/geoserver" related URLs. This isn't new, and we have seen researchers, in particular Shadowserver, looking for similar URLs at least since the beginning of the year.
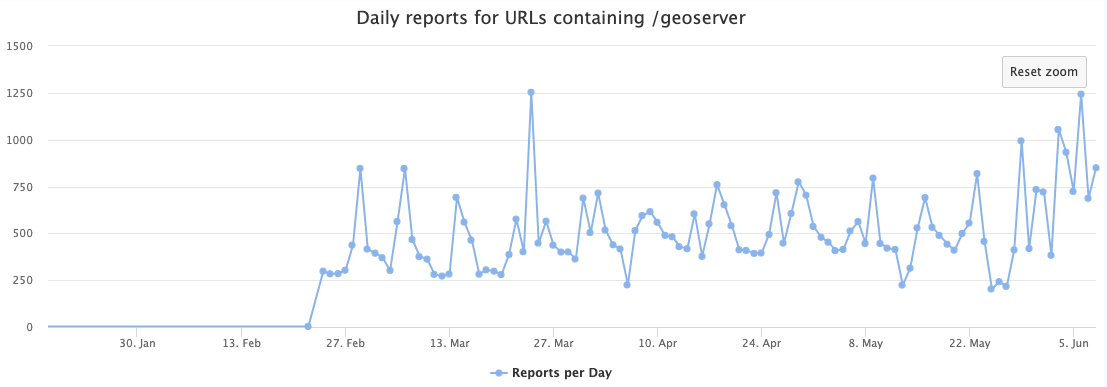
(See our web logs for current data)
Geoserver is an open-source web application to organize geospatial data [1]. Looking for vulnerabilities, one looks, in particular, interesting: CVE-2022-24816. A writeup from December provides details, including exploit code [2].
Right now, I am just in the process of setting up a full Geoserver honeypot to see what else we may be getting (I will update this diary if I see anything). But my best guess is that this is yet another scan for vulnerable web apps. The same source IP scans for several other common vulnerabilities. We usually see between 15 and 17 URLs "hit" by this particular source IP address.
[1] https://geoserver.org/
[2] https://www.synacktiv.com/en/publications/exploiting-cve-2022-24816-a-code-injection-in-the-jt-jiffle-extension-of-geoserver.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
XXXXX/access.log.0.gz:XXXXX.com.br 83.97.73.89 - - [29/May/2023:08:14:08 -0300] "GET /geoserver HTTP/1.1" 302 0
bundled with some usual PHP flaws:
POST /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
GET /solr/admin/info/system?wt=json
GET /index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=md5&vars[1][]=HelloThinkPHP21
GET /?a=fetch&content=<php>die(@md5(HelloThinkCMF))</php>
GET /?XDEBUG_SESSION_START=phpstorm
GET /console/
POST /Autodiscover/Autodiscover.xml
GET /_ignition/execute-solution
POST /bin/sh
Clausewitz4.0
Jun 8th 2023
2 years ago