New tool: le-hex-to-ip.py
So, this week it is my privilege to be TA-ing for Taz Wake for the beta run of his new class FOR577: Linux Incident Response and Threat Hunting. We were looking in the linux /proc filesystem and were noticing in the /proc/<pid>/net/{tcp/udp/icmp/...} that the IP addresses were listed in hex, but little-endian.
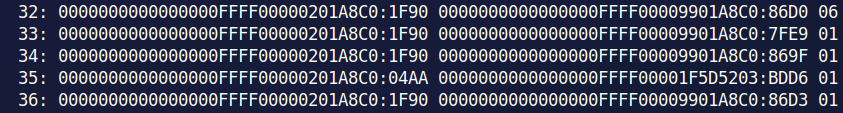
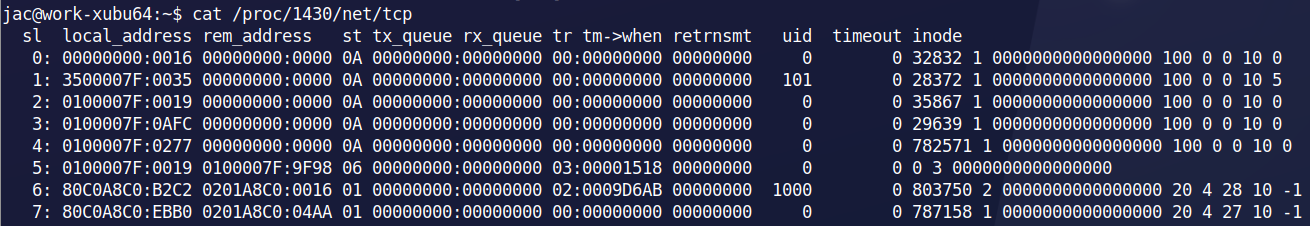 I immediately remembered Didier's Handler's Diary from last week about the IPs in the event logs that were in decimal and little endian. I tried the last 2/3 of his recipe and it worked, but what I really wanted was a command-line way to do it. My first thought was to see if chepy would fit the bill. Unfortunately, it doesn't do the Change IP Format from CyberChef. So, I figured, I'd write something myself. Then I looked into the /proc/<pid>/net/tcp6 and saw that those addresses were also little-endian on 32-bit boundaries.
I immediately remembered Didier's Handler's Diary from last week about the IPs in the event logs that were in decimal and little endian. I tried the last 2/3 of his recipe and it worked, but what I really wanted was a command-line way to do it. My first thought was to see if chepy would fit the bill. Unfortunately, it doesn't do the Change IP Format from CyberChef. So, I figured, I'd write something myself. Then I looked into the /proc/<pid>/net/tcp6 and saw that those addresses were also little-endian on 32-bit boundaries.

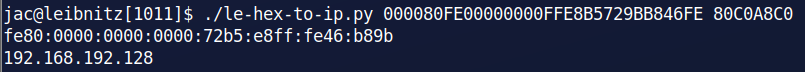
So, I wrote a python script that could handle both instances. I've added it to my github repo. I named the script le-hex-to-ip.py and it takes the 8 character (IPv4) or 32 character (IPv6) hex strings (1 or more) and translates them back into human-readable IPv4 or IPv6 addresses. It isn't anything particularly special, but I figured I would share it. If anyone has thoughts on improvements, please let me know. Below you can see the script in action.
References:
[1] https://www.sans.org/cyber-security-courses/linux-threat-hunting-incident-response/
[2] https://isc.sans.edu/diary/IPv4+Addresses+in+Little+Endian+Decimal+Format/30256/
[3] https://github.com/clausing/scripts.git
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments