Ongoing Scans Below the Radar
With the rise of botnets like Mirai[1], we have seen a huge increase of port scans to find new open ports like port 2323 or later port 6789. If the classic port 80 and port 23 remain the most scanned ports, we see new trends almost every week. By the way, thank you to our readers who also report this to the ISC!
This is the traffic detected by my current honeypots:
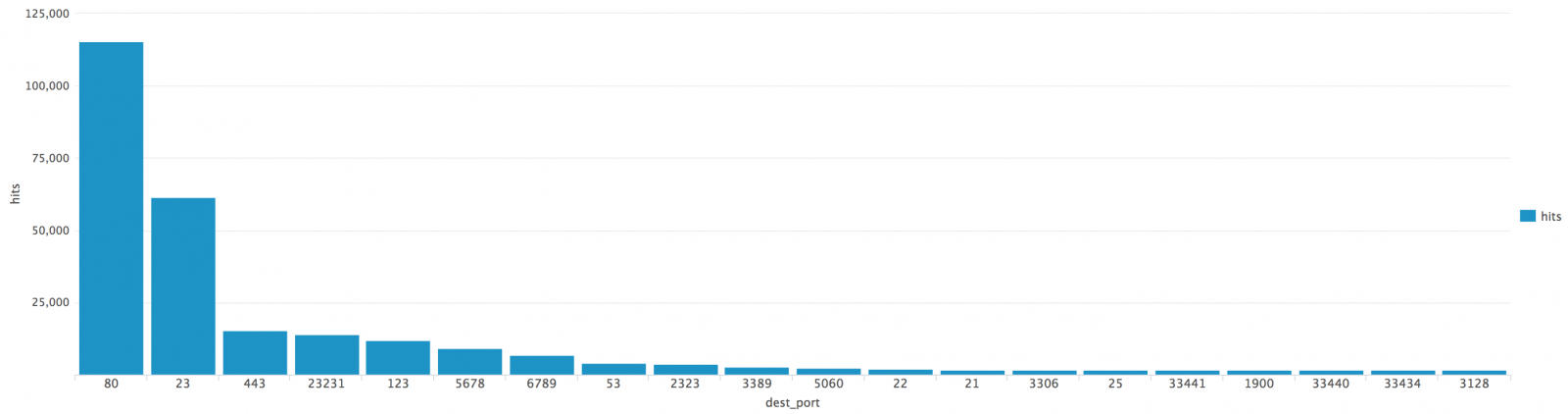
The honeypots accept connections on ports 80 and 443 and just log attempts performed on other ports.
A few days ago, I deployed a new honeypot that listens to many more ports:
- 21 (FTP)
- 22 (SSH)
- 69 (TFTP)
- 80 (HTTP)
- 123 (NTP)
- 161 (SNMP)
- 445 (SMB)
- 1433 (MSSQL)
- 3389 (RDP)
- 5060 (SIP)
- 5900 (VNC)
- 8080 (Proxy)
For each protocol, the honeypot collects interesting information related to the application (user, password, commands, filename, path, ...) It has been deployed on a brand new system that was unknown before. Here are some results after one week online:
| Protocol | Hits |
| 21 | 1 |
| 3389 | 2 |
| 80 | 3 |
| 69 | 9 |
| 161 | 35 |
| 123 | 82 |
| 5060 | 234 |
| 3306 | 3097 |
| 1433 | 4897 |
| 23 | 41857 |
As you can see databases seems to remain a nice target. The MSSQL scans revealed the following users:
| Chred1433 |
| IIS |
| KISAdmin |
| kisadmin |
| sa |
| su |
| vice |
With MySQL, the targeted users were:
| mysql |
| root |
| server |
The NTP scanners issued the "monlist" command to search for NTP servers vulnerable to amplification attacks.
As you can see, there are bots scanning for many protocols. We need to keep an eye on what is happening below the radar. I'm planning to listen to more ports in the coming days. I wish you already a wonderful and safe year 2017!
[1] https://isc.sans.edu/forums/diary/What+is+happening+on+2323TCP/21563
[2] https://www.us-cert.gov/ncas/alerts/TA14-013A
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Dec 31st 2016
9 years ago
You told about a new multi-listening honeypot deployed to help investigating for bots. Could you please provide a description of the honeypot used and how to deploy such one ? It could maybe be a nice idea to aggregate the collected data of many of the same honeypot you use ?
Many thanks in advance,
Best regards.
Anonymous
Jan 2nd 2017
9 years ago
Devices have a random (?) high port open, which sends directly malware:
https://www.virustotal.com/de/file/cd902176bb1ad799f422703b67f021e16922ac9f990f30e9ec032ae03a5602ff/analysis/1482934109/
Anonymous
Jan 2nd 2017
9 years ago
Here is what I see for the last 24 hours.
Port Summary
Port Packets Sources Targets Service Name
23 192 183 1 telnet
23231 66 66 1
6789 28 28 1 ibm-db2-admin dB2 Web Control Center
2222 36 21 1 AMD [trojan] Rootshell left by AMD exploit
60205 16 16 1
5358 9 9 1
2323 8 8 1 3d-nfsd 3d-nfsd
5060 9 7 1 sip SIP
3389 4 3 1 ms-term-services MS Terminal Services
3391 2 2 1 savant SAVANT
53 2 2 1 domain Domain Name Server
3306 2 2 1 mysql MySQL
5900 2 2 1 vnc Virtual Network Computer
62014 2 2 1
123 2 2 1 NetController [trojan] Net Controller
161 2 2 1 snmp SNMP
7547 2 2 1 TR069 Router Remote Admin
0 2 2 1
8000 3 2 1 irdmi iRDMI
21 1 1 1 ftp File Transfer [Control]
Anonymous
Jan 2nd 2017
9 years ago
Anonymous
Jan 2nd 2017
9 years ago
I'm preparing a standard setup that I'll share later + integration into Splunk.
Anonymous
Jan 3rd 2017
9 years ago